Risk Intelligence Custom Policies
Each aspect of Risk Intelligence, from the scans to run to their schedule, is controlled through Risk Intelligence policies.
Default policies are available for Laptops, Desktops and Servers with the ability to manage your own custom policies (as well as edit the defaults). When creating a new policy, the policy settings and scan configurations are automatically populated from the selected "Base Policy On" policy. When in the policy dialog, click Customize Scans to go to the Custom Scans section.
For a list of all of the policies currently in use across your policy supporting features, please refer to the Feature Policy Report.
This section covers how to:
Create a Custom Policy

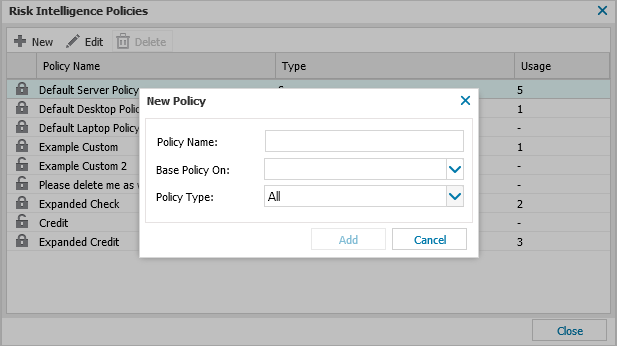
- In the All Devices view, go to Settings > Risk Intelligence > Policy.
- Click New to create a custom policy.
- Enter the Policy Name for identification.
- Select an existing policy to act as a template from the Base Policy On drop-down - or leave blank to set all scans as Do not Run (disabled).
- Choose the Policy Type: All, Server, Desktop or Laptop.
- Select a policy or General in the All Policy dialog.
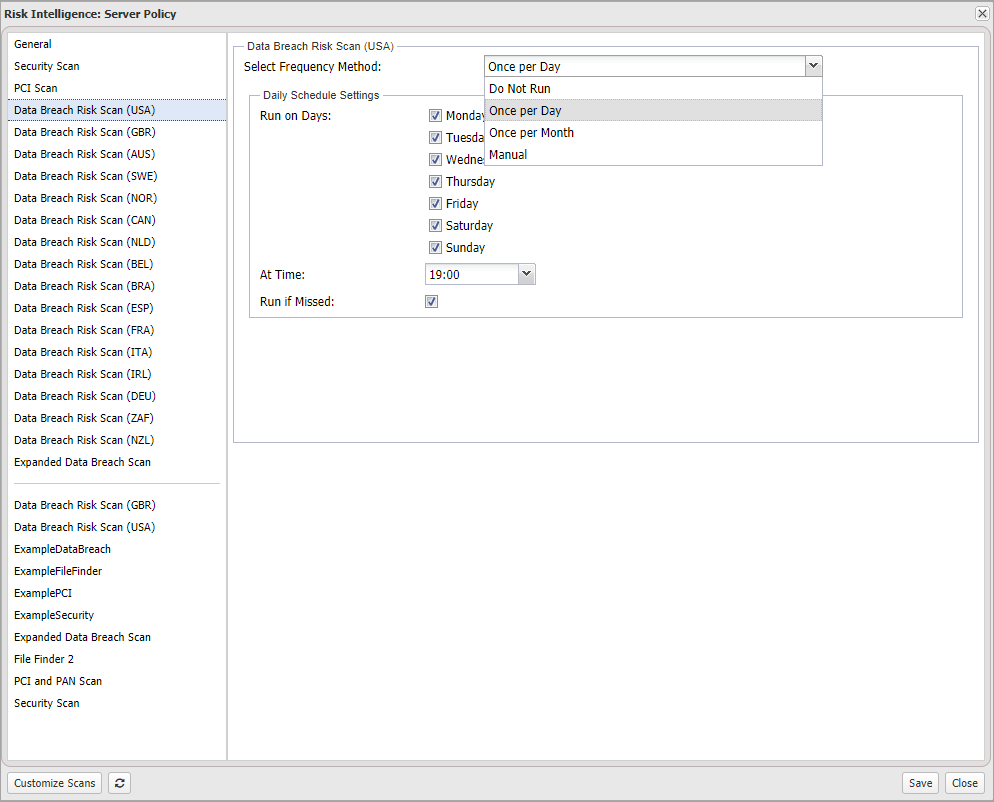
- To enable a scan, change its Select Frequency Method setting to Once per Day, Once per Month or Manual and configure the scan (where required). Change this setting to "Do Not Run" to disable a scan.
