Vulnerability Management (New)
The Vulnerability Management view allows you to monitor assets efficiently using filters, searches, and actions. Powered by our new Modern Agent, Vulnerability Management helps identify patterns, trends, and anomalies, uncovering opportunities, risks, and areas for improvement.
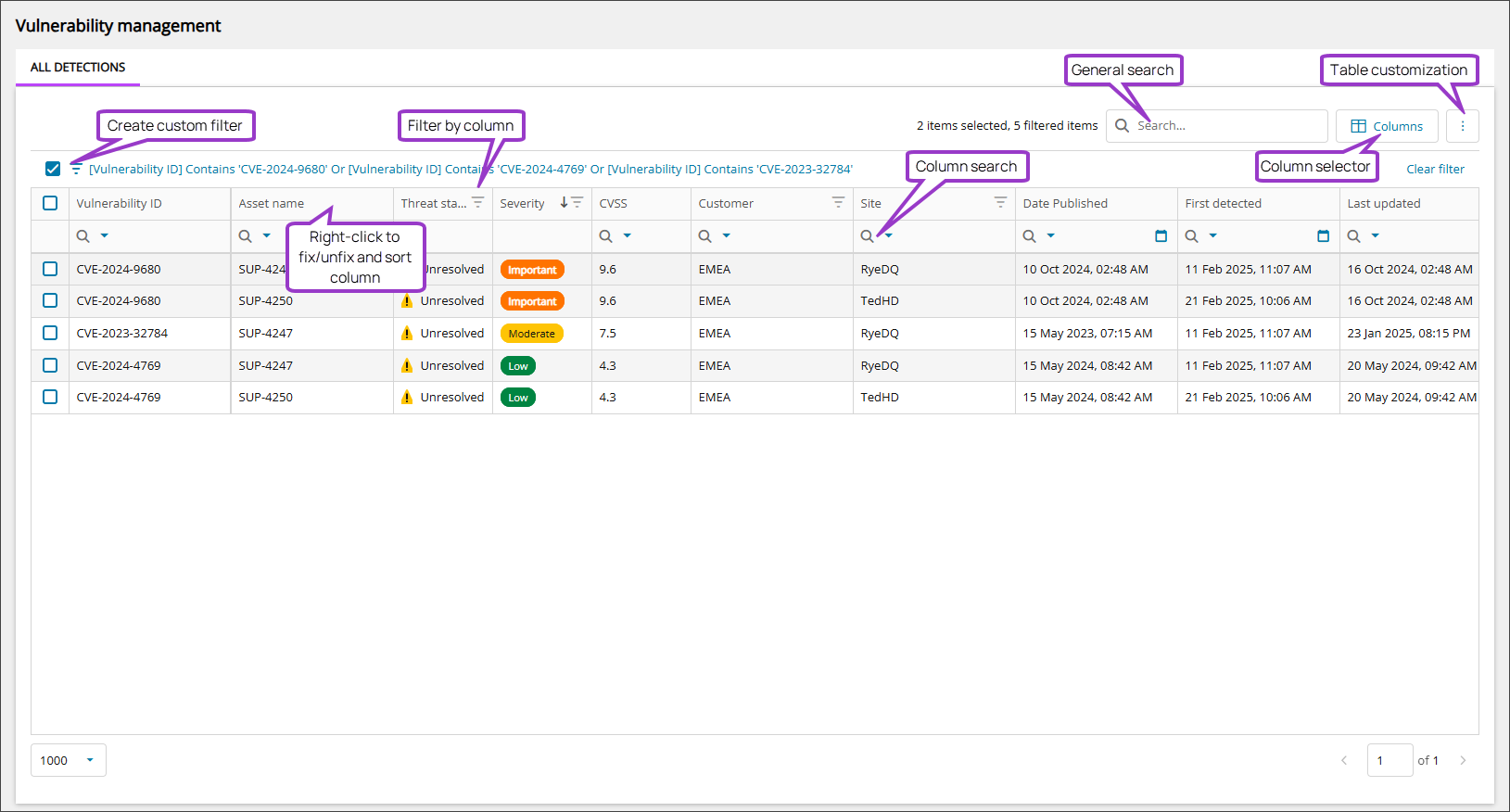
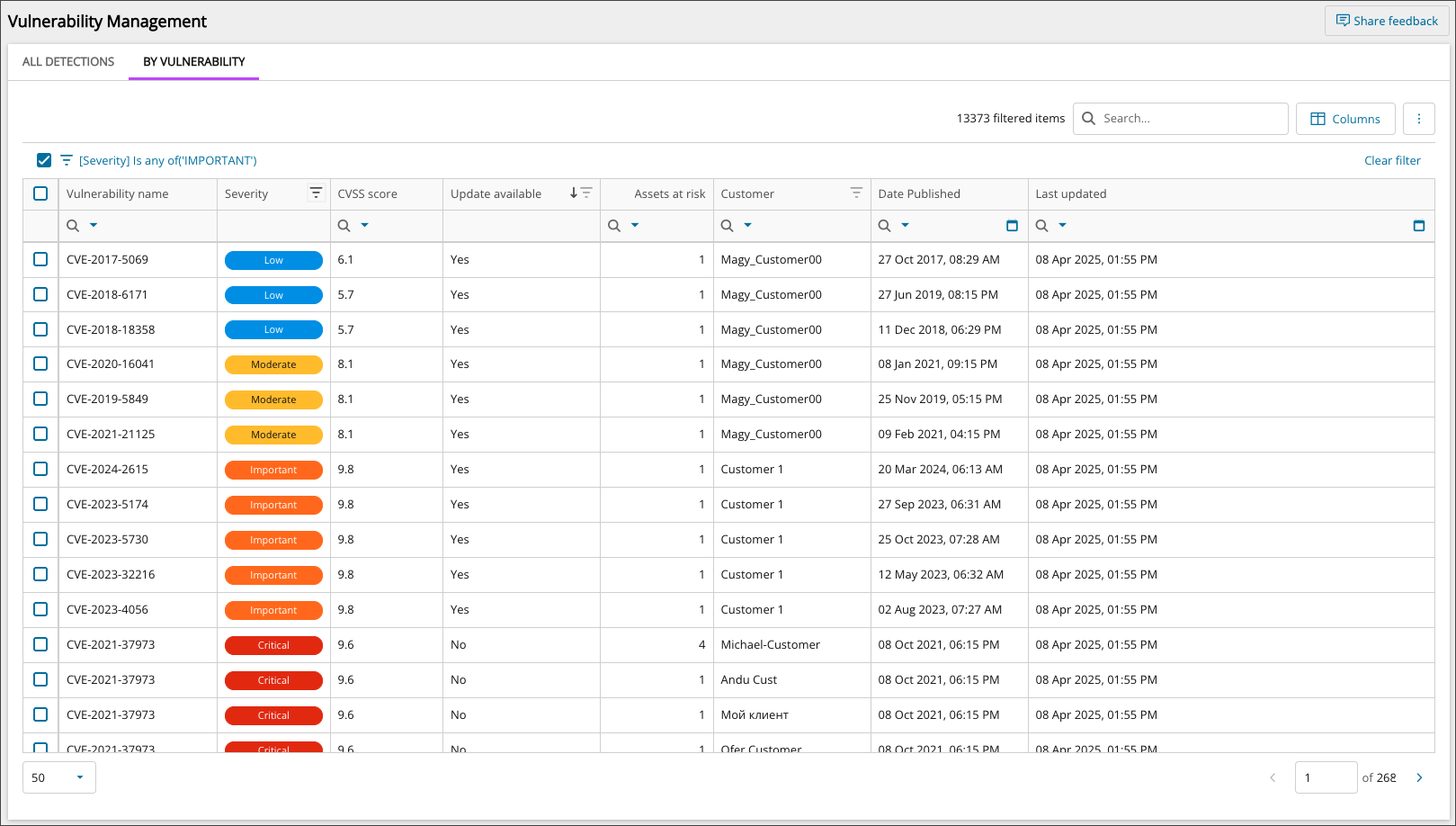
Vulnerability Management provides three distinct tabbed views;
- All Detections displays all the vulnerability detections individually.
- By Vulnerability groups the vulnerabilities displayed, making it easier to see numbers of devices effected by each vulnerability.
