2025.4 Release Notes
Build Number: 25.4.0.16 Last updated: 16/02/2026
N-central 2025.4 HF1 (build N-central 2025.4.0.9 – 2025.4.0.16) Patch issue
This Hotfix resolves an issue introduced in N-central 2025.4.0.9 where a defect in the Windows Software Probe caused PME patching to fail when probe caching was enabled. See the 2025.4 HF1 Release Notes for further details.
If you have not already updated to version 2025.4, we recommend that you install the 2025.4 HF1 release.
What's New in 2025.4
We’re introducing exciting new features, enhancements, and critical fixes to improve usability, security, and performance. Here’s a preview of what’s expected in the 2025.4 release.
On-premises upgrade prerequisite: Report Manager SP7
Ensure Report Manager is upgraded to Service Pack 7 (SP7) before proceeding with the on-premises upgrade to 2025.4.
Agent Compatibility Update
N-central agents running a version earlier than 2020.1 will no longer be able to communicate with the N-central server after this release.
To ensure uninterrupted monitoring and management, please upgrade all agents to version 2020.1 or later before applying this update.
Legacy API Availability Changes
As part of our ongoing commitment to strengthening the security posture of N-central, we are deprecating certain legacy API functionalities and removing access to APIs originally intended for internal use only.
-
The public SOAP EI API will no longer be accessible.
-
The public SOAP EI2 API will remain available
-
The public REST API will remain available
-
N-central Mobile APP
-
N-central Mobile Device Management (MDM)
-
External Data Feed (A new API is available under EI2 that is not affected)
The below features will cease to function post-upgrade until they are migrated to newer APIs in future releases. Features impacted :
To support transitional needs, we’ve introduced a new setting under:
Administration > Mail and Network Settings > Network Security > LEGACY APIS
This setting allows administrators to temporarily re-enable deprecated APIs.
Please note that re-enabling these APIs will expose the N-central server to potential malicious exploits.
EDF API Changes
As part of the removal of the EDF API users will need to start using the EI2 API in order to continue to access EDF functionality. Instructions can be located through our javadocs in the EI2 API documentation under the “edfsubmit” section.
<serveraddress>/dms/javadoc_ei2/com/nable/nobj/ei2/ServerEI2_PortType.html
Automation Manager Update
To ensure full compatibility with the 2025.4 release of N-central, upgrade the N-central agent/probe to version 2025.4 on all devices running Automation Manager designer to version 2.98.2.2.
Identity & Access Management (IAM)-Multi-Factor Authentication (MFA) Enforcement for SSO Accounts
Multi-Factor Authentication (MFA) is now mandatory for all SSO accounts using N-able Login (formerly MSP SSO), beginning November 2025.
All SSO clients using N-able Login (formerly MSP SSO) starting
-
MFA is now mandatory for both new and existing users in the staging environment. Users without MFA configured will be prompted to set it up during their next login. This enforcement is part of our broader roadmap for global MFA adoption and is aligned with ISO-certified security standards.
-
Impact:
-
All users must complete MFA setup to continue accessing N-central via N-able Login including Product Admin.
-
MFA setup is integrated into the standard onboarding and authentication flows.
-
Administrators retain the ability to reset MFA for users; recovery codes may be required in some cases.
-
Native HaloPSA and Autotask REST API Support
The following two integration features are now available to all partners from this release:
-
HaloPSA Native Integration
-
Autotask REST API Support
These features were previously available only through a controlled rollout starting from 2025.2.1, but are now open for full partner adoption to support improved service workflows and API flexibility.
Dedicated native integration with HaloPSA (Professional Services Automation) inside N-central
Why we developed this?
While the existing HaloPSA integration was functionally complete, it introduced friction because it was managed across two separate platforms. Partners and Sales Engineers consistently highlighted the need for a simpler, faster, and more cohesive experience.
Also, having a native integration positions N-central as a centralized hub for ITSM/PSA integrations, aligning with the vision of a unified, modernized platform.
Features include:
-
Unified User Experience
-
All configuration and operations are managed directly within N-central.
-
No need to switch between HaloPSA and N-central or use third-party connectors
-
-
Device & Customer Mapping: Easily map devices and customers between N-central and HaloPSA for accurate service tracking and streamlined workflows.
-
Automated Ticketing:
-
Automatically create and update tickets in HaloPSA based on N-central alerts.
-
Two-way sync ensures ticket statuses remain aligned across both platforms.
-
-
Credential Management:
-
Securely store and manage HaloPSA API credentials in N-central.
-
Includes a "Test Connection" feature to validate your integration setup.
-
-
Optimized via HaloPSA APIs: All integration operations - ticketing, asset sync - leverage HaloPSA API endpoints.
-
Improved Time Entry User Matching: The integration now supports listing API-only users from HaloPSA.
With HaloPSA’s robust native billing capabilities - including support for billing based on the number of devices managed - the need to manage billing profiles directly in N-central has been eliminated.
While partners had shown strong interest in this features, critical issues were uncovered during testing with early adopters and as a result the GA was postponed until we fix critical issues in both NFR and Production environments.
The following are the changes we implemented:
Device Export & Asset Sync
Bulk Device Sync
-
Issue: Currently, only 15–25 devices can sync in a single job before failures or timeouts occur.
-
How we fixed it: Under engineering review.
Asset Uniqueness
-
Issue: The Halo setting “Asset tag must be unique” caused problems - if enabled, exports were blocked; if disabled, exports went through but created duplicates.
-
How we fixed it: Devices with the same name are now handled cleanly by appending all device names with N-central Device IDs.
Customer Mapping Validation
-
Issue: Devices that weren’t linked to a customer in N-central were still being synced, which confused PSA systems and created orphaned records.
-
How we fixed it: The Customer Name / Site Name is now mandatory during Customer Mapping. A warning message is displayed on the Customer Mapping page if no valid customer name is selected.
If an export is triggered without a complete mapping, the export fails gracefully with a clear error explaining why.
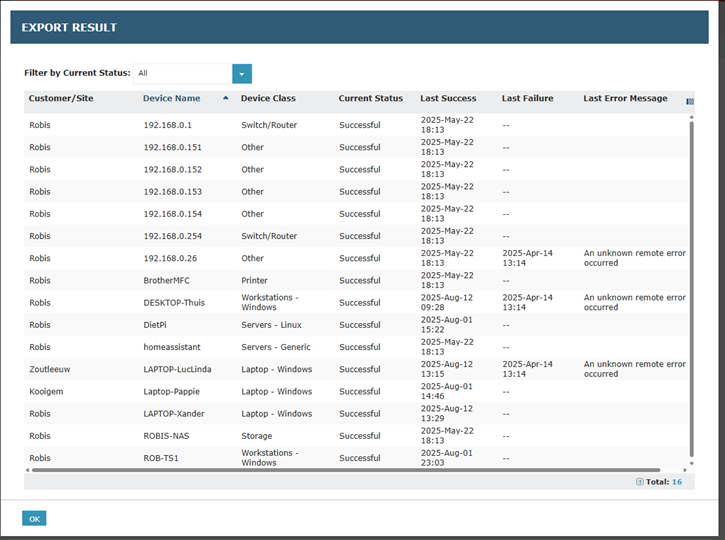
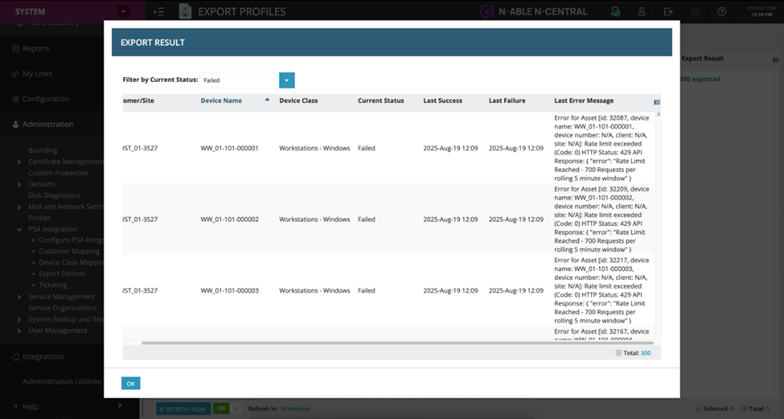
Smarter Error Messaging for Failed Device Exports
Issue: When device exports to Halo failed, the error messages were too vague or generic, making it hard to understand the root cause.
