Take Control Security Guide
Introduction
N-able's Take Control is a remote support platform that prioritizes security to ensure the safety and integrity of remote sessions. The platform includes a range of features designed to protect both the technician and the end-user, making it a trusted choice for managed service providers (MSPs) and IT professionals.
One of the key security features of Take Control is its use of end-to-end encryption for all remote sessions. This encryption ensures that data transmitted between the technician and the remote device is secure and cannot be intercepted by unauthorized parties. The platform also supports multi-factor authentication (MFA), adding an extra layer of security by requiring users to verify their identity through multiple methods.
Take Control's security architecture includes robust access controls and permissions. Administrators can define user roles and permissions, ensuring that only authorized personnel have access to sensitive information and remote sessions. The platform also provides detailed audit logs and session recordings, allowing administrators to monitor and review remote support activities for compliance and security purposes.
In addition to these features,Take Control integrates with various security information and event management (SIEM) systems, providing enhanced visibility and control over security events. This integration allows MSPs to detect and respond to potential threats more effectively, ensuring the security of their clients' IT environments.
With its comprehensive security features,N-able's Take Control helps MSPs and IT professionals deliver secure and reliable remote support, protecting both their operations and their clients' data.
Purpose and target audience
Purpose
The purpose of this document is to provide a comprehensive overview of the security architecture of Take Control (N-able). This document aims to inform Managed Service Providers (MSPs) and IT professionals about the security features, protocols, and best practices embedded within the Take Control solution. By understanding the security architecture, stakeholders can better appreciate how the solution safeguards client systems, ensures compliance with industry standards, and mitigates potential security risks.
Target Audience
This document is intended for MSPs and IT professionals who are responsible for the deployment, management, and support of remote access solutions within their organizations. The target audience includes:
-
IT Managers and Directors: Individuals overseeing IT operations and strategy, who need to understand the security capabilities and benefits of N-able Take Control .
-
System Administrators: Professionals responsible for the day-to-day management and maintenance of IT systems, who require detailed knowledge of the solution's security architecture to ensure system integrity and protection.
-
Security Analysts: Experts focused on identifying and mitigating security threats, who need to understand how N-able Take Control addresses potential vulnerabilities and ensures robust system security.
-
Compliance Officers: Individuals responsible for ensuring that organizational practices meet regulatory requirements, who need to understand how N-able Take Control supports compliance with data protection standards.
-
Technical Support Engineers: Personnel providing frontline support to end-users, who need to be familiar with the solution's security features and troubleshooting procedures.
By addressing the needs and concerns of these key stakeholders, this document aims to facilitate informed decision-making and effective implementation of Take Control's security measures within diverse IT environments.
Significance of Security in today’s digital era
Security is incredibly significant in today's digital era due to the increasing reliance on technology. A robust security framework safeguards personal information, protects against cyber threats, protects critical infrastructure thereby ensuring business continuity to prevent financial loss and maintain reputation.
N-able offers a comprehensive array of security features across all its products for MSPs. Take Control, one of the compelling products of N-able, provides an extensive suite of security mechanisms for MSPs through its robust features and standards.
Take Control Key Security Features
-
Multi-Factor Authentication (MFA) and Single Sign-On (SSO) enhance security and user experience by reducing the risk of unauthorized access and simplifying login processes
-
Effective security logging helps maintain the integrity and security of systems thereby helping the MSPs detect and respond to threats promptly through validating any dangerous characters, logging the timestamp, and identifying security incidents
-
Data encryption ensures confidentiality, integrity, and availability of data against cyberattacks and threats
-
Role-level access control (RBAC) lets MSPs grant limited access as needed, secured with mandatory two-factor authentication (2FA)
-
SO-certified data centers located worldwide ensure security, reliability, and operational excellence
-
Network Security framework protects the infrastructure servers with high-availability firewalls and the servers are continuously monitored to detect and prevent various network security threats
-
Cyber Resilience defends against ransomware, phishing, malware, and insider threats thereby reducing the risk of data breaches and ensuring business continuity
-
Communication is protected securely by CloudFlare and is encrypted in transit leveraging Transport Layer Security (TLS)
-
Threat Intelligence enables monitoring and mitigating security threats, including Distributed Denial of Service (DDoS) attacks, Structured Query Language (SQL) injections, and cross-site scripting (XSS)
-
Real-time Analytics provide comprehensive reporting and dashboards that allow us to monitor and respond to attacks in real-time
Take Control Security Standards
Authorization (Access Control) and Authentication
Take Control’s authorization features ensure data privacy and system integrity through granting or denying specific requests to the MSP, program, or process. All requests go through some kind of authorization verification layer and only the authorized MSPs are provisioned with unique account IDs. Access is assigned based on pre-defined roles as per Role-Based Access Control (RBAC).
