Protection Policy: Scanning
Quick and Deep Scans are an intrinsic part of Managed Antivirus protection. This section covers the overall scan behavior of these 2 scan types, with the specifics of each of the scan types detailed in Protection Policy: Quick Scan and Deep Scan.
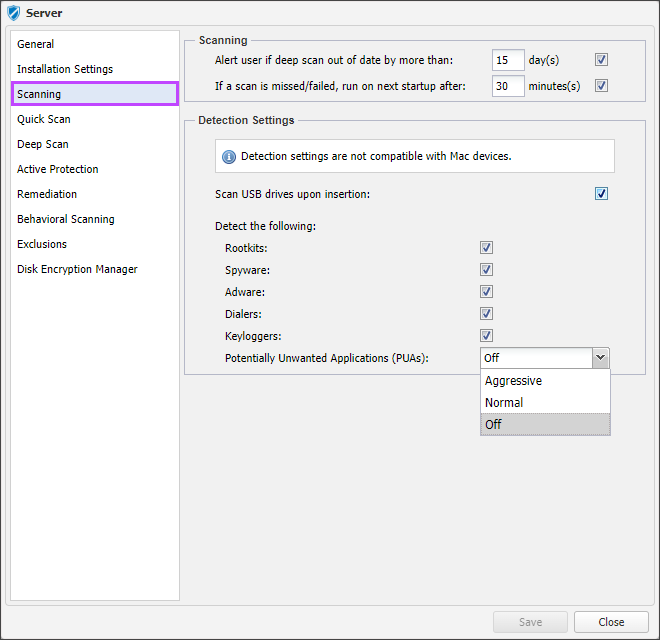
Scanning
To ensure deep scans have taken place, the policy contains the option to Alert user if deep scan out of date by more than n day(s). Enter the threshold and tick the box to apply.
Exceeding this threshold generates an alert on the Dashboard and in the agent console. Where End-User Interaction > Show Notification is enabled in the policy's Protection Policy: General section.
In the event a device is offline when the scheduled scan is due or some other event causes a scan to be missed, Managed Antivirus can be set to run the scan after the next startup of the device. Tick the box to enable the option If a scan is missed, run on next startup after n minute(s) and enter a suitable duration to apply.
To reduce the device’s threat exposure you can opt to Scan USB drives upon insertion, tick the box to enale.
Allow adequate time for the computer to start and download the latest definition files.
Detection Settings (Windows only)
Configure Managed Antivirus to Detect the following threat types during a scan. Tick the box next to each in the Protection Policy to enable.
Detection Settings are not compatible with Mac devices.
| Threat Type | Notes | ||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
Rootkits |
The main role of rootkits is to hide processes, files, logins and logs. They may also intercept data from terminals, network connections or peripherals, if they incorporate the appropriate software. Rootkits are not malicious in nature. For example, systems and even some applications hide critical files using rootkits. However, they are mostly used to hide malware or to conceal the presence of an intruder into the system. When combined with malware, rootkits pose a great threat to the integrity and the security of a system. They can monitor traffic, create backdoors into the system, alter files and logs and avoid detection. |
||||||||||||||||
|
Spyware |
Any software that covertly gathers user information through the user's Internet connection without his or her knowledge, usually for advertising purposes. Spyware applications are typically bundled as a hidden component of freeware or shareware programs that can be downloaded from the Internet. Once installed, the spyware monitors user activity on the Internet and transmits that information in the background to someone else. Spyware can also gather information about email addresses and even passwords and credit card numbers. Spyware's similarity to a Trojan horse is the fact that users unwittingly install the product when they install something else. Spyware steals from the user by using the computer's memory resources and also by eating bandwidth as it sends information back to the spyware's home base via the user's Internet connection. Because spyware is using memory and system resources, the applications running in the background can lead to system crashes or general system instability. |
||||||||||||||||
|
Adware |
Adware is often combined with a host application that is provided at no charge as long as the user agrees to accept the adware. Because adware applications are usually installed after the user has agreed to a licensing agreement that states the purpose of the application, no offence is committed. However, pop-up advertisements can become an annoyance, and in some cases degrade system performance. Also, the information that some of these applications collect may cause privacy |
||||||||||||||||
|
Dialers |
Dialers, as the name implies, are designed to dial an expensive premium rate number instead of the number used to connect with the ISP. This type of threat is primarily designed to target dial-up connections. |
||||||||||||||||
|
Keyloggers |
A keylogger is an application that logs anything typed by the user. Keyloggers are not malicious in nature. They can be used for legitimate purposes, such as monitoring employees or childrens activity. However, they are increasingly being used by cyber-criminals for malicious purposes (for example, to collect private data, such as login credentials and social security numbers). |
||||||||||||||||
|
Potentially Unwanted Applications (PUAs) |
PUAs are unwanted programs that can come bundled with free software and display pop-ups, install toolbars in the default browser, change the homepage or search engine. PUAs can also run processes in the background slowing down the device's performance. Select the required level of detection from the drop-down. Aggressive, Normal or Off
|
What do you want to do?
- Review the Managed Antivirus Quick Start Guide
- View Managed Antivirus URLs
- Enable Managed Antivirus on individual servers and workstations or on all servers and workstations at a client or site