How we fixed it: Improved the export error messages so failures are clearly explained, helping admins quickly diagnose and resolve issues. The "Last Failure Timestamp" column shows the time of the error attempt, and the "Last Error Message" column contains a clear, user-friendly message explaining the failure.
-
400 Validation Errors – Clear guidance when fields are missing (e.g., “Device serial number missing”).
Error message after update:
-
401 Unauthorized Errors – Friendly messages when API credentials are invalid, with instructions to check the HaloPSA client secret.
-
429 Rate Limit Errors – User-friendly messages explain when too many exports were triggered and advise when to retry.
Ticketing Improvements
Issue: Tickets were mapped to wrong types and noted that required fields often blocked syncs.
Alert-Partners please ensure this setting is on your Halo side
All ticket type fields are configured as Visible – Not Required.
(Configuration → Tickets → Ticket Types → Edit → Field list → set to Visible – Not Required)
Approval process is disabled.
(Configuration → Tickets → Approval Processes → uncheck “Allow choice of CAB members when an approval step begins”).
Ensured that now the correct Ticket Types Are Assigned During Ticket Creation From N-central to HaloPSA.
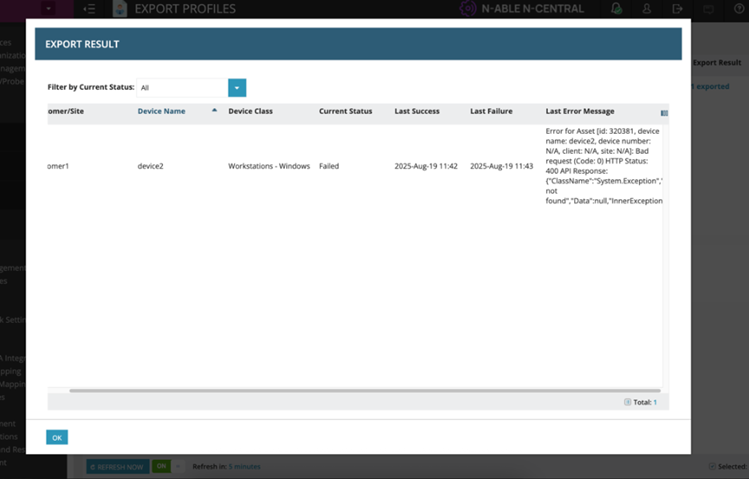
Show & Download Error Messaging for Failed Device Exports
Issue: Previously, when a device export failed, the error message shown in the modal box was often too long, truncated, or unreadable.
How we fixed it: Partners can quickly capture and share error details without digging into logs.
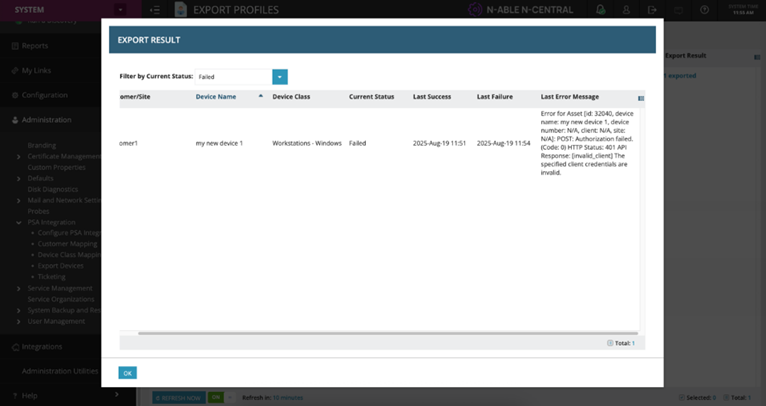
-
Once users select the filter by Failed exports, only failed device export rows appear.
-
Long error messages in the Export Results table are now truncated with an ellipsis (…) for a cleaner view. Hovering over a truncated error shows the full message in a tooltip, so details are never lost.
-
Added two quick-action icons next to each error message: Copy to Clipboard – instantly copies the full error text for troubleshooting or sharing & Download as Text File – saves the full error (with device details and timestamp) as a .txt file for easy reference or support tickets.
Known Limitation:
-
At this time, errors can only be copied or downloaded one at a time. Bulk copy/download is not yet supported.
For detailed information on capabilities for Autotask REST API Support, see: N-central 2025.2.1 Release Notes
N-central SSO Enhancements – Stronger Security, More Control
This release strengthens SSO session security, administrator control by
-
Providing more flexibility to configure how N-central enforces token expiry to balance strict session security against compatibility with different identity provider (IdP) implementations.
-
Adding emergency controls with one-click session revocation when high security concerns arise.
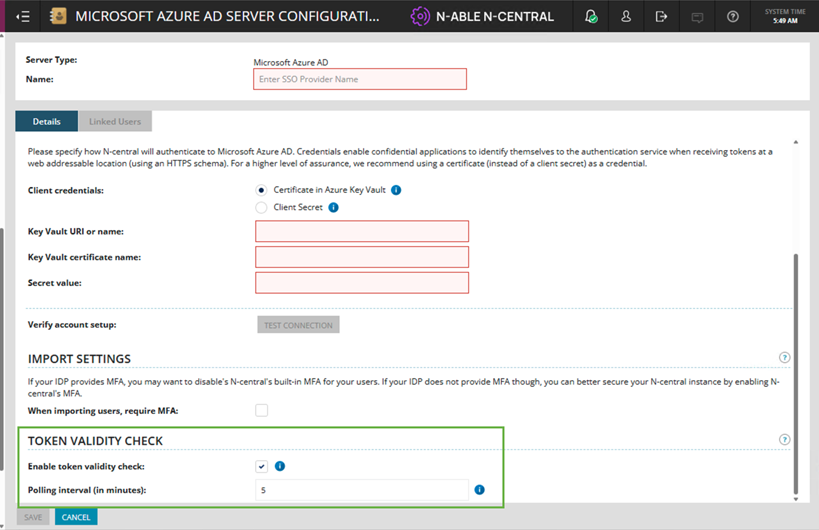
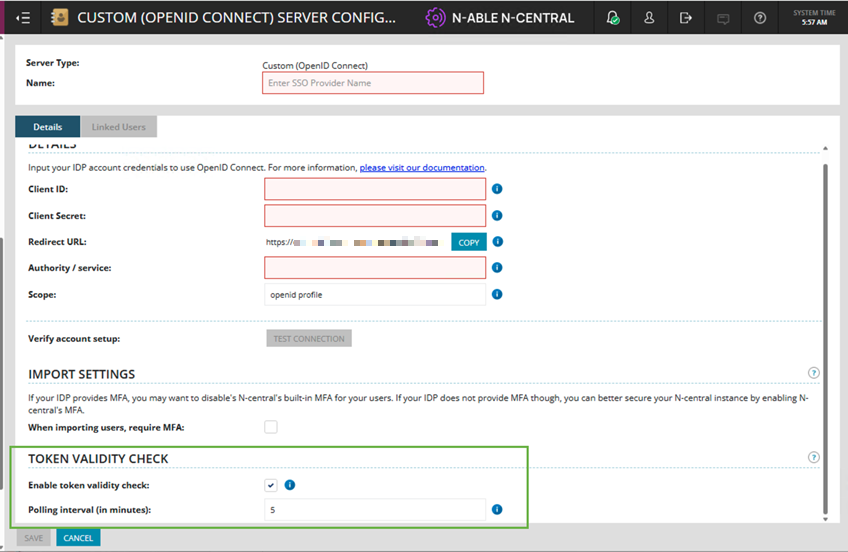
Token Validity Check (new setting) for Microsoft Azure AD and Generic Identity Providers:
-
The "Enable token" validity check option is checked by default for new providers.
