Roles and permissions
You assign user roles to users to customize their N-sight RMM access . You can use the default system roles, or you can create your own roles to meet your requirements. For example, you can create feature specialist roles, roles for the finance team, or basic roles for contractors.
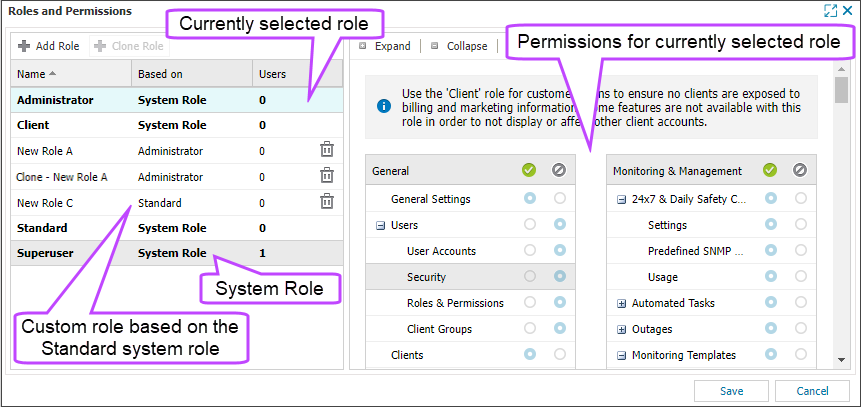
You can edit and delete roles that you have added as your user role needs change.
To manage roles, you must be signed into N-sight RMM using an Agent Key, a Superuser role , or a user account with the Roles & Permissions permission enabled.
The Roles and Permissions dialog lists the currently configured roles in the left panel. When a role is selected in the left panel, the permissions for the selected role display in the right panel. In the list of roles, you can see if the role is a system role, or if it is a role you added.
You can manually resize the Roles and Permissions dialog using the cursor on the edge of the dialog, and you can resize the panels by placing the cursor on the panel divider and move it right or left.