View Suspect Data File User Access Permissions
When our scans pick up suspect data, you can see which files are affected and who has access to them.
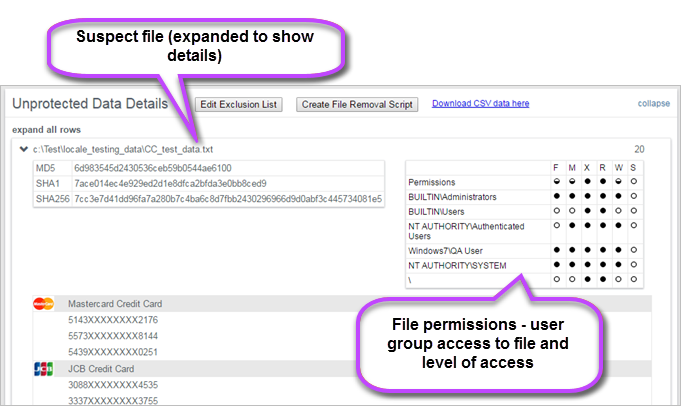
To find out which user groups have access to suspect data files - and the level of access they have - you need to look at the Scan Results report for individual hosts.
The following scan types reveal this information:
- Data Breach Risk scan
- Data Discovery scan
- PAN scan
- PCI and PAN scan
- File Finder scan
- Go to View and Manage - Scan Results.
- Find the scan you want to check and double-click to open.
- Expand the Unprotected Data Details panel and expand the suspected file to view the Permissions table.
- F - Full
- M - Modify
- X - Execute
- R - Read
- W - Write
- S - Special - Windows-only permission
|
The Permissions table displays which user groups have access to the suspected data, and what access rights they have. The following lists all available access types:
- Half circle means that at least one of the users in the group has access at that level - Full circle means that all users in the group have access at that level |