-
When enabled, N-central validates the token’s expiry claim on every request, ensuring immediate access termination once a token expires.
-
Existing IDP configurations upgrading to this version → validation defaults to off unless explicitly enabled.
-
For N-able Login (MSP SSO), token validity check is always enforced (not configurable in the UI).
This setting applies only to active SSO sessions.
Polling Interval (Added a new input bar)
The Polling interval setting defines how often N-central checks externally with the identity provider to confirm a token is still valid.
-
Default value is 5 minutes; range is 1 to 1,440 minutes.
-
Polling is independent of the token validity check. Even if you disable token claim validation, you can still configure external polling.
-
Tokens issued by N-able Login are time-limited (60 minutes), so sessions naturally expire if not refreshed.
The Polling Interval is updated for both new and existing IdPs.
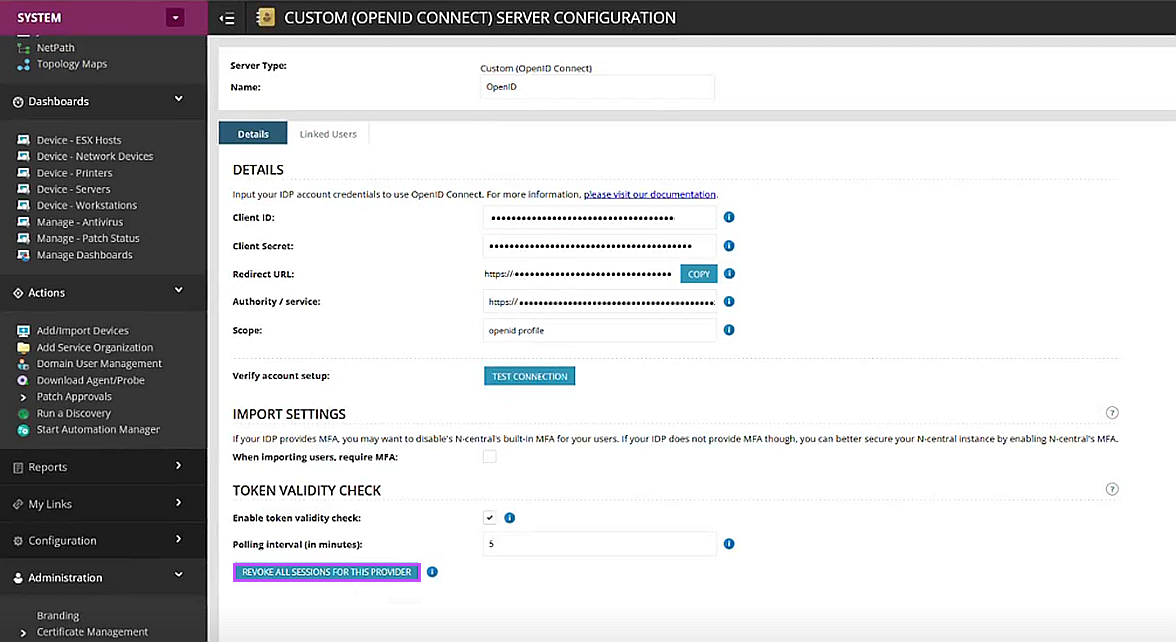
Revoke All Sessions (Added a new button)
-
A new “Revoke all SSO sessions” button is available for Azure AD and Custom (OIDC) providers which forces all users authenticated with that provider to log in again. Use this when applying sensitive security changes or responding to access concerns.
-
Other providers and local authentication remain unaffected.
-
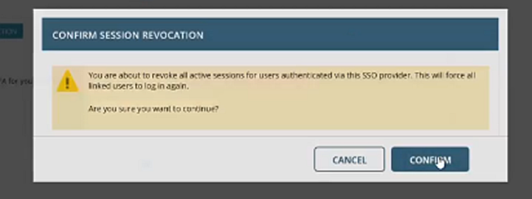
Clicking on this button will display a confirmation modal with message “You are about to revoke all active sessions for users authenticated via this SSO provider. This will force all linked users to log in again. Are you sure you want to continue?”
-
When the user clicks on the Confirm button, it invalidates all active sessions for users authenticated through this SSO provider. The user will be logged out and prompted to Login again.

User Audit Syslog Export – Additional Audit Events for Ecoverse Features
In earlier releases, the audit coverage for Ecoverse included:
-
Patch Management events (e.g., patch install/uninstall logs).
-
Reboot actions initiated from the Asset View.
This release significantly expands coverage to additional high-impact activities:
Take Control & Advanced RBM
-
Remote control session start/end (from Asset View, native session).
-
Remote background session start/end.
-
Remote background file transfer (upload, download).
-
Process termination.
-
Registry edits.
-
System shell command execution.
-
Scripting
-
Script executed.
-
Script added.
-
Script edited.
-
Script deleted.
Scripting is currently in development and will be available for Limited Technology Preview (LTP) this December.
Asset Tags
-
Tag created.
-
Tag edited.
-
Tag assigned/unassigned to Assets.
-
Tag deleted.
Cloud Commander
-
Tenant connects, disconnect, remove.
-
Cloud users add, edit, delete.
-
Cloud user password reset.
-
Cloud user MFA reset.
-
Cloud user session revoked.
-
Cloud user disabled.
-
Cloud user license assigned/unassigned.
-
Cloud user assigned/unassigned to groups.
-
Cloud user assigned/unassigned to roles. To configure Syslog export and take full advantage of these features, see: Configure Syslog Export.
Applying Asset Tags in Asset View
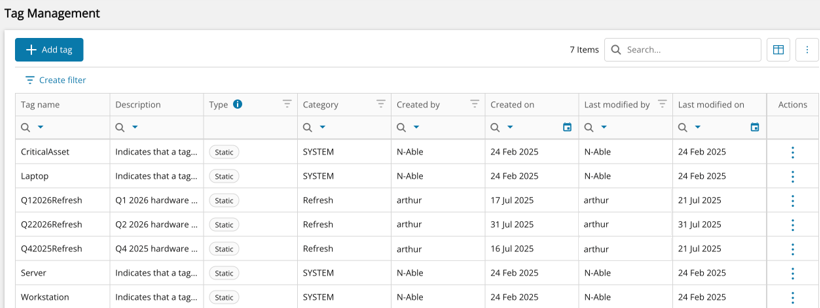
Easily categorize and organize devices with greater precision using the new Asset Tag capabilities in N-central. This enhancement brings more flexibility and control to how partners manage and track devices across distributed environments.
-
Apply custom tags to devices across all levels: Partner, SO, Customer, and Site.
-
Assign tags directly from the Asset View to enable consistent device labeling to support filtering, reporting, and workflow automation.
-
Manage Tags-Create, edit, and delete tags via the new Tag Management screen (admin-only access).
-
Tag visibility and usage are controlled through a combination of feature flags, user role permissions, and organizational hierarchy.
See also:
What’s new: Quick Navigation
Navigating N-central is now simpler. The Quick Navigation search bar indexes all destinations available in the left-hand navigation menus, helping users quickly locate pages and configuration screens without manually expanding panels.
-
Global Search now displays all pages and actions visible in the left-hand navigation menus across all modules (System, Actions, Integrations, etc.).
-
Search results are permission-aware, showing only pages the logged-in user has access to.
-
Results are now consistent with what is displayed in the UI, no hidden, backend, or deprecated links.
Why it matters
Previously, the users were limited to the currently visible menu panels, requiring users to drill through multiple layers to find a page. This enhancement delivers a unified search experience for faster access to any navigable page or action.