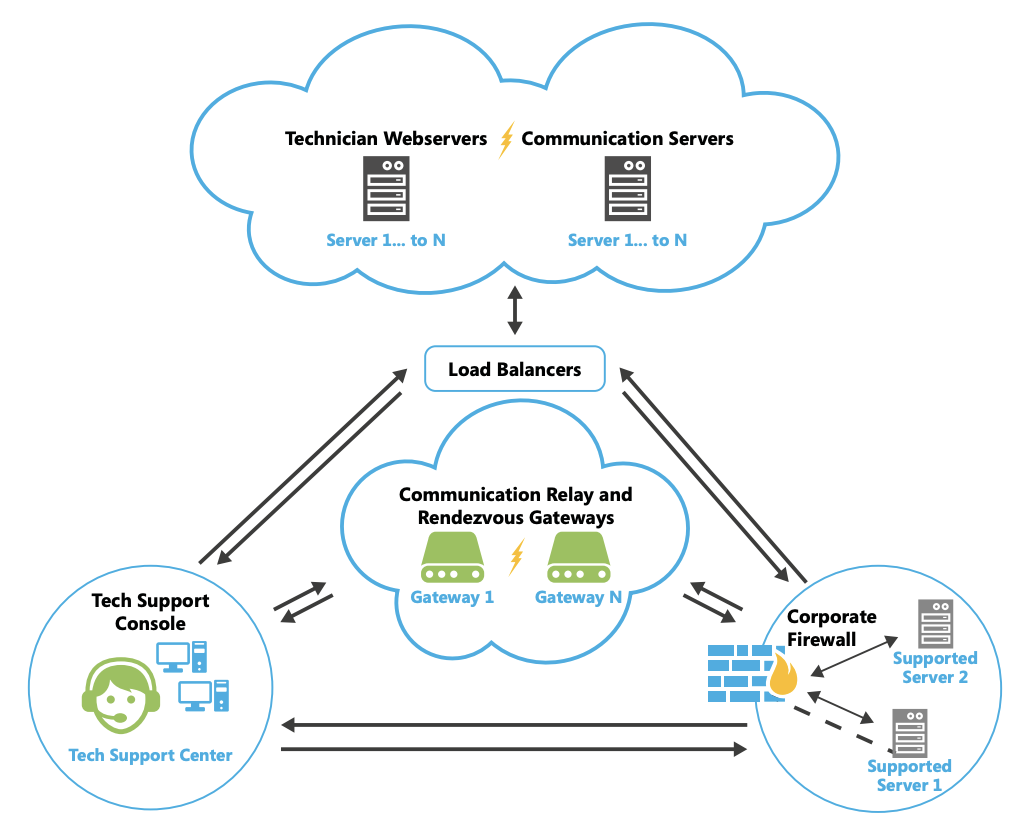
Take Control’s authentication features prevent unauthorized access through the reduced risk of identity thefts, fraud, and cyberattacks, thereby enhancing security and MSPs trust. Multi-factor Authentication (MFA) mandatory Two-Factor Authentication (2FA) protect against unauthorized use of passwords thereby providing an extra layer of security beyond traditional password protection. Furthermore, the password policy covers all applicable information systems, applications, and databases and enforces best password practices. All actions performed by users are be authenticated and authorized. The following is the authentication workflow that Take Control follows:
