Enabling and Disabling Disk Encryption Manager in the Managed Antivirus Protection Policy
Disk Encryption Manager is enabled and disabled via the Managed Antivirus Protection Policy.
How to Enable Disk Encryption Manager in the Managed Antivirus Protection Policy
Once logged into N-sight RMM:
- In the All Devices view, select Settings > Managed Antivirus > Protection Policy
- Either create a New policy or Edit an existing one
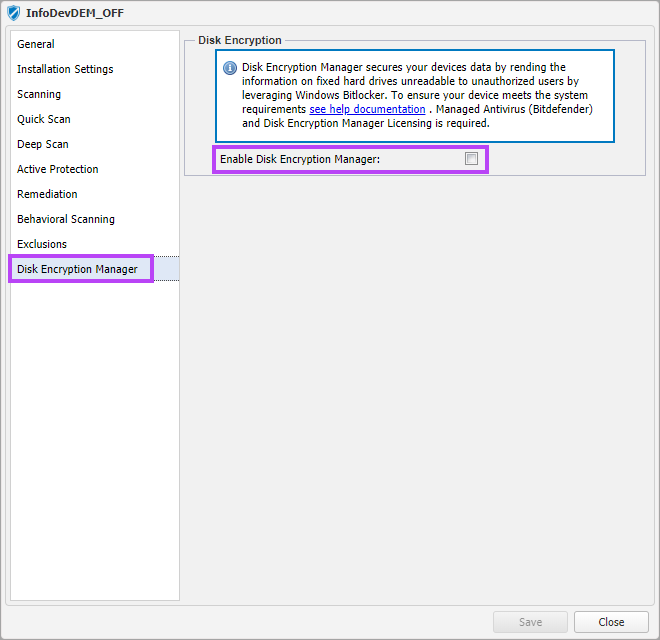
- In the policy dialog, select Disk Encryption Manager in the left-pane
- By default, Disk Encryption Manager is disabled, tick the Enable Disk Encryption Manager tick box
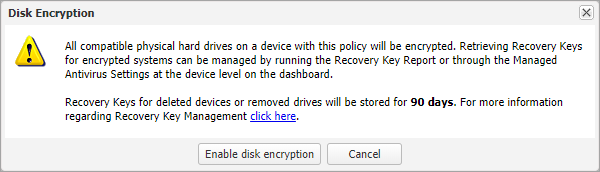
- An advisory warning appears, read through this so you fully understand the action being taken and then click Enable disk encryption
- A new section for Trusted Platform Chip Module will appear in the policy. If required, click to tick the Prompt user for PIN during pre-boot. This is the configuration recommended by Microsoft as per their advice: BitLocker Security FAQ
- If you have created a new policy, the remaining settings for the other sections can be configured by following Bitdefender Engine - Protection Policies
- Once you have completed the policy configuration, click Save to save the configuration and close the dialog
How to disable Disk Encryption Manager in the Managed Antivirus Protection Policy with or without Decrypting
- Select Settings > Managed Antivirus > Protection Policy
- Either double-click the target policy or highlight it and select Edit
- In the policy dialog, select Disk Encryption Manager in the left-pane
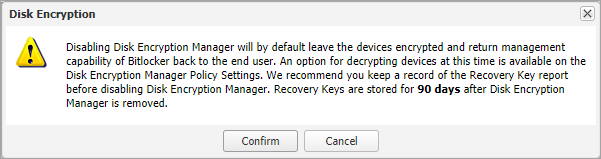
- Untick the Enable Disk Encryption Manager tick box
- An advisory warning appears, read through this so you fully understand the action being taken and then click Confirm
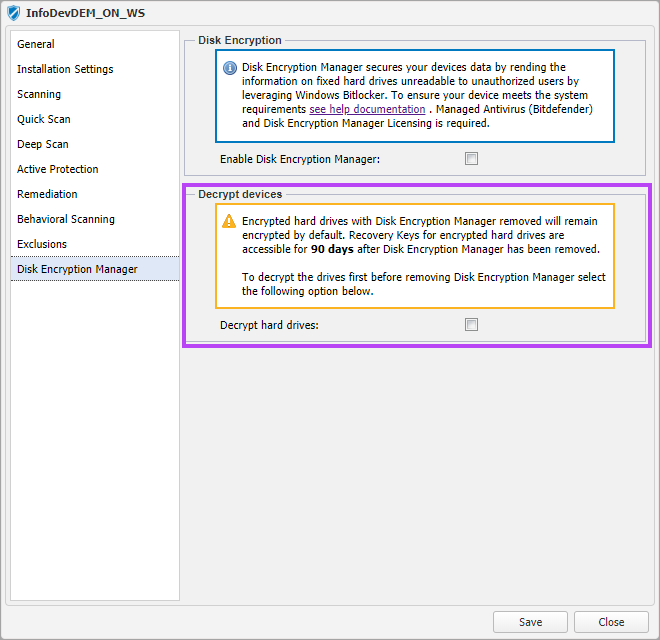
- A new section for Decrypt Devices will appear in the policy
- Tick the Decrypt hard drives option if required. All devices configured with this policy will be set to decrypt and uninstall Disk Encryption Manager when the policy is saved
- Leave Decrypt hard drives unticked to disable Disk Encryption Manager and leave the devices encrypted. Control of BitLocker is returned to the device, with its encryption settings set as they were when Disk Encryption Manager was installed. Ensure that the Recovery Key Report has be run and saved securely for these devices. See Disk Encryption Manager Reporting for details
- Click Save to save the configuration and close the dialog
Disabling Disk Encryption Manager in the Managed AntivirusProtection Policy is the only point when the option to decrypt a device is given. As such, care must be taken to ensure only the target devices are using the policy in which Disk Encryption Manager is being disabled. Confirm that there are no other devices, clients or sites using the policy as these will also have Disk Encryption Manager disabled and, if selected, the devices will decrypt. As long as the device remains in the N-sight RMM All Devices view, the Recovery Key information remains available via the Recovery Key Report. If the device is removed from N-sight RMM, the last known valid Recovery Key is retained for 90 days only.
Swapping Policies and Moving Devices
Depending on changes to your customer’s requirements and protection needs, you may have to apply a new Managed Antivirus Protection Policy to their devices or even move devices between Clients and Sites.
Care should be taken when performing these actions, as the devices with policies inherited from the Site or Client level will update to match the Managed Antivirus Disk Encryption Manager configuration as set in the new policy's settings. The policy will not change when it was set at the individual device level.
- When you move devices or swap the Protection Policy from where Disk Encryption Manager is disabled to where it is enabled, all devices will install Disk Encryption Manager and encrypt the device
- When you move devices or swap the Protection Policy from where Disk Encryption Manager is enabled to where it is disabled, all devices will uninstall Disk Encryption Manager and leave the devices encrypted
Where the Managed Antivirus Protection Policy was set at the individual device level, moving the device to another Client or Site will not change the Protection Policy.