Known limitations / Future iterations
The current release focuses on search visibility based on role and feature access. Future releases will introduce:
-
Customer Tree Level Filtering: refining results based on the selected customer or site context.
-
Searching for filters, devices, services, profiles, or other system entities remains outside the current Global Search scope and is still in the design and planning phase.
Analytics Updates
| Issue Type | Issue key | Summary | Release Notes | Release Date |
|---|---|---|---|---|
| Enhancement | DW-494 | N-central Hardware Inventory Report | Added a column to the FACT_PHYSICAL_STORAGE_LATEST' in the 'Hardware Inventory (Physical Disk)' data model called 'DSS_IS_DELETE' that indicates if the record was deleted. This can be used to exclude removed storage devices from queries for reporting on disk size. | 29-Oct-2025 |
| Enhancement | DV-8160 | N-central Analytics ESR Dashboard |
Removed the Patching tab in the ESR ashboard. Analytics reports and dashboards will now use the same underlying patch data model. See What else is changing? in Upcoming public preview - Patch Compliance report. |
16-Feb-2026 |
| Enhancement | DV-8153 | N-central Analytics Network Assessment Report |
Removed the Patch Status section in the Network Assessment report. Analytics reports and dashboards will now use the same underlying patch data model. See What else is changing? in Upcoming public preview - Patch Compliance report. |
16-Feb-2026 |
| Bug | DV-7816 | N-central Last Boot-Up Time and Logged-In User Report | Fixed an issue where the Last Boot-Up Time and Logged-In User report sometimes showed an incorrect last logged-in user. This resolves NCIP-14082. | 29-Oct-2025 |
| Bug | DV-7705 | N-central Last Boot-Up Time and Logged-In User Report | Fixed an issue where the Last Boot-Up Time and Logged-In User report sometimes displayed devices more than once. | 29-Oct-2025 |
| Bug | DW-479 |
Patch Compliance dashboard DDA Patch data model |
Fixed an issue that caused Patch Publish dates to be blank in the Patch Compliance dashboard and the Patch data model in Direct Data Access | 11-Nov-2025 |
| Bug | DW-481 | DIM_SITE and DIM_CUSTOMER records | Fixed an issue where initial records in DIM_SITE and DIM_CUSTOMER contained incorrect dates, which caused missing data in some reports. | 11-Nov-2025 |
| Bug |
DW-504
DW-505 |
Analytics Reports
Dashboards |
Fixed an issue where device keys in the warehouse were incorrectly set to 0 leading to missing application data in Analytics reports and dashboards. | 11-Nov-2025 |
| Bug | DV-7673 | Managed Device Summary Report | Resolved an issue where Service Name and Identifier values were blank in the Monitored Services table. | 17-Nov-2025 |
| Bug | DV-8123 | N-central Analytics Patch Compliance dashboard |
Fixed an issue that caused unmanaged devices to appear in the Patch Compliance dashboard. The dashboard now only includes patches related to managed devices. |
13-Jan-2026 |
| Bug | DV-7856 | N-central Analytics Software Inventory Report | Fixed an issue where devices were sometimes missing from the dropdown after selecting a customer. | 11-Feb-2026 |
Scheduled Reports and Notifications – Recipient Visibility Improvements
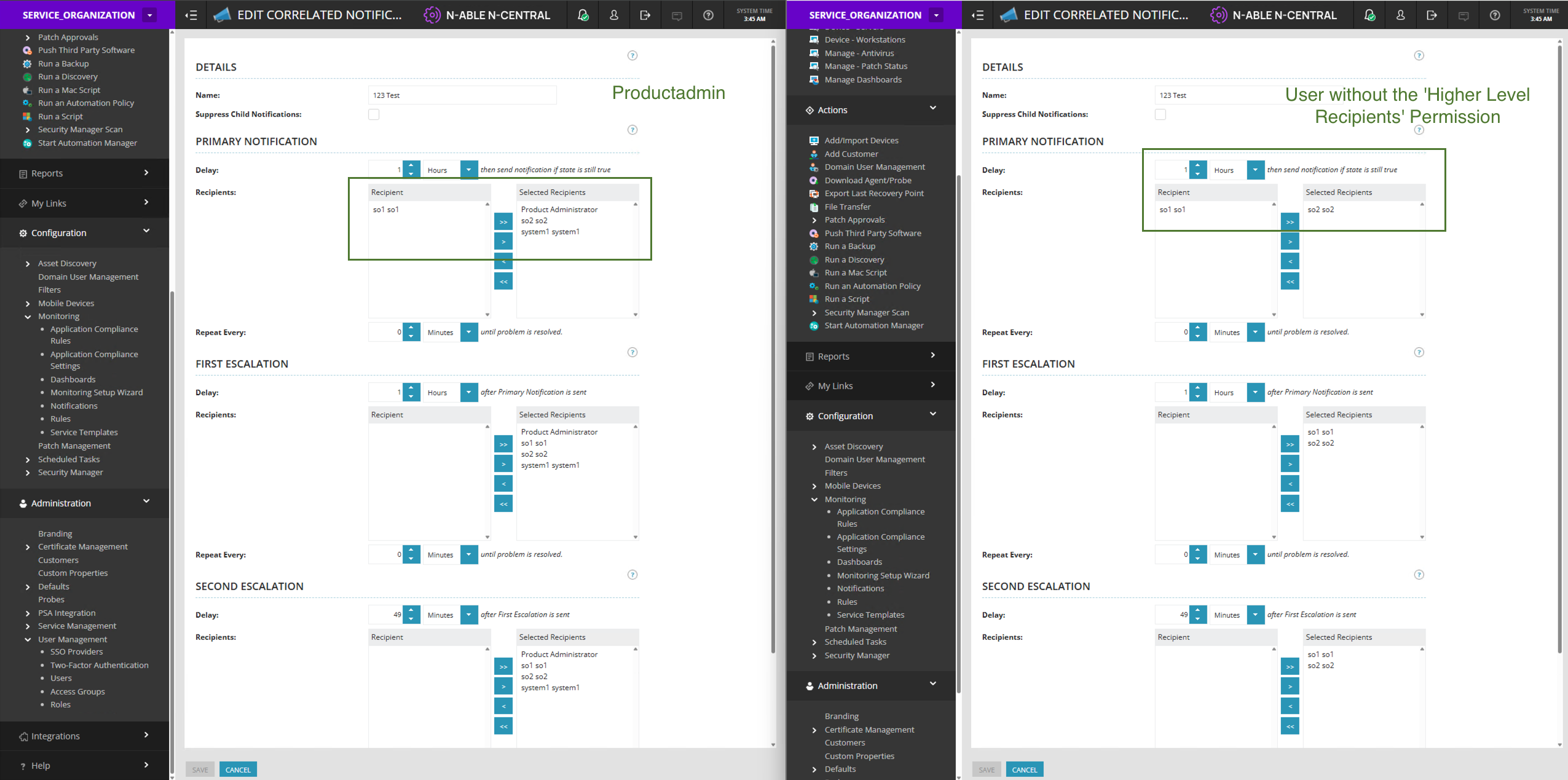
Before the fix:
Customer-level accounts were previously able to view SYSTEM-level recipients when managing scheduled reports or correlated notification profiles. This occurred when a report or notification entity was created by a user with higher-level permissions and later updated by a user without them
After the Fix:
The system now restricts recipient visibility based on the user’s permission scope thus preventing lower-level users from viewing or unintentionally modifying system-wide or higher-level notification recipients.
-
Users can only view and modify recipients they have access to.
-
Hidden recipients (outside the user’s permission level) remain associated with the report or profile and are preserved when the user saves changes.
-
Navigate to Configuration → Monitoring → Notifications → Add Correlated Notification Profile from a SO /Customer/Site level.
-
For a user without “Higher Level Recipients” permission, they will see only the recipients from the same level.