Security Overview
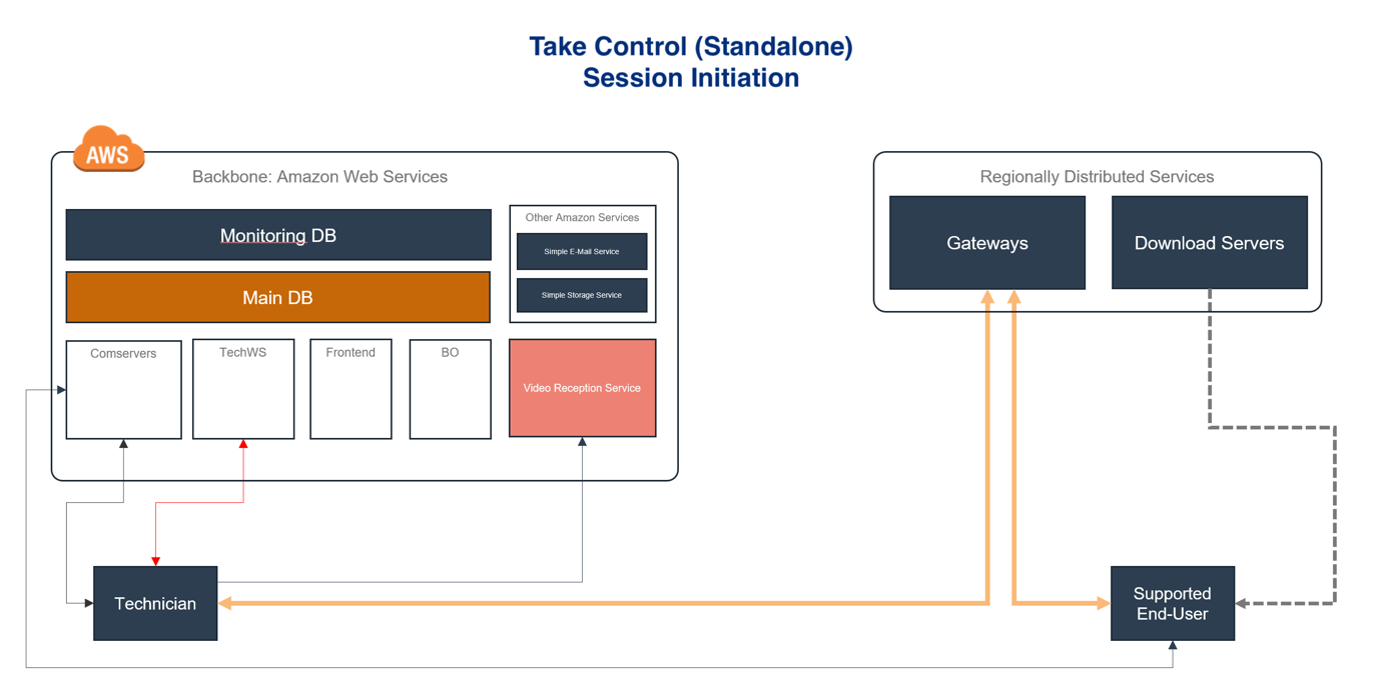
In this diagram for Standalone Take Control accounts, the Take Control technician reaches out to TechWS to obtain a list of all devices, then connects to the Comserver to obtain the correct device information. From here, the gateway initiates the connection to the target device and begins the session.
The device (in this case described as the "Supported End-User") uses the Download Server to download/update the agent, and communicates with the Comserver to register itself and send the regular heartbeats to the platform. At the same time receives the gateway to connect to and waits for a connection.
