Data Breach Risk Scan Report for Individual Host
The Data Breach Risk Scan combines the Data Discovery scan and the Security scan to search your device(s) for security vulnerabilities and sensitive data including credit card numbers, driver license numbers etc. The Scan Results report shows:
- Unprotected Data Summary - Graph shows Unprotected Data Count by Type (e.g credit cards, dates of birth, driver licenses, social security numbers etc.). You can also see:
- Elapsed Time for the scan - The amount of time the scan took to run.
- Number of Files Scanned - Total number of files scanned.
- Number of Files with Violation - The number of files containing findings (credit card instances, social security numbers etc.).
- Number of Total Violations - The total number of unique findings (credit card instances, social security numbers etc.) found in the Number of Files with Violation.
- Potential Liability - The potential liability of the unprotected data found. For information about configuring potential liability, see the Account Info Tab
- Vulnerability Summary - Shows vulnerability count by vendor.
- Unprotected Data Details - Lists files with unprotected data. In this section you can:
- Focus on particular data by using the filters at the top of the panel: Bank details, Cards, Date of Birth, Licenses and Social Security numbers.
Any filters set only apply to the current session. If you leave the page, your filters are not retained and you will need to re-select them.
When you choose to download the PDF or CVS files, any filters are ignored and the full unfiltered data is downloaded.
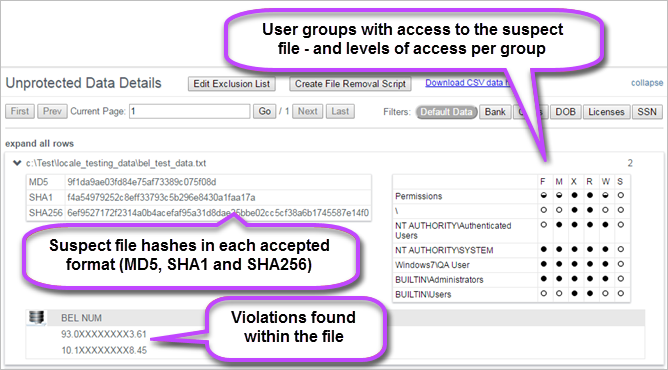
- Expand files to view: the file hash for the file in each of the hash formats (MD5, SHA1 and SHA256); a table containing the user groups that have access to the file (and what level of access they have - see View Suspect Data File User Access Permissions); a list of the violations found in the file.
The listed, violated files are masked. No unmasked data leaves the system that is scanned.
- Create File Removal Script to Delete Unprotected Data Files from Device
- Exclude Files from Data Scans on Individual Hosts
- Unprotected Data Scan Statistics - Displays the time it took to run the scan, volumes scanned, number of files scanned, number of files with suspect data, suspected instances found etc.
- Vulnerability by Vendor Details - List of vulnerabilities by vendor and instructions on how to fix. Click on a vulnerability to view details.
- Vulnerability Details - List of vulnerability details and instructions on how to fix.
- Network Port Details - Displays listening TCP/IP ports on your system. Listening ports indicate that a service is listening for external communication from a remote computer.
- Review the list of open ports to determine if they are absolutely necessary.
- Disable any unnecessary services to reduce the risk of compromise from malware or attackers. We recommend that you back up your system before making any changes.
- Your local IT administrator will be able to provide you with guidance on managing your network ports.
