Event Log Check
The Event Logs are repositories of information that have detailed data on the status of the system written to them by applications and Windows components.
The Event Log Check monitors the Event Logs and can be configured to query a specific Event Log based on the following indicators Event ID, Event Type, Event Source and Description. Alerting where the specified information is, or is not, discovered in an Event Log entry.
Multiple Event Log Checks may be created on the same device for both 24x7 (business critical events you wish to be alerted to as soon as they occur, for example license failures, virus detection etc) and Daily Safety Checks (for example a backup job has completed or an Antivirus program updated).
For Application and Security Event Logs the Event Log Check only retrieves information from the root level, it does not query any sub-level logs.
Add
- In the All Devices view North-pane, select the device
- Go to the Checks tab
- Click Add Check
- Choose Add 247 > Event Log Check
- Configure settings
- To run an Automated Task when the Check fails choose Assign a Task after creating the Check
- OK to save and apply
- Where Assign a Task after creating the Check is selected:
- Select the script
- Click Next to configure
- Enter the Command Line parameters (if required)
- Set a Script timeout in the range 1 - 3600 seconds (default 120 seconds)
- Click Finish to save and apply
Edit
- In the All Devices view North-pane, select the device
- Go to the Checks tab
- Select the target Event Log Check
- From the Check drop-down
- Click Edit Check (also available from the Check's right-click menu)
- Configure the settings
- Click OK to save and apply
Delete
- In the All Devices view North-pane, select the device
- Go to the Checks tab
- Select the target Event Log Check
- From the Check drop-down
- Click Delete Check (also available from the Check's right-click menu)
- Review the summary and select OK to confirm removal
Event Log Check Settings
Descriptive Name
Give the check a meaningful name for identification on the All Devices view as well as in Alerts and Reports.
Event Log to check
Select the target Event Log from the dropdown menu.
The Agent automatically detects the installed Event Logs and uploads this information to the All Devices view.
Alert when
This threshold determines when an alert is generated. Choose to Alert when the Log contains or Log does not contain the following information:
Event ID(s)
The identification number associated with the Event. Identification numbers may be specific to one Event or associated with multiple different Events. This field supports comma separation when entering multiple Event IDs.
Event Type
Indicates the severity associated with the Event Log entry. The Check supports the five Windows Event Log Types (Information, Error, Warning, Success Audit and Failure Audit) along with the custom Success/None Event Types used by some vendors to indicate the completion of a job. Any combination of these Event Types may be used in the Check.
- Information: Describes the successful operation of an application, driver, or service.
- Error: Indicates a significant problem such as loss of data or loss of functionality.
- Warning: Signals that the event itself is not necessarily significant, but that it may indicate a possible future problem.
- Success Audit: Records a successful audited security access attempt.
- Failure Audit: Records an unsuccessful audited security access attempt.
- Success/None: Indicates the completion status (custom Event Type).
Event Source
The application or Windows component that generated the Event.
Message contains string
The Event Description may contain information on specific problems or the application’s status. Configure the Check to search for specific text within the Event description to monitor its state.
The Check supports wildcards * in the Event ID(s), Event Source and Message contains string to search for any entries in these fields. For example, drive * failed in Message contains string.
Event Exclusion
The Windows Agent supports the following settings when configuring the Event Log Check from the All Devices view.
- Apply Critical Events Exclusion List: Tick this box to ignore those Events already entered in the Critical Event Exclusion list where discovered as part of the Event Log Check.
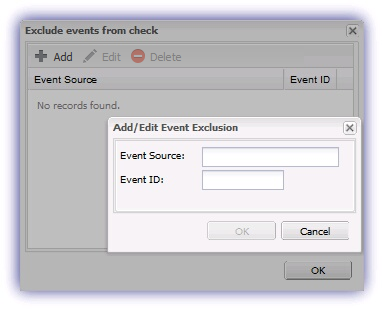
- Exclude Events from Check: An exclusion list can be created for the specific Event Log Check.
Select Exclude Events from Check > Add then enter the Event Source and Event ID to ignore.
The dialog also includes the option to manage the Exclusion List for this specific Event Log Check. Highlight the required entry then select Edit or Delete to amend as required.
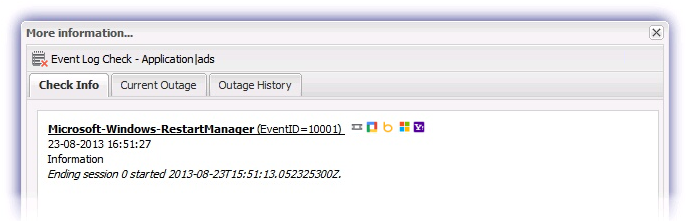
More information
After the Check results are uploaded to the N-sight RMM user interface, details of the output can be viewed in the More Information section along with links to the following resources for further information on the Event: EventID.net, Google, Bing, Microsoft or Yahoo.
The time and date recorded for the discovered Event is based on the local time of the device and not your N-sight RMM timezone.