Bitdefender Engine FAQs
We have included three new default Bitdefender polices and incorporated a Migration Tool to create Bitdefender versions of VIPRE policies.
Bitdefender partners with Microsoft to create smart exclusions based on Microsoft recommendations. These smart exclusions are automatically included in the background for each View and Configure Managed Antivirus Protection Policies (so do not appear in the Protection Policy: Exclusions list) and are applied by the Bitdefender Engine depending on the scanned device's Operating System.
As such when using the Bitdefender engine there is no longer a requirement to create separateView and Configure Managed Antivirus Protection Policiesjust to scan different Operating System types, unless these policies are to include custom exclusions or settings that only apply to specific Operating Systems.
Managed Antivirus (Bitdefender) is available for both Windows and Mac computers. They use common policies and the Operating System governs which policies are applied. Managed Antivirussetup is exactly the same for both Windows and Mac computers.
Unfortunately the icon cannot be branded as it is burned into the agent by Bitdefender during their build process. Only the Company Name, Product Name, Website, Email, and URL are configurable in the View and Configure Managed Antivirus Protection Policies. Please be aware that if N/A is entered for any of the settings this will appear in the Agent's About Managed Antivirus dialog.
The Bitdefender engine edition of CART utilizes OPSWAT's AppRemover to detect any currently installed AntiVirus or AntiSpyware products on the device. Depending on the discovered solution CART can either uninstall the product (where it is marked as Yes for ARSupported) or simply report the product as detected (No for ARSupported).
Further information on the products supported by OPSWAT are available in the section Bitdefender Engine - Supported Products for Removal
Please be aware that automatic CART removal is disabled by default in the Protection Policy - Installation Settings. Where CART is disabled in the Protection Policy it may still be used to remove a detected product via the Remove links or force installation links and subsequently install Managed Antivirus.
Regarding MalwareBytes, there is an exception in place to the list provided by OSWAT so it is not removed.
The data in the Managed Antivirus (Bitdefender) displays for one full calendar year.
The first troubleshooting step is to double-check that the entered location is correct. If this all appears to be okay, the next step is to check whether case sensitivity was enabled for this folder.
Case sensitivity was introduced in the Windows 10 April 2018 Update (version 1803) and is configured on a per-folder basis. Where enabled for a folder, the entered exclusion location must precisely match the file and folder case. Otherwise Managed Antivirus is unable to exclude this folder or file and it will be scanned. Further information on this setting is available from Windows 10: Case sensitive file and folder names.
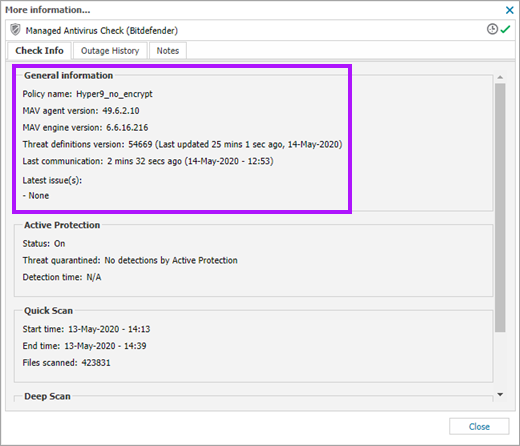
The Bitdefender engine can update independently of the Advanced Monitoring Agent upgrade cycle. To view the version of the Bitdefender engine installed on a device; select the target device on the All Devices view, navigate to the Managed Antivirus Check in the South-pane Checks tab, then click the check's More information link to open its dialog. The current MAV agent version is displayed under the General information section of the Check Info tab
The only way to avoid any potential issues with System Restore is to run it from Safe Mode or uninstall the Antivirus product before restoring, although on some systems (Windows 8) System Restore does work when Active Protection is disabled. Bitdefender have created the Knowledge Base article How do I use System Restore in Windows? that covers the various options.
It is not possible to install Managed Antivirus to a custom location.
There is no option to exclude based on the file size.
This error is returned where the endpoint cannot connect to Bitdefender's Global Protective Network intelligence cloud. To alleviate this error please ensure the device, and Windows - Designate a Site Concentrator server if configured on the device's Site, can reach the following Managed Antivirus URLs.
Bitdefender provided the following response to this question which encompasses not only the remediation action to take one CrytoLocker is detected, but also steps to prevent the device becoming infected in the first place.
First we would like to point out that CryptoLocker is not unique at all in how it propagates. A lot of malware has been distributed via attachments for a dozen years, and certain torrents have been seeding malware for ages. So we're certainly not talking about a new or unique threat here.
Obviously the infected email should be first addressed at the mail server, meaning the mail server should scan received email for malware/phishing and the end user should not receive the infected e-mail in the first place - perhaps using a service like Mail Assure.
However, in case the mail server protection fails, or is not available for some reason, the N-sight RMM solution still protects the end user through multiple layers:
- The first layer is Web Protection, available from the N-sight RMM All Devices view. The rest of the items mentioned are specific to the Managed Antivirus Bitdefender engine offering .
- The second layer is Active Protection. Before the executable file is started, it has to be written on disk and run. In case of attachment when a user clicks on a file, it does not start "directly from Outlook" - it is in fact written into the temporary directory and starts from there, either directly or passed as argument to an appropriate program such as Microsoft Word. The on-access module would be triggered when a file is opened (either because the system wants to memory-map the executable image into memory, or because Microsoft Word wants to read the document). Once triggered, the on-access module scans the file for malware with our standard engine, and if any malware is found, the file is blocked, meaning it cannot be started, or Microsoft Word cannot load the document, therefore preventing an infection.
- In a rare case when a malware threat is completely new or was modified to pass the engine, and a new detection isn't available yet, the file would be scanned and allowed to start. In this case the Behavioral Scanning gets into the game, analyzing the running program behavior and comparing it with the set of heuristic rules of what the file is allowed to do. If the file's behavior is found malicious, the process is killed automatically, even though it was not detected by the engine.
So as you see, we're using multiple layer protection even on the endpoint itself. And while no security solution guarantees 100% protection, Bitdefender does provide a much better detection level comparing to other vendors, as confirmed by the latest AV-Test results Bitdefender averages a 100% detection rate on 0-day malware collections, with the industry average 98%.
Please note that AV-Test is a trusted third-party organization with good reputation, it is trusted by many security professionals and which is not affiliated with Bitdefender or any other anti-malware vendor.
Please be aware that we are not responsible for the content of external sites.
What do you want to do?
- Review the Managed Antivirus Quick Start Guide
- View Managed Antivirus URLs
- Enable Managed Antivirus on individual servers and workstations or on all servers and workstations at a client or site
- Automatically remove installed Antivirus products
- View and Configure Managed Antivirus Protection Policies. Includes scan schedules, remediation action (default threat action), end-user interaction
- Look at actions for information on the end user authorization required on macOS High Sierra (10.13) and later
- Manage Quarantined items
- Start and Cancel on-demand scans
- Remotely update Managed Antivirus Threat Definitions
- Analyze Managed Antivirus Reports, these cover the provided level of protection