N-central Mac Agent v1.13 (5th Nov 2025)
We’ve released a new version of the N-central Mac Agent with important security enhancements, including an update to the latest OpenSSL LTS version to address known vulnerabilities.
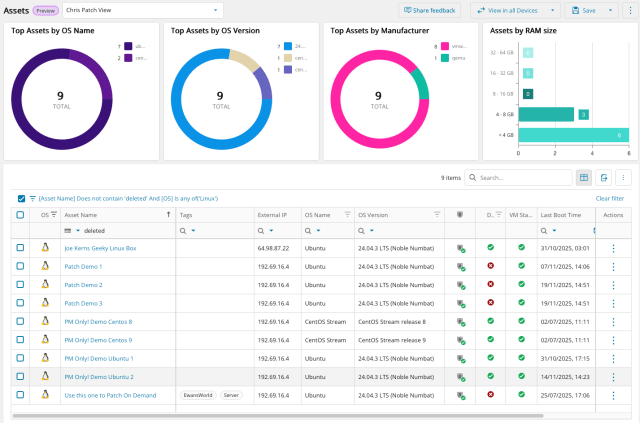
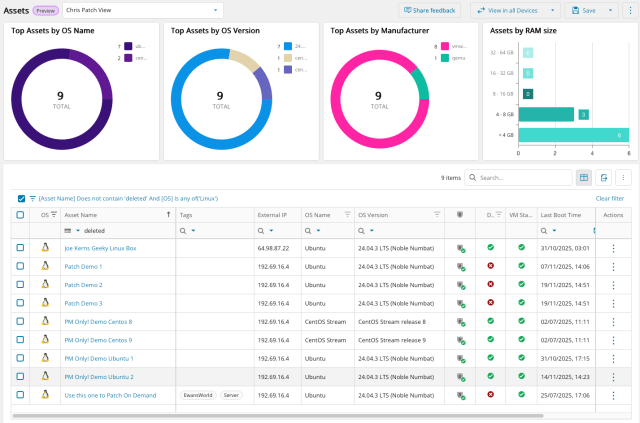
Introducing the Public Preview of Linux Patch Management (24th Nov 2025)
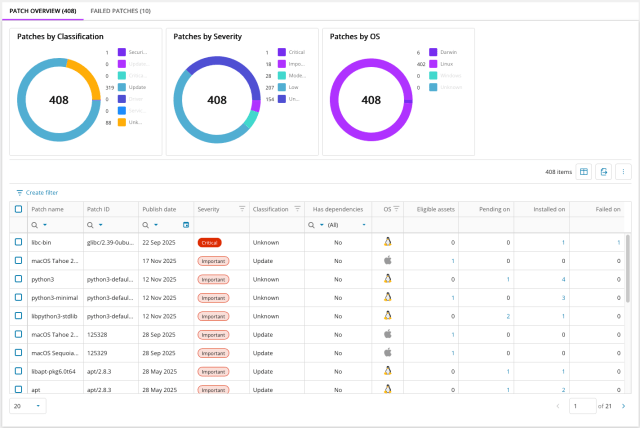
We’re excited to announce the public preview of Linux Patch Management in N-central delivering greater control, visibility, and flexibility for patching Linux environments.
This new capability provides a centralized patch overview, showing detected packages, patch status, and detailed metadata for each asset. Technicians can initiate on-demand patch installations, schedule updates, and manage reboot behavior, all while monitoring real-time device status.
Enhanced Diagnostics and Integration
Failed patches are surfaced with detailed failure codes, messages, and quick retry options for faster remediation. Patch engine health and last scan times are now visible within the asset view, and audit logging with role-based permissions ensures traceability and security. This preview lays the foundation for upcoming features such as patch policies, continuous retries, and expanded OS support, helping you streamline operations and deliver measurable value to your business.
Prerequisites
-
N-central version 24.6 or later.
-
Enable Analytics and accept cloud data storage.
-
Users must be signed up to N-able (MSP) SSO.
Key Features
Centralised Patch Overview
All detected Linux packages are displayed in a single interface. Patch status is shown for each asset, including installed, pending, and failed patches. Detailed metadata is available for each package, and details can be exported for coverage information.
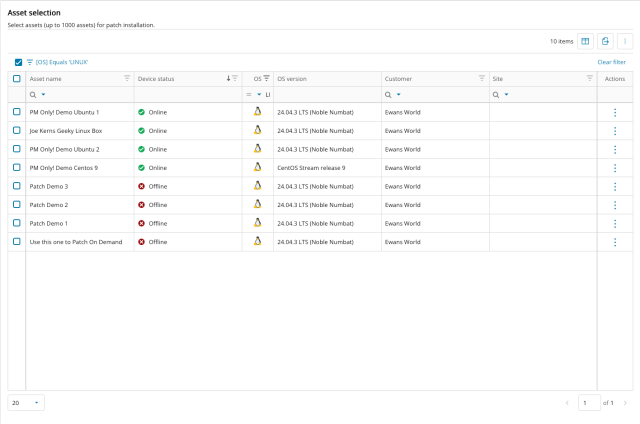
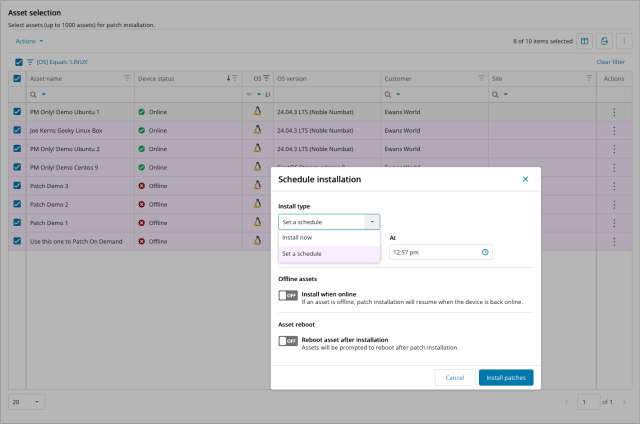
On Demand Patch Installation
Technicians can apply patches to Linux devices, viewing their real-time online/offline status. Patching can be scheduled or set to install when devices come back online whilst also controlling the reboot behavior.
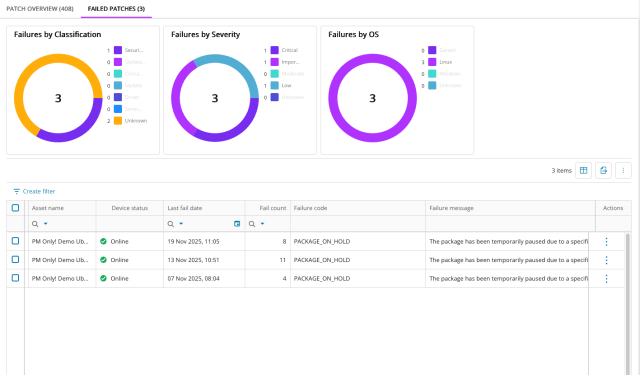
Failed Patch Diagnostics
Failed patches are surfaced with detailed failure codes, messages, fail counts, and last fail dates. Quick retry actions are available for real-time patch installation attempts.
Asset View Integration
Patch engine status and last scan time are visible within the asset view within a new Patch Management Icon, supporting quick engine health information and last scan times.
Patch tab within assets overlay
Patching for each Linux asset can be tracked and initiated including installing and install status, scheduling, reboot control, and historical patch data.
Audit Logging and Permissions
Patch audit log entries and user permissions provide traceability and role-based control over patch operations. These features work within the existing audit logs and user roles and permissions of the existing Patch Management features of N-central.
Getting Started information:
Patch management components are automatically deployed within the Unified Framework Agent without making changes to the system across Linux distributions compatible with N-central.
Small hourly detection scans run to keep you up to date with the latest patches available.
Preview Stage
Throughout the public preview, we will continue to add more functionality and enhancements based on your feedback.
By providing feedback, you’ll help us refine and expand patch management capabilities for Linux and beyond.
