Security Scan
The Security Scan Report contains the vulnerability results for the selected device, exposing the operating system and installed application security risks.
Device details
Shows the assessment completion time, host name, IP address, and platform. To export the report, select. the PDF version button.
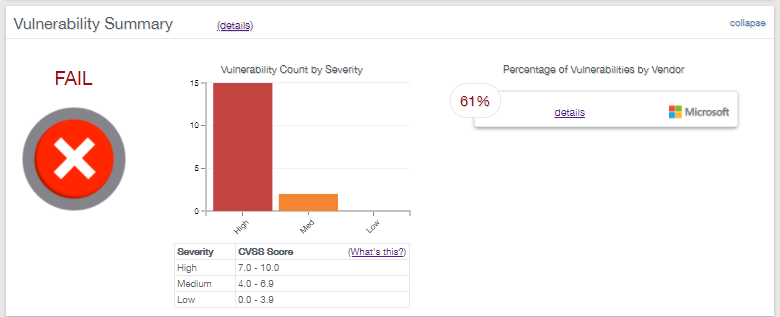
Vulnerability Summary
The Vulnerability Summary graph shows the vulnerability count by severity based on the Common Vulnerability Scoring System (CVSS) with each vulnerability assigned a severity of High, Medium or Low and percentage of vulnerabilities by vendor.
To break down this information click, on the details links to take you to the "Vulnerability Details" sections.
Details about Scoring
A vulnerability with a High level of severity will fail PCI compliance whereas vulnerabilities with Medium or Low severity levels will generally pass PCI compliance.
- High: 7.0 - 10.0
- Medium: 4.0 - 6.9
- Low: 0.0 - 3.9
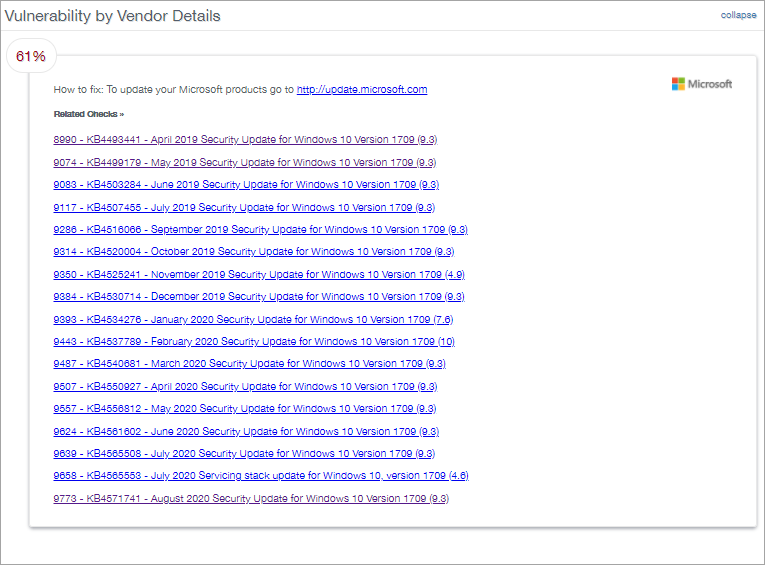
Vulnerability by Vendor Details
Lists the vulnerabilities discovered by vendor click on a vulnerability in this section to go to its entry in the Vulnerability Details section. This list details of the discovered vulnerabilities along with links to external sites that with instructions on how to alleviate the issue.
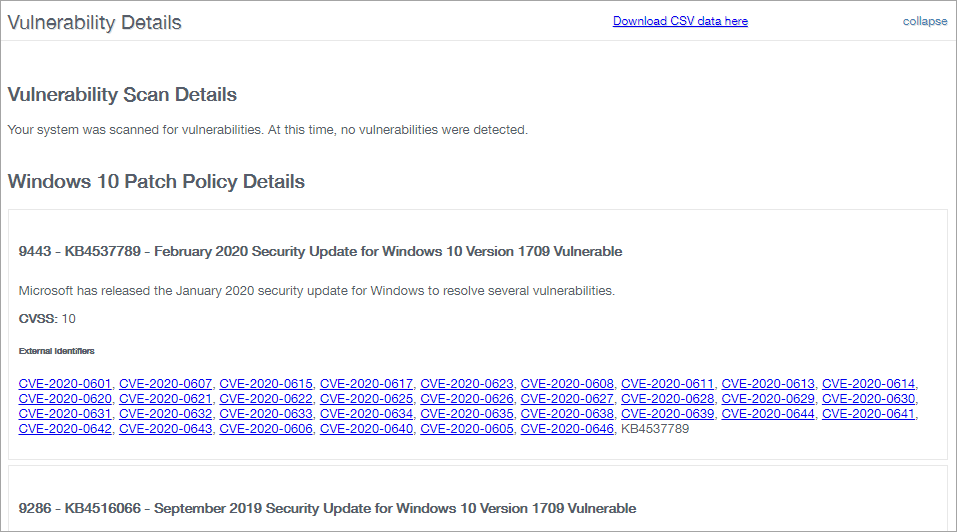
Vulnerability Details
List details of the discovered vulnerabilities along with links to external sites with instructions on how to alleviate the issue.
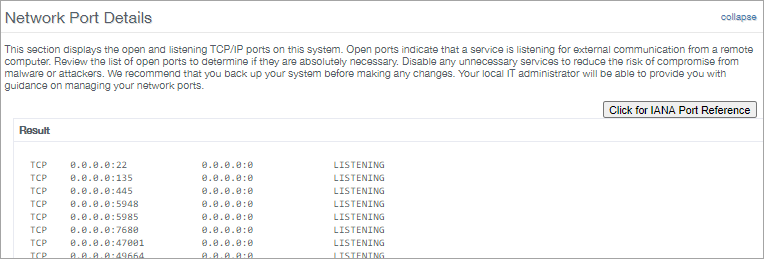
Network Port Details
Displays the listening TCP/IP ports on your system. These listening ports indicate that a service is listening for external communication from a remote computer.
From here you can review the list of open ports, determine if they are required and disable any unnecessary services to reduce the exposure to compromise from malware or attackers.
We have also included a button to open the Internet Assigned Numbers Authority at the service name and port numbers page.
Please note, we are not responsible for the content of external sites.
What do you want to do?