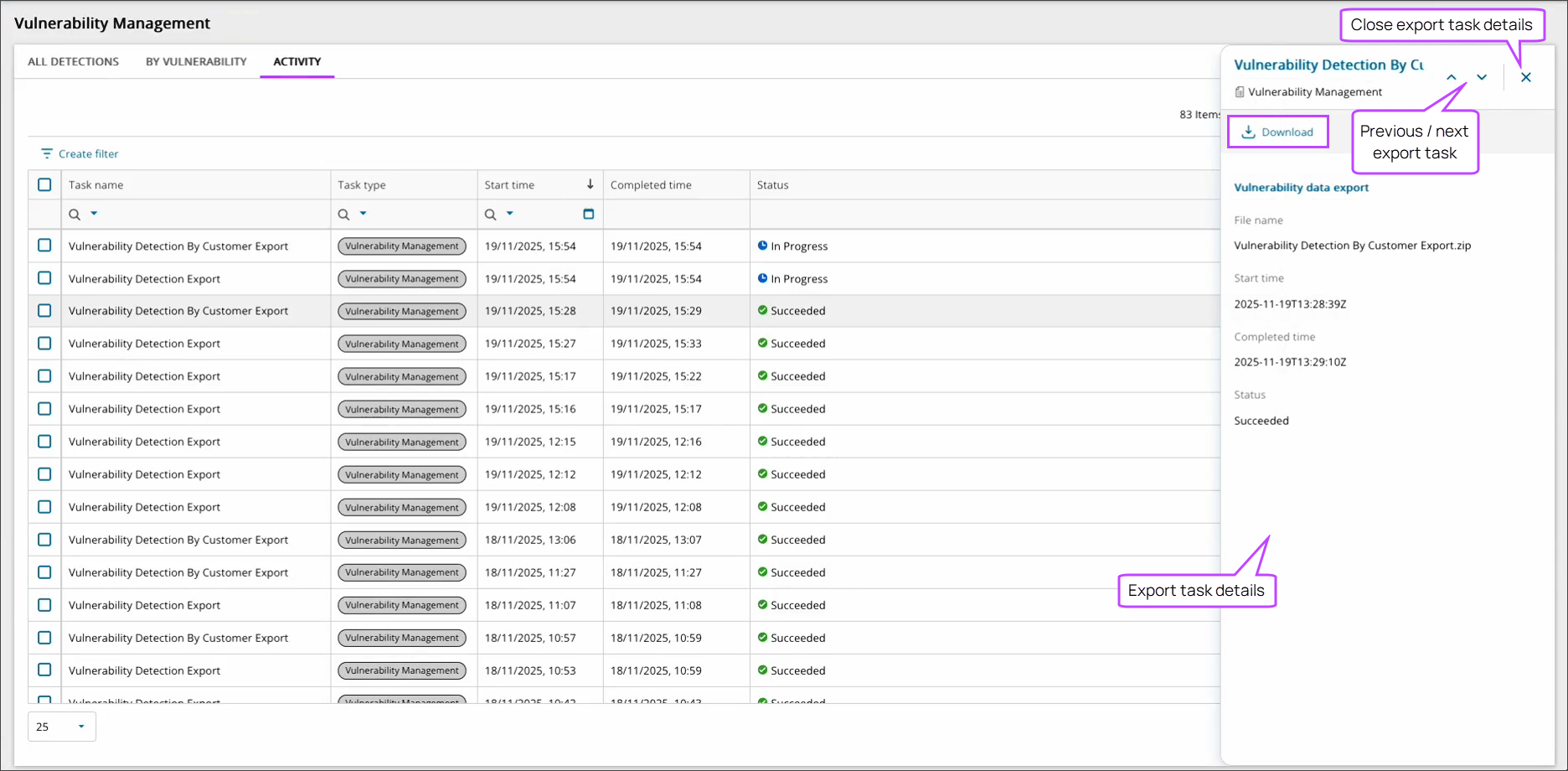
- Activity details the in progress and historical large exports (10k+ rows) statuses.
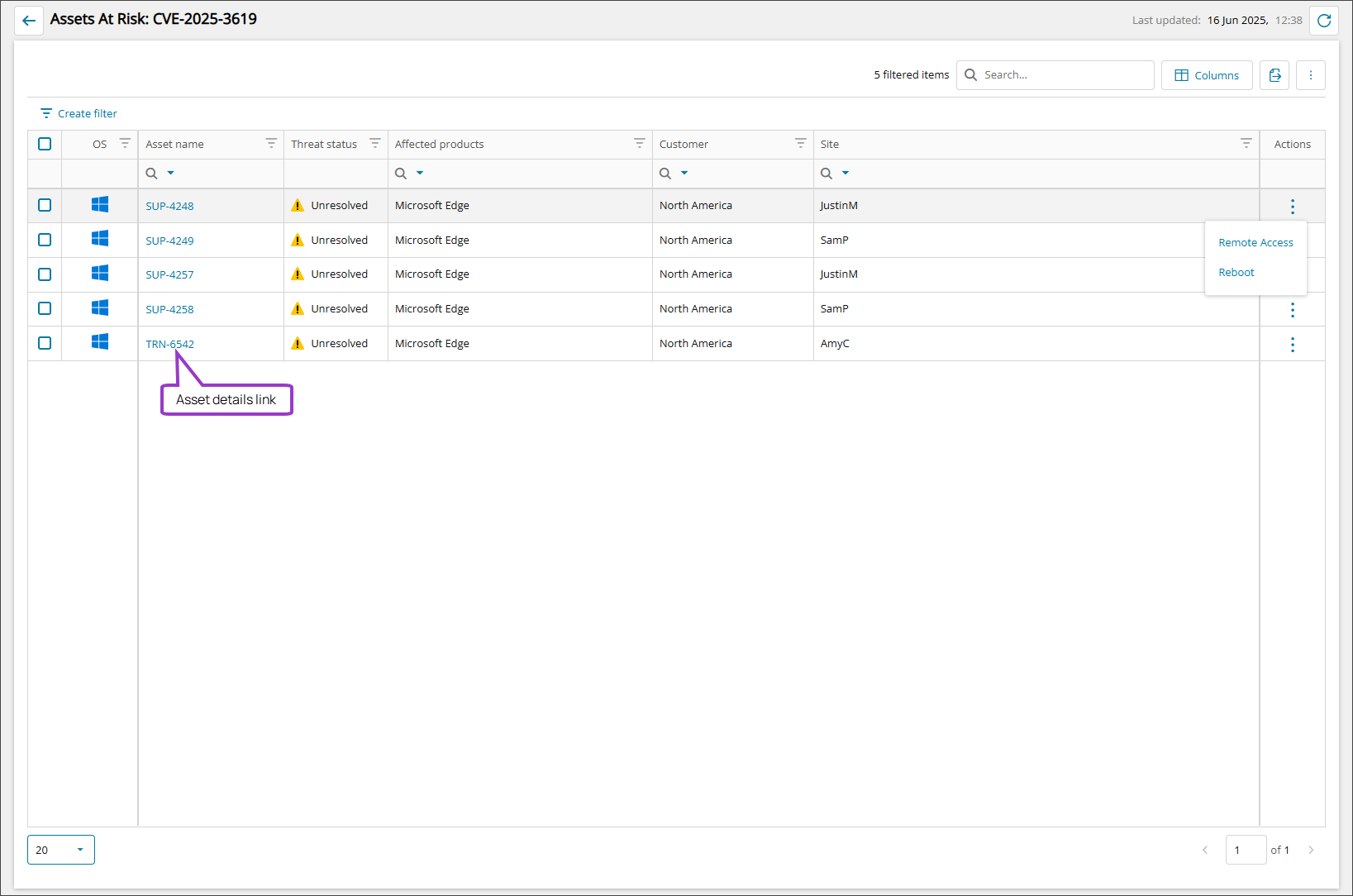
Each vulnerability also shows how many assets are at risk and also provides a list of those assets in the Assets at risk view. You can also launch directly into the All devices view for each asset from here as well.
- Is the application still supported by the vendor?
- Is Patch Management configured as you expect it to be?
In the event an application is no longer supported by the vendor, there will be no more available patches for it, which means Patch Management cannot update it.
Assuming the application is still supported by the vendor, Patch Management should be patching as updates become available, assuming your configured Protection Policy is set to do so.
N-able recommends that, wherever possible, the application be uninstalled and an alternative application used in its place.
Vulnerability Management scans
Endpoints run a software inventory scan at 06:00, 12:00, 18:00, and 24:00 as per endpoint local time.
- If there is a change from the prior completed scan, the update is uploaded to our cloud and processed
- If nothing has changed, no upload occurs
- At least one upload per day will occur, regardless of change
Updates to the software inventory sent to the cloud are processed as they arrive, and will queued and processed before they update the state of the vulnerability, This queue can stack up and take up to 4 hours to process from start to finish.
A given vulnerability entry will remain in the database for up to 90 days since the last change to its status.
If a software version with a vulnerability is detected and then that software is no longer detected, the vulnerability shifts from unresolved to resolved.
- If a software version that has that same vulnerability is then later detected, the vulnerability will then move back to an unresolved status.
- We do not currently track vulnerability change causes, only that a vulnerable software was detected at one point in time and that when we inventoried again, that vulnerable software was no longer present.
If a scan is missed on a device because it is powered off or otherwise non-operational, the device will be scanned at the next scheduled scan time.
Access the Vulnerability Management view
- Select Vulnerabilities in the Left navigation.