Please share your thoughts and feature requests via the feedback link within Patch Management or directly with the product team.
Take Control – Integrated Agent 7.50.24 (26th November 2025)
This release focuses on stability improvements for the Windows Agent in Take Control Integrated. We addressed the core issues introduced in versions 7.50.22 and 7.50.23 that affected memory usage and log generation.
Fixes:
-
Resolved a memory leak issue.
-
Fixed a problem where log files grew abnormally large under certain workflows. Log generation is now normalized and capped at expected levels.
Continued Development on CMMC-Compliant Version of N-central for On-Premises Partners
We are continuing development on the CMMC-compliant version of N-central, specifically designed for on-premises partner-hosted instances. This work is part of our broader initiative to ensure CMMC Level 2 compliance, supporting partners managing environments aligned with U.S. Department of Defense (DoD) cybersecurity requirements.
Take Control Security Modernization (FIPS 140-3 Upgrade) (26th November 2025)
Why it matters
N-central 2025.4 introduces an important security enhancement to Take Control, aligning remote access with the compliance standards required for regulated and high-security environments.
We have replaced legacy cryptographic libraries with fully FIPS 140-3–approved modules and removed all non-compliant algorithms. This upgrade brings Take Control up to the same security posture as the rest of N-central’s CMMC and FedRAMP-ready components. All remote sessions will now use modern, compliant encryption. Partners can deploy N-central in regulated sectors without exceptions, while everyone benefits from a stronger overall security baseline.
What’s included
-
Full adoption of FIPS 140-3 certified cryptographic modules.
-
Removal of non-compliant algorithms and legacy libraries.
-
Security alignment with CMMC and FedRAMP requirements.
-
Broader internal stability improvements and defect fixes.
Release Timeline
Take Control Cloud – 2025.10 (Early October)
Agents (phased rollout):
-
Mac Integrated Agent – 6.00.70 (Early October)
-
Windows Integrated Agent – 7.50.22 (Mid October)
-
Mac Standalone Agent – 6.00.70 (Mid October)
-
Windows Standalone Agent – 7.50.22 (Mid October)
Viewers (Late October):
-
Windows Integrated Viewer – 7.50.22
Connects only to Agents 7.50.22+
-
Mac Integrated Viewer – 6.00.70
Connects only to Agents 6.00.70+
-
Windows Standalone Console/Viewer – 7.50.22
-
Mac Standalone Console/Viewer – 6.00.70
Patch Management Engine (PME) Update: Version 2.13.6.5586 GA (11 Nov 2025)
Patch Management (PME) Version 2.13.6.5586 GA addresses multiple issues:
-
Mitigation of the effects of changes to Microsoft Patch titles.
Introduced measures in PME to mitigate the impact of Microsoft’s recent simplified Windows Update titles and associated format changes.
Microsoft has adopted the format: “YYYY-MM UpdateType (KBnnnnnnn) (FeatureUpdate.Build)“, where UpdateType can be “Security Update, Preview Update, .Net Framework Security Update”.
For example, “2025-11 Security Update (KB5034123) (26100.4747)”
Automatic keyword-based approvals may not work in the future when Microsoft’s simplified title format replaces the current structure.
-
Support 25H2 Feature Update via Enablement Package.
Added support for detecting and applying the 25H2 Feature Update via Enablement Package. This applies to devices running 24H2 with the August Cumulative Update Preview Patch or later alreadyapplied. Enablement Packages activate 25H2 with a small update and reboot. For earlier Windows 11 or Windows 10 editions, the ESD (Electronic Software Download) file option will be available soon. This uses the OS switch technique where a new OS is installed side by side with the original.
-
Approvals.xml issues.
Addressed an issue where connection errors to Microsoft Update servers could lead to unexpected content in the N-central approvals.xml file.
-
Minor supersedence improvements.
Improved the installation date logic in our supersedence calculations.
Patch Management Engine (PME) Update: Version 2.13.9 GA (15 Dec 2025)
We’re pleased to announce the General Availability (GA) of Patch Management Engine version 2.13.9.
This release contains the completion of 25H2 support, additional changes required to adopt the recent Microsoft patch title changes and changes to improve the resilience and robustness of a PME component.
-
Full support for Windows 11 25H2 upgrades
Previous release (2.13.6) introduced support for upgrading to Windows 11 25H2 via Enablement Package for devices already on Windows 11 24H2.
This update extends support to older Windows 11 editions and eligible Windows 10 devices, enabling in-place upgrades using ESD files.
-
Adaptation to Microsoft Patch Title changes
Enhanced processing, identification, matching, and filtering of patches based on OS and build number.
-
Improved resilience of File Cache Service Agent
Better recovery from failed downloads for increased robustness.
Bug Fixes
-
PMCM-10787 – improves how we reference the version of available ESD file updates
Build Information
| Component | Version |
|---|---|
| PME | 2.13.9.5611 |
| MSPPlatform | 2.13.9.5029 |
| PME.Diagnostics | 2.14.0.5021 |
| PME.ThirdPartyPatch | 2.13.9.5029 |
Introducing Custom Properties in N-central Analytics Direct Data Access (15 Dec 2025)
We’re excited to announce a new feature in N-central Analytics: you can now create custom Device and Organization properties directly in Direct Data Access.
With custom properties, you can track data unique to your MSP. For example, you can track:
-
Windows 11 compatibility
-
BitLocker status
-
Service tiers
You can update these properties manually or automatically via scripts, giving you full control over your data.
How It Works
Analytics delivers custom property data in a lightly modeled, row-based format. Each row represents a property and includes columns for device or customer identifiers and their corresponding values.
You can use this data to filter, enrich, and refine your queries, unlocking more insights from your existing Direct Data Access views.
Get Started
-
Learn more about custom properties in Direct Data Access here.
-
Find detailed guidance on setting up custom organization properties here.
-
Find guidance on setting up custom device properties here.
Custom properties in Direct Data Access give you deeper visibility and control over your MSP data, helping you make smarter decisions faster.
Announcing the Release of Report Manager 5.0 SP8 (15 Dec 2025)
Report Manager 5.0 SP8 (5.0.8.18)
-
Download link (login required)
Report Manager 5.0 SP8 focuses on platform readiness, reporting accuracy, ETL performance, and security hardening. It’s a stability and futureproofing release rather than a feature explosion.
The new Report Manager service pack (SP8) includes platform updates, reporting accuracy improvements, and multiple performance, reliability, and security enhancements. This release adds support for SQL Server 2022 and Windows Server 2022, improves the accuracy of patch executive summary and patch detail reports, and delivers significant optimizations to ETL processing to better handle large data volumes and long-running jobs. SP8 also introduces stronger security hardening across web and API layers and improves maintenance services to prevent stalled data processing.
This service pack should be applied to your Report Manager server and does not require an upgrade to your N-central server version. For full details, including the complete list of fixed issues and download information, please refer to the release notes and link above.
Dynamic Asset Tagging, Asset Activities and New Asset Event Information (19 Dec 2025)
We’re pleased to announce several new features and product improvements to N-central and N-sight. This release introduces new automated tagging capabilities, known as Dynamic Tagging, secure boot and feature release information, and a new Asset Activities Panel that displays new event codes, and deeper asset information. These updates are designed to provide you with a higher level of automation, greater control, and deeper insights into the environments you manage.
Dynamic Asset Tagging
Dynamic Asset Tagging is now Generally Available, significantly enhancing tagging capabilities by enabling automated addition and removal of tags based on user defined rules. This exciting new capability makes possible a scalable approach to asset categorization and grouping. It also creates a foundation for future innovations such as the new policy engine.
Configuring dynamic tag rules is easy and follows already established workflows and patterns from within Assets View, utilizing rich filtering to fine tune rules based on various key datapoints.
This functionality will be available to N-central partners over the coming days.