- Click Save to apply
| Section | Description | |
|---|---|---|
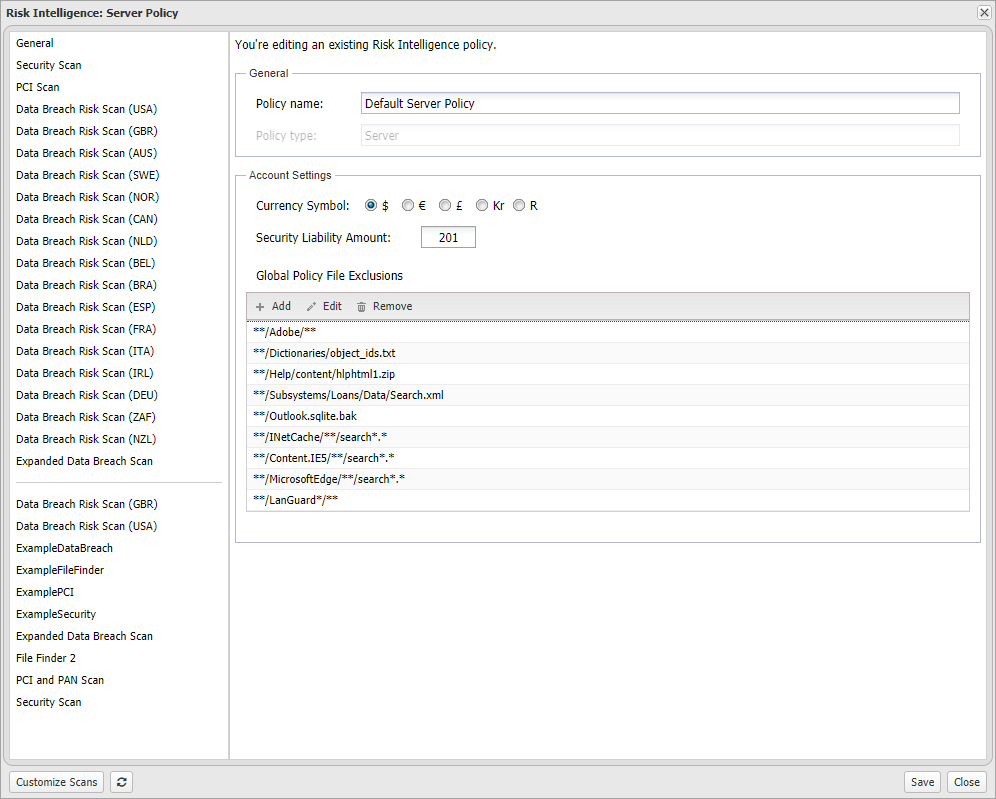
| General |
Contains the Policy type and editable Policy name Set the account wide Currency Symbol and Security Liability Amount as well as any Global Policy File Exclusions |
|
| Policies | Security Scan | Retrieves vulnerability information from the computer that may expose the Operating System and installed application to security risks |
| PCI Scan | Search for risks with internal Payment Credit Industry compliance violations | |
| Data Breach Risk Scan (Country) |
A security scan that searches for Credit Card Numbers, dates of birth, government-issued identification, and financial account numbers.
There is not a global standard for Personally Identifiable Information (including government issues identification) so we include country-specific versions of this scan to search for and retrieve details in that country’s format. AUS, BEL, BRA, CAN, DEU, ESP, FRA, GBR, IRL, ITA, NLD, NOR, NZL, SWE, USA, ZAF, NZL |
|
| Expanded Data Breach Risk Scan | This extension of the Data Breach Risk Scan also performs a Technical Safeguards Check. This check queries the device and highlights settings that do not meet common baseline configurations | |
| Custom Scans | Custom scans based on the following scan types: Data Risk Breach, Expanded Data Risk Breach, File Finder, Security and PCI and PAN Scan.
To access the Scan Configuration section of the Risk Intelligence dashboard, click the Custom Scans button. To manually synchronize N-sight RMM's custom policy list with Risk Intelligence, click the Reload Customized Scans button. |
|
Risk Intelligence scans run based on the local time of the computer the Agent is installed on.
These intensive scans may take some time to complete. There is a mechanism that prevents the scheduling of a scan within two hours of another scan starting. If two scans are scheduled to take place within this two-hour period, a notification displays when saving the policy.When a scan is still running when a new scan is scheduled to start, the currently running scan is stopped.
Scan Frequencies and Options
| Frequency | Scheduling Options / Notes | ||
|---|---|---|---|
| Do Not Run | Disables scan | ||
|
Once per Day
To run the scan weekly, select the required day. |
Run on Days | Select Time | Run if Missed |
| Once per Month | Day of Month on which to Run | At Time | Run if missed |
| Manual | Scan only runs when manually initiated. | ||
Edit a Custom Policy
Please note that the default policies settings are editable.
- In the All Devices view, go to Settings > Risk Intelligence > Policy.
- Select the target policy.
- Click Edit.
- Change the editable settings.
- Click Save once complete to apply.
Delete a Custom Policy
Default policies are locked for deletion. You cannot delete a Risk Intelligence policy when it is currently in use on a computer or it is set as the default for a Client or Site, even when there are no devices registered against the Client or Site
- In the All Devices view, go to Settings > Risk Intelligence > Policy.
- Select the target policy.
- Click Delete .
- Confirm removal.
What do you want to do?