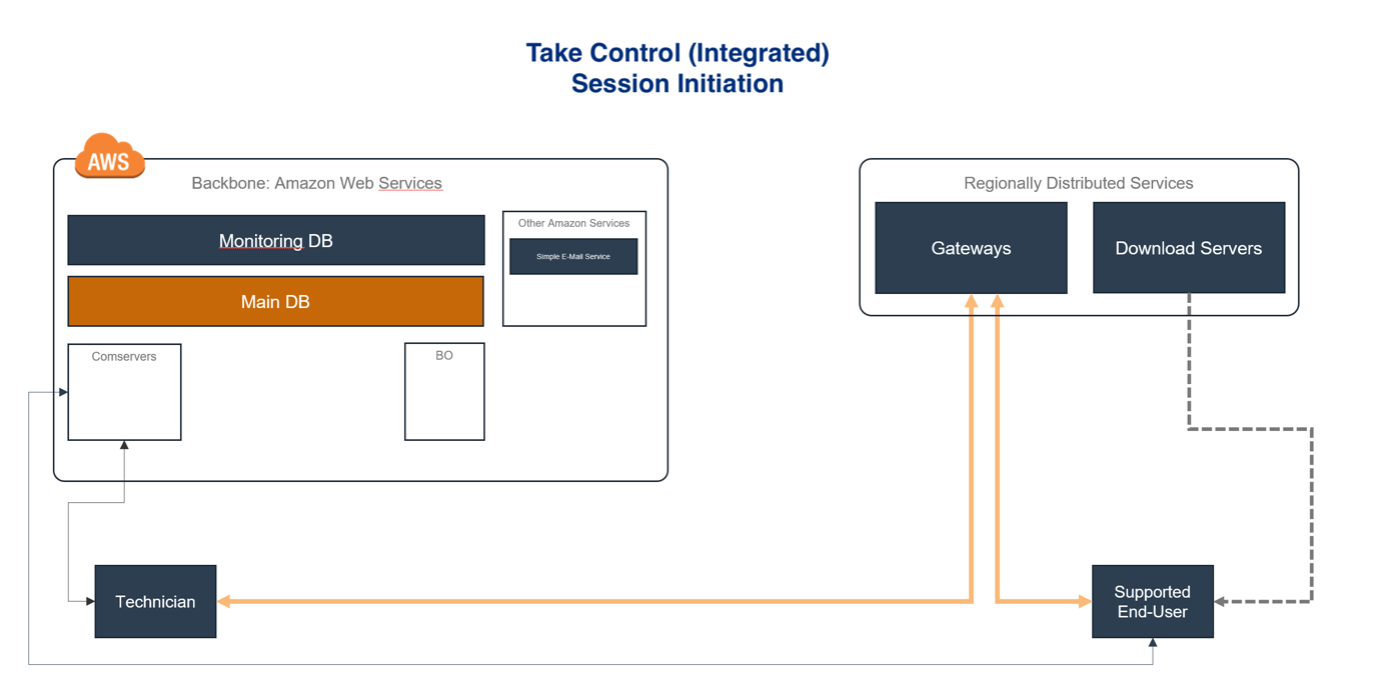
This diagram shows the session initiation for integrated Take Control accounts. Here and different from standalone connections, there is no TechWS. Instead, the device list is in N-sight. Prior to beginning the session, the technician receives a link, which is used to migrate directly to the Comserver, get the respective gateway, and then the process to launch the support session is very similar to the Standalone connection process.
Secure Communication
All the features available during Take Control remote support sessions are sheltered by a proprietary communication protocol encrypted by AES-256 CTR + HMAC-SHA256 and a Diffie–Hellman ephemeral key exchange. This feature is active when establishing or during the support session.
Take Control uses its own proprietary protocol to coordinate and control its features. Messages are transmitted over standard Internet protocols, primarily HTTPS (HTTP over SSL/TLS).
As an additional security measure, all commands containing images, keyboard and mouse strokes, file transfers and clipboard information are digitally signed. Take Control has no access to the sessions’ content, since all encryption is based on an end-to-end negotiation, which leaves no room for intercepting the transferred information nor decoding it in the gateway.
Most connections are outbound from the perspective of the End Point, maximizing compatibility with production environments. Take Control utilizes the following ports and protocols:
-
TCP over port 443: Mandatory for communication.
-
TCP over port 3377: Alternative for communications between End Points and the assigned Gateway server.
-
User-configurable port: For P2P connections within the same LAN.
-
UDP over a random port: For P2P connections over the Internet, once UDP availability is confirmed.
-
TLS/HTTPS over port 443: Optional for End Point to Gateway communications.
-
SSL/TLS Inspection: Any security solution scanning the contents of Take Control ’s HTTPS connections will prevent it from working. Exceptions for Take Control ’s traffic on any SSL/TLS/HTTPS Inspection filter/engine are required.