Key Highlights
-
Create, edit and delete dynamic tag filters
-
Automatically apply tags when saving a new tag filter
-
Automatic re-evaluation of tags assigned to an asset when datapoints change
-
Control access through roles and permissions
-
Search and filter assets by assigned tags
Secure boot and feature release information

We’ve added 2 new columns detailing Secure Boot information and OS Feature Release details to the library of data points available within Assets Views.
By surfacing this information within Assets View, technicians gain actionable insights into a foundational layer of device security – enabling faster response, stronger compliance, and greater client confidence in endpoint protection.
-
Spot risks before they become an issue – See easily where secure boot is disabled and determine endpoints lagging behind on their feature release
-
Stay confident in compliance – Keep in line with security frameworks such as CIS, NIST and other internal policies
-
Save time and reduce manual work – No more running PowerShell scripts to retrieve this information
-
Demonstrate to clients you are protecting them at every layer – Managed software and hardware layers
For example, these additional columns, along with the rich filtering available through Assets View helps in identifying machine that require urgent attention to bring them into a compliant state.
Asset Activities Now Available in the Assets View
We’re excited to introduce a new Activities View in the Assets View dashboard. This feature gives frontline technicians quick visibility into recent events on an endpoint, making it easier to investigate device issues and respond to helpdesk tickets and alerts.
The Activities View is now available in public preview. Initially, it includes user access events and system crash events (such as blue screen errors). Over time, we’ll add more event types based on your feedback, so let us know which events matter most for diagnosing common IT issues.
How to Access Activities:
-
In the new Assets View, click a device to slide out the Device Details view.
-
Click the Activities tab to see recent events from the last 90 days.

The tables below provide a reference to the event details we are currently capturing on a 30-minute cycle:
| Event ID | Event name | Logon type requested | Description |
|---|---|---|---|
| 4624 | Successful logon |
2: Interactive 7: Unlock 10: RemoteInteractive 11: CachedInteractive |
Occurs when a logon session is created on the destination machine. |
| 4625 | Failed logon attempt | Same as above | Occurs when a logon attempt fails on the local machine. |
| 4634 | Logoff |
2: Interactive 10: RemoteInteractive |
Occurs when a logon session ends and no longer exists. |
| 4647 | User-initiated logoff | 2: Interactive | Occurs when a user initiates a logoff. |
| 4648 | Logon with explicit credentials |
2: Interactive 10: RemoteInteractive |
Occurs when a process attempts a logon by explicitly specifying credentials. Common in scheduled tasks or when using the RUNAS command. |
| 4672 | Administrator logon (special privileges assigned) |
2: Interactive 10: RemoteInteractive |
Occurs when special privileges are assigned to a new logon session. |
| 4768 | Kerberos authentication ticket (TGT) request |
2: Interactive 10: RemoteInteractive |
Occurs when the Key Distribution Center issues a Kerberos Ticket Granting Ticket. Only on domain controllers. |
| 4769 | Kerberos service ticket request |
2: Interactive 10: RemoteInteractive |
Occurs when the Key Distribution Center receives a Kerberos service ticket request. Only on domain controllers. |
| 4776 | NTLM authentication attempt | 2: Interactive | Occurs when credentials are validated using NTLM authentication. |
| 4800 | Workstation locked | 2: Interactive | Occurs when a local session is locked. |
| 4801 | Workstation unlocked | 7: Unlock | Occurs when a local session is unlocked. |
| Event ID | Event name | Description |
|---|---|---|
| 41 | System kernel-general crash | Occurs when the system restarts unexpectedly without cleanly shutting down first. |
| 1001 | Application crash |
Occurs when Windows Error Reporting has logged an application error or crash. Common BugCheck codes include:
|
| 6008 | Unexpected system shutdown | Occurs when the system shuts down unexpectedly. |
We very much hope that new Asset Activities view helps to make you more efficient in day-to-day issue diagnosis and resolution, and look forward to enhancing the new view with more activity data based on your feedback – please let us know!
N-central Mac Agent version 1.13.1 (13 Jan 2026)
This release focuses on the following network reliability improvements:
-
Network operation timeouts: Added timeout handling to prevent agent freezes during network operations.
-
Smarter error recovery: TLS/connection errors now trigger endpoint rotation while preserving the session, instead of forcing a full session reset.
-
Explicit failure handling: After repeated failures, the agent now logs clearly and performs a clean restart instead of running in a degraded state.
-
Enhanced logging: Better visibility into endpoint rotation attempts and failure scenarios.
Remote Control: Unsupported Linux distributions (23 Jan 2026)
Some older Linux distributions rely on legacy libraries that we no longer support. For this reason, CentOS 7, CentOS 8, and Ubuntu 20 are not supported for Remote Control.
Important Notice for OnPrem partners upgrading to 2025.4 from a version earlier than 2025.1
N-central 2025.1 replaced the underlying operating system on N-central from CentOS to AlmaLinux.
If you are upgrading from a version of N-central earlier than 2025.1 you will be doing a complete operating system migration.
This is a significant upgrade to N-central with new system requirements and the upgrade will take longer than a normal upgrade.
We highly recommend reviewing the updated system requirements and release notes for essential details before proceeding with the upgrade.
Migration Paths
Pre-2025 Upgrade Path: CentOS to AlmaLinux (2025.1)
-
2024.4.0.0
-
2024.6.0.0
-
2024.6.1.0
-
2024.6.2.0
2025 Upgrades: Systems already running AlmaLinux
-
2025.1.0.0
-
2025.2.0.0
-
2025.2.1.0
-
2025.3.0.0
-
2025.3.1.0
-
2025.4.0.0
Bug Fixes
A range of high-impact bugs have been resolved in this release. Be sure to review the full list included below for more details.