Actions available from the Vulnerability Management view
After you identify the vulnerability issues you are looking for, you can take action directly from the Vulnerability Management view with the following tasks:
- View vulnerability details
- Open asset details in the All Devices view from Vulnerability Management
- View Assets at risk
- Export Vulnerability Management data to CSV
Viewable data fields via All Detections
| Column name | Description |
|---|---|
| Vulnerability ID | The CVE code for the vulnerability. |
| Asset Name | The unique identifier assigned to an asset, enabling efficient tracking, management, and troubleshooting. You can update this information within the classic platform (N-central or N-sight). |
| CVSS (Common Vulnerability Scoring System) Score | Numerical score as per CVSS for the vulnerability. |
| Severity | Critical
Important Moderate Low |
| Threat Status | Resolved or Unresolved. |
| Affected Products | Product name affected by the vulnerability. |
| Customer | Name of the client the asset belongs to. |
| Site | The name of the client site where the device resides. |
| Date Published | The date the vulnerability CVE was published. |
| First detected | Initial detection date for the vulnerability on the device. |
| Last updated | The most recent date of the previous vulnerability information update. |
| Update available | Yes or No. Indicates if an update that will resolve the vulnerability is available. |
| Risk Score | This score gives an overall view of how severe the vulnerability is by considering factors like how well-known the CVE is, the risk of it being compromised, and its life cycle. |
| OS Role |
Asset OS is either a |
| Has exploit |
|
| CISA KEV | Yes or No. Indicates if the vulnerability is listed in the CISA (Cybersecurity and Infrastructure Security Agency) KEV (Known Exploited Vulnerabilities) Catalog. |
| Has ransomeware | Yes or No. Indicates if the vulnerability is known to be used in ransomware campaigns. |
| CWEs | The Common Weakness Enumeration (CWE) ID. Common software and hardware weakness types that could have security ramifications. A weakness is a condition in a software, firmware, hardware, or service component that, under certain circumstances, could contribute to the introduction of vulnerabilities. A CWE is assigned an ID in the form CWE-<ID>, where the <ID> is simply a unique number chosen at the time of assignment (e.g., “CWE-798”). The CWE-ID is followed by a descriptive name for the weakness (e.g., “CWE-798: Use of Hard-coded Credentials”). See the CWE website for full details. |
Viewable data fields via By Vulnerability
| Column name | Description |
|---|---|
| Vulnerability ID | The CVE code for the vulnerability. |
| Severity | Critical
Important Moderate Low |
| CVSS (Common Vulnerability Scoring System) Score | Numerical score as per CVSS for the vulnerability. |
| Update available | Yes or No. Indicates if an update that will resolve the vulnerability is available. |
| Asset at risk | The unique identifier assigned to an asset, enabling efficient tracking, management, and troubleshooting. You can update this information within the classic platform (N-central or N-sight). |
| Customer | Name of the client the asset belongs to. |
| Date Published | The date the vulnerability CVE was published. |
| Last updated | The most recent date of the previous vulnerability information update. |
| Risk Score | This score gives an overall view of how severe the vulnerability is by considering factors like how well-known the CVE is, the risk of it being compromised, and its life cycle. |
| Has exploit | Yes or No. Indicates if the vulnerability has a known exploit. |
| CISA KEV | Yes or No. Indicates if the vulnerability is listed in the CISA (Cybersecurity and Infrastructure Security Agency) KEV (Known Exploited Vulnerabilities) Catalog. |
| Has ransomeware | Yes or No. Indicates if the vulnerability is known to be used in ransomware campaigns. |
| CWEs | This column displays the Common Weakness Enumeration (CWE) ID. Common software and hardware weakness types that could have security ramifications. A “weakness” is a condition in a software, firmware, hardware, or service component that, under certain circumstances, could contribute to the introduction of vulnerabilities. A CWE is assigned an ID in the form CWE-<ID>, where the <ID> is simply a unique number chosen at the time of assignment (e.g., “CWE-798”). The CWE-ID is followed by a descriptive name for the weakness (e.g., “CWE-798: Use of Hard-coded Credentials”). See the CWE website for full details. |
Ecoverse functions
All our new Ecoverse views have common functionality, such as filtering and sorting the presented data, performing searches, and exporting. For full details and instructions, please select a link below.
- Ecoverse views
- Filter and sort Ecoverse views
- Search Ecoverse views
- Create custom filters in Ecoverse views
- Custom filters examples
- Customize your Ecoverse views
- Save Ecoverse views
- Export data from Ecoverse views
As Ecoverse views are developed and released, they may not initially contain full Ecoverse functionality.
Related articles
- System and user requirements for Vulnerability Management
- View Assets at risk
- Start a Remote access session from the Assets at risk view
- Reboot an asset from the Assets at risk view
- View vulnerability details
- Open asset details in the All Devices view from Vulnerability Management
- Export Vulnerability Management data to CSV
- Discover Assets view (New)
- Read more about the Modern Agent.