Encryption key
Take Control utilizes the following modules to facilitate communication between the technician (Viewer) and remote devices (Applet or Agent). The encryption keys are randomly generated for each remote session between the Viewer and the Applet, or the Take Control Agent. As an additional security measure, the partner can configure a Master-Password (saved only in the Agent) or choose Windows Account authentication, as well as requiring a previous authorization for the machine user to launch the session. All the actions performed during the sessions are logged, and video recording can be made mandatory. Additionally, any session performed to a Windows device will be registered in the machine’s Event Viewer.
Network Security
Take Control ensures cutting-edge network security by monitoring and controlling incoming and outgoing network traffic. The Next Generation Firewalls (NGFWs) installed in the data center and at remote office locations monitor outbound communications for abnormal or unauthorized activities, which may indicate the presence of malware (e.g., malicious code, spyware, adware). NGFWs have been designed to provide network segmentation through the establishment of security zones to control the flow of network traffic and to restrict access to systems from external networks and between internal systems. Additionally, automated tools are implemented within the network to facilitate near-real-time analysis of events for detecting system-level attacks.
Redundancy
Take Control ’s infrastructure is Built on a failure-tolerant, geographically distributed, and redundant architecture. Monitored 24/7 through automated resources and human resources. It’s ventral servers are located in three different and redundant locations hosted on AWS. Coordinate session establishment and connection to technicians. Gateways are assigned based on country and geographic proximity, automatically replaced by an alternative connected gateway if unavailable
Cyber Resilience
N-able’s cyber resilience strategy is vital for business continuity as it provides the MSPs with an ability to prepare for, respond to, and recover from cyber threats with the aim to reduce the chances of financial loss and reputational damage. MSPs must be prepared to recover their operations in a rapid and efficient manner despite operational interruptions from cyber incidents.
Anomaly Detection
N-able’s support proactively notifies MSPs when anomalies are detected to save time and start recovery process as early as possible. Take Control ’s anomaly detection mechanism monitors suspicious API calls which are outside of the pattern of normal system behaviour. The continuous monitoring of anomalies enhances overall data security thereby augmenting MSPs trust and satisfaction, operational efficiency, and competitive advantage.
Incident Response
Take Control ’s security Incident Response Plan (IRP) help MSPs to detect, respond to, and recover from cybersecurity incidents. The primary goal of an IRP is to minimize the impact of security incidents for any organization. Take Control ’s well-defined IRP helps MSPs protect their data, reduce recovery costs, minimize damage, and improve overall security posture through detection and analysis, eradication, recovery and post-incident activity.
Penetration Testing
N-able’s products including Take Control undergo an annual external penetration test by a certified third party. Additionally, a thorough internal penetration test is mandatory before releasing any major feature or application. Network penetration tests are also performed annually or after significant changes.
Compliance and Data Sovereignty
N-able’s security compliance adheres to implementing policies, controls, and best practices to protect sensitive data and meet regulatory requirements. N-able products including Take Control comply with various security frameworks to prevent data breaches, mitigate risks, and sustain MSPs trust. Physical security and power continuity are maintained through partnerships with leading data center providers, featuring rigorous security measures and redundant systems.
Data Center certifications include the following compliances to demonstrate adherence to:
-
HIPAA - Strict privacy and security standards for Data Protection
-
FIPS - Standards set by NIST to ensure security and interoperability in U.S. government computer systems.
-
ISO27001 - Best practices and comprehensive security controls
-
ISO9001 - Framework for Quality Management System (QMS)
-
NIST 800-53 - Comprehensive catalogue of security and privacy controls for information systems and organizations
-
PCI-DSS - Robust security measures reducing the risk of data breaches and cyber attacks
-
SOC 1 Type II and Soc 2 Type II - Stringent information security controls across its services
-
Mandatory 2FA - Powerful security measure with an additional verification step
Summary
Security is an ongoing process, a multi-layered approach combining technologies, policies, and user awareness. Take Control's Security framework outlines the best standards for securing applications, infrastructure, and data against evolving cyber threats covering authentication and authorization mechanisms, encryption processes, incident response planning, network security controls, cyber resilience, and compliance requirements. By implementing Take Control ’s strong security measure, the MSPs can protect sensitive data, prevent breaches, and maintain compliance with industry standards.
Appendices
N-able FIPS 140-2 Compliant Components Letter
Communication and Security Statement from the N-sight User Guide