|
Category |
Updated Summary |
Issue Key |
|---|---|---|
|
Analytics v1.4.3 |
||
|
Video Controller (FACT_VIDEO_CONTROLLER_LATEST) Fixed an issue where reporting on the latest status of Video Controller data wasn't possible due to pricing tiers. |
DW-496 | |
|
Integration and Remote Support |
||
|
Core |
Remote desktop sessions blocked in some networks
Issue: Partners couldn’t connect via Remote Desktop (RDP) when traffic passed through a proxy/firewall. Fix: Updated agent handling so remote desktop works reliably through proxies. |
NCCF-767051 |
|
Core |
PSA integrations disrupted after content validation change
Issue: A recent change stopped allowing line breaks (newlines) in notification templates. Many partners relied on those newlines to format alerts for their PSA systems, so the change broke PSA notification processing. Fix: Restored support for newlines in templates, ensuring PSA integrations and notifications work as expected. |
NCCF-712085 |
| Core |
Take Control icon showed incorrect status
Issue: Remote Control icon incorrectly displayed “active” for some custom connection types even when disconnected. Fix: Updated UI logic and tooltips to accurately reflect connection state. |
NCCF-918408 |
| Core |
Direct Support actions missing from audit exports
Issue: Exported audit logs omitted Direct Support activity, leaving incomplete compliance records. Fix: Restored missing event mappings to ensure full reporting coverage. |
NCCF-901509 |
| Core |
Autotask time entries failed to sync
Issue: PSA time entries were rejected because the Ticket ID field wasn’t consistently passed during sync. Fix: Ensured Ticket ID is included for all Autotask time entry submissions. |
NCCF-828843 |
|
Performance & Task Reliability |
||
|
Core |
Device services sometimes showed as “stale” for several minutes
Issue: AMP-based services showed as stale for 4–5 minutes before returning to normal, confusing monitoring dashboards. Fix: Corrected status reporting so services update in real time. |
NCCF-736090 |
|
Core |
Maintenance checks delayed other system tasks
Issue: Maintenance refreshes ran too long, delaying other actions. Fix: Optimized refresh logic so tasks no longer get stuck. |
NCCF-714640 |
|
Core |
Errors when scheduling automation tasks at site level
Issue: Site-level scheduled tasks for automation returned system errors when running on AMPs. Fix: Fixed task handling so scheduled tasks run reliably. |
NCCF- 597747 |
|
Core |
Asset info update task profile not working correctly
Issue: The “Update Asset Info When Finished” task profile didn’t behave correctly when bulk asset updates were used. Fix: Adjusted the profile so asset info updates run as intended. |
NCCF-204273 |
|
Core |
System delays caused by internal counter
Issue: Partners experienced delays tied to TimeElapsedCounter wait logic. Fix: Adjusted calculation logic to remove unnecessary wait times. |
NCCF-404466 |
| Core |
Pre-upgrade memory validation failed incorrectly
Issue: Systems with 8 GB RAM were incorrectly flagged as insufficient due to unaccounted kernel-reserved memory during upgrade checks. Fix: Adjusted validation logic to correctly calculate usable memory and prevent false upgrade blocks. |
NCCF-1006162 |
| Core | Silent installer triggered device reboot
Issue: Devices rebooted automatically following silent agent installations, disrupting production environments. Fix: Added “/no restart” parameter to prevent unintended reboots after installation. |
NCCF-664567 |
| Core | XMPP roster loading froze during startup
Issue: Large XMPP rosters caused Jetty startup to stall and delay system availability. Fix: Optimized startup behavior to skip unnecessary roster synchronization and prevent thread blocking. |
NCCF-999546 |
| Core | Database lock contention in IndexKeeper
Issue: Simultaneous session updates created database lock contention, slowing performance during heavy operations. Fix: Optimized index lookups and reduced redundant writes to improve throughput. |
NCCF-980339 |
| Core |
Housekeeping jobs caused database lockups
Issue: Bulk housekeeping updates locked tables, delaying maintenance and background tasks. Fix: Implemented row-level transactions and staggered commits to eliminate contention. |
NCCF-840626 |
| Core |
All Devices view loaded slowly on large environments
Issue: The All-Devices view took several minutes to load for large customer deployments due to inefficient queries. Fix: Rewrote query joins and added caching to significantly improve performance. |
NCCF-816496 |
| Core |
Scheduled tasks recreated on licence change
Issue: License updates deleted and recreated scheduled tasks unnecessarily, causing redundant logs and delays. Fix: Refined update logic to modify only affected task records. |
NCCF-459946 |
| Core | Large report exports timed out
Issue: Exporting large reports occasionally timed out or failed due to memory limitations. Fix: Added pagination and memory-efficient streaming for reliable export performance. |
NCCF-275889 |
| Core |
Frequent asset info updates caused system load
Issue: The “Update Asset Info” job ran too frequently, generating redundant updates and extra load. Fix: Added change detection and throttling to trigger updates only when necessary. |
NCCF-284273 |
| Core |
Custom dashboard widgets not saved
Issue: User-created dashboard widgets disappeared after refresh or logout due to serialization errors. Fix: Fixed persistence logic so custom widgets remain saved and visible. |
NCCF-228667 |
|
Security & Certificates |
||
|
Core |
Password policy option not applying
Issue: The “Do not allow username-based passwords” option in Password Settings could not be enforced, weakening security policies. Fix: Fixed the password validation so the option now works. |
NCCF-649150 |
|
Core |
Outbound communication blocking did not fully apply
Issue: Outbound communications continued even after being disabled, causing unexpected data flow. Fix: Updated logic so outbound communication is fully blocked when configured |
NCCF-571471 |
|
Core |
Root certificate store created invalid entries
Issue: Upgrades built the root certificate store with invalid records, creating trust issues. Fix: Cleaned up store building process to ensure only valid records are included. |
NCCF-572685 |
|
Core |
Security and stability improvements with Jetty update
Issue: Jetty version (9.4.54) contained known issues. Fix: Upgraded to Jetty 9.4.56 to improve stability and security. |
NCCF-427410 |
| Core | Azure SSO sessions expired prematurely
Issue: Azure SSO sessions ended within minutes because token refresh intervals were not respected, causing repeated login prompts. Fix: Updated token validation and refresh logic to align with Azure’s authentication lifecycle, keeping users signed in as expected. |
NCCF-1042177 |
| Core | SSO authority URL truncated
Issue: Long identity provider URLs exceeding 120 characters were truncated, breaking SSO configuration for certain IDPs. Fix: Increased field length to 256 characters to fully support long SSO authority URLs. |
NCCF-873348 |
| Core |
Certificate upload failed when password contained “%”
Issue: TLS keystore uploads failed if passwords included special characters like %. Fix: Improved password parsing and encoding to support all valid characters. |
NCCF-923779 |
| Core |
Agent install delayed by revocation check
Issue: Online certificate revocation lookups delayed or failed agent installs and upgrades. Fix: Removed redundant CRL validation steps to accelerate installation. |
NCCF-919399 NCCF-910296 |
|
Monitoring & Data Accuracy |
||
|
Core |
Endpoint Detection & Response (EDR) status displayed incorrectly
Issue: EDR monitoring showed “No Data” in the UI even though API calls were retrieving data. Fix: Corrected UI reporting so service status is displayed accurately. |
NCCF-542099
|
|
Core |
Linux agent crash during log monitoring
Issue: On some devices, a math error made the Linux agent crash when reading logs. Fix: Fixed the error so the agent no longer crashes. |
NCCF-789878
|
| Core |
Negative memory usage displayed on small systems
Issue: Devices with ≤2 GB RAM displayed negative memory usage due to integer overflow in calculations. Fix: Corrected arithmetic logic to ensure accurate reporting of memory usage. |
NCCF-930747 |
| Core |
FACT_SERVICE_AVAILABILITY_HOUR events repeated unnecessarily
Issue: Availability events were emitted continuously even when no state change occurred, creating log noise. Fix: Revised logic to trigger events only on genuine state transitions. |
NCCF-901377 |
| Core | Windows Server Azure Edition not recognized
Issue: Azure Edition systems appeared as “Unknown OS” in Asset Inventory reports. Fix: Added SKU 0x197 detection logic to correctly identify Azure Edition servers. |
NCCF-813057 |
| Core |
Duplicate network devices discovered
Issue: Network discovery sometimes created duplicate device records when MAC addresses could not be resolved. Fix: Added LLDP-based MAC address retrieval to ensure unique device identification. |
NCCF-796118 |
| Core |
SNMP polling failed intermittently
Issue: Certain SNMP devices intermittently stopped reporting data due to socket timeout errors. Fix: Improved retry handling and socket management to stabilize polling. |
NCCF-259001 |
|
Backup & Credentials |
||
|
Core |
Backups failed when password contained special characters
Issue: Backups would fail if your FTP password had the “%” symbol in it. Fix: Backups now work even if your password includes special characters. |
NCCF-789183 |
|
Core |
ESXi login failed if credentials contained a hyphen
Issue: Logging in to ESXi failed if your username or password had a “-” (hyphen). Fix: Logins now work with hyphens in usernames and passwords. |
NCCF-709175 |
|
MSAD |
AM Agent crash on app domain unload
Issue: The AM Agent crashed when the AppDomain was unloaded with unhandled exceptions. Fix: Stabilized the unload process to prevent agent crashes. |
MSAD-5149 |
|
MSAD |
Misconfigured services due to AM Engine unload
Issue: Unloading the AM Engine app domain caused service misconfigurations and agent instability. Fix: Adjusted handling during unload to avoid misconfiguration. |
MSAD-5148 |
| MSAD |
AM Engine AppDomain unload causes service misconfiguration
Issue: When the AM Engine unloads its AppDomain, certain services are left misconfigured, causing instability. Fix: Updated unload sequence to preserve configuration and clean up resources. |
MSAD-5252 |
| UI and Notifications | ||
| Core |
Email notifications showed garbled subject text
Issue: Alert emails containing non-ASCII characters displayed unreadable subjects due to encoding errors. Fix: Implemented UTF-8 header encoding for all outbound notification emails. |
NCCF-217884 |