Failed Login Check
On Windows devices, the Failed Login Check queries the Windows Security Event Log to identify the total number of unsuccessful login attempts on the monitored device over the past 24 hours. If the number of discovered Events exceeds the configured threshold, the Check fails.
The Windows Agent searches for the following Events in the Windows Security Event Log:
| Event ID | Failure Type |
|---|---|
| 4625 | An account failed to log on |
| 4768 | A Kerberos authentication ticket was requested (when type failure) |
| 4772 | A Kerberos authentication ticket request failed |
| 4771 | Kerberos pre-authentication failed |
| 4776 | The domain controller attempted to validate the credentials for an account |
| 4777 | The domain controller failed to validate the credentials for an account |
The Failed Login Check returns data on the IP address and user name associated with the attempted login. The aggregated data is only available for the latest one hundred entries recorded over the monitored period with any number above this simply counted.
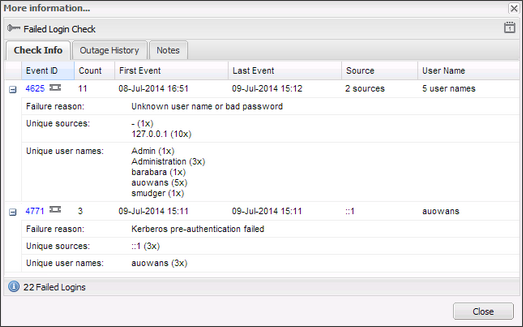
Check results are available in the South-pane Checks tab. The More Information column displays the total number of Failed Logins recorded over the last 24 hours. Click the link in the More Information column for information on the cause of the failures.
The More Information dialog lists a summary for each discovered event. Click the Event plus button (+) for detail on the failure.
| Field | Description |
|---|---|
| Event ID |
Failure Event ID with link to EventID.net for more Event type information |
| Count | Total number of instances of the Event |
| First Event | Date and time of first Event |
| Last Event | Date and time of last Event |
| Source | IP address the attempted login originated from, if known. If there are multiple IP addresses the number of Sources is returned. |
| User Name | User name associated with the attempted login. If there are multiple users, the number of User names is returned. |
| Failed Logins | Total number of Events recorded |
| Failure reason | Cause of the failed login attempt |
| Unique sources | IP address the attempted login originated from, if known. Includes the number of occurrences of this Event the IP address is associated with. |
| Unique user names | User name linked to the attempted login. Includes the number of occurrences of this Event the user name is associated with. |
Check configuration
Add
- In the All Devices view North-pane, select the device
- In the South-pane Checks tab, click Add Check
- Select Add DSC > Failed Login Check
- Enter the Threshold
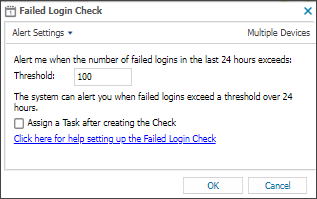
When you set the threshold for the Failed Login Check, we recommend you decide how many failed attempts constitutes an abnormal amount.
Work with your customer to determine a suitable number of failed logins as a baseline, and configure the threshold such that if the baseline is exceeded, the check fails and sends an alert. - To run an Automated Task when the Check fails, choose Assign a Task after creating the Check
- Click OK to save and apply
If you selected Assign a Task:
- Choose the Automated Task script.
- Select Next to configure parameters.
- Enter any required Command Line or Script parameters.
- (Optional) Set maximum permitted execution time for the script.
- Select Finish to save and apply the task.
Edit
- In the All Devices view North-pane, select the device
- Go to the Checks tab
- Right-click the target Failed Login Check and select Edit Check
- Edit the settings
- Click OK to save and apply
Delete
- In the All Devices view North-pane, select the device
- Go to the Checks tab
- Right-click the target Failed Login Check and select Delete Check
- Review the summary and select OK to confirm removal