2025.2.1 Release Notes
Build Number: 2025.2.1.18 Last updated: 08/13/2025
We strongly recommend upgrading to version 2025.3.1, which includes a critical security fix addressing a vulnerability that could pose a risk to the security of your N-central environment.
Notice for OnPrem partners upgrading to 2025.2.1 from a version earlier than 2025.1.
N-central 2025.1 replaced the underlying operating system on N-central from CentOS to AlmaLinux.
If you are upgrading from a version of N-central earlier than 2025.1 you will be doing a complete operating system migration. This is a significant upgrade to N-central with new system requirements and the upgrade will take longer than a normal upgrade.
We highly recommend reviewing the updated system requirements and release notes for essential details before proceeding with the upgrade.
We’re introducing exciting new features, enhancements, and critical fixes to improve usability, security, and performance. Here’s what’s in the 2025.2.1 release:
What's New in 2025.2.1
The HaloPSA Integration and Autotask REST API features are available as Preview in this release. These features will be rolled out progressively across partners who are interested in participating in this preview.
This approach allows us to monitor adoption and gather feedback to better understand the impact of these new capabilities on existing workflows and integrations before we proceed with a broader rollout.
Enable Coexistence of SOAP and REST APIs for the Autotask Integration
-
The Autotask SOAP API was originally scheduled to reach End-of-Life (EOL) in December 2024, but this plan has since been retracted. While the SOAP API has not officially reached EOL, it is in the process of being sunset, with a new retirement date yet to be announced.
-
To support a smooth transition, we are enabling coexistence of both SOAP and REST APIs for the Autotask integration. This gives partners the flexibility to continue using their current SOAP 1.6 configurations while gradually migrating to REST, minimizing operational impact.
-
We are currently inviting interested partners to preview the REST API integration.
N-central Agent Compatibility for Windows Server 2025
The latest update of the N-central Windows Agent now offers enhanced support for Windows Server 2025 assets, enabling seamless deployment and reliable performance across next-generation Windows Server environments.
CMMC Mode Enablement: Laying the Groundwork for CMMC Compliance
-
As part of our long-term commitment to CMMC compliance, this release introduces foundational features that prepare the platform for secure, CMMC-aligned operation.
-
Upgraded Struts Library to Version 6.4
-
Enhanced Authentication using the following changes:
-
IDP Access Token Expiration Enforcement
Implemented enforcement of expired identity provider (IDP) access tokens in N-central. When an IDP token expires, users are now automatically logged out and prompted to reauthenticate, ensuring secure session handling. To prevent frequent logouts, administrators are advised to extend the token lifespan within their identity provider settings, if permitted by your organization’s security policies.
-
Identity Management – SSO Unlink Behavior
When a user is unlinked from an SSO provider (Azure or generic), N-central now displays a warning message outlining the impact of this action. If the user proceeds with the unlinking, their active session is automatically invalidated, and they are prompted to log in again using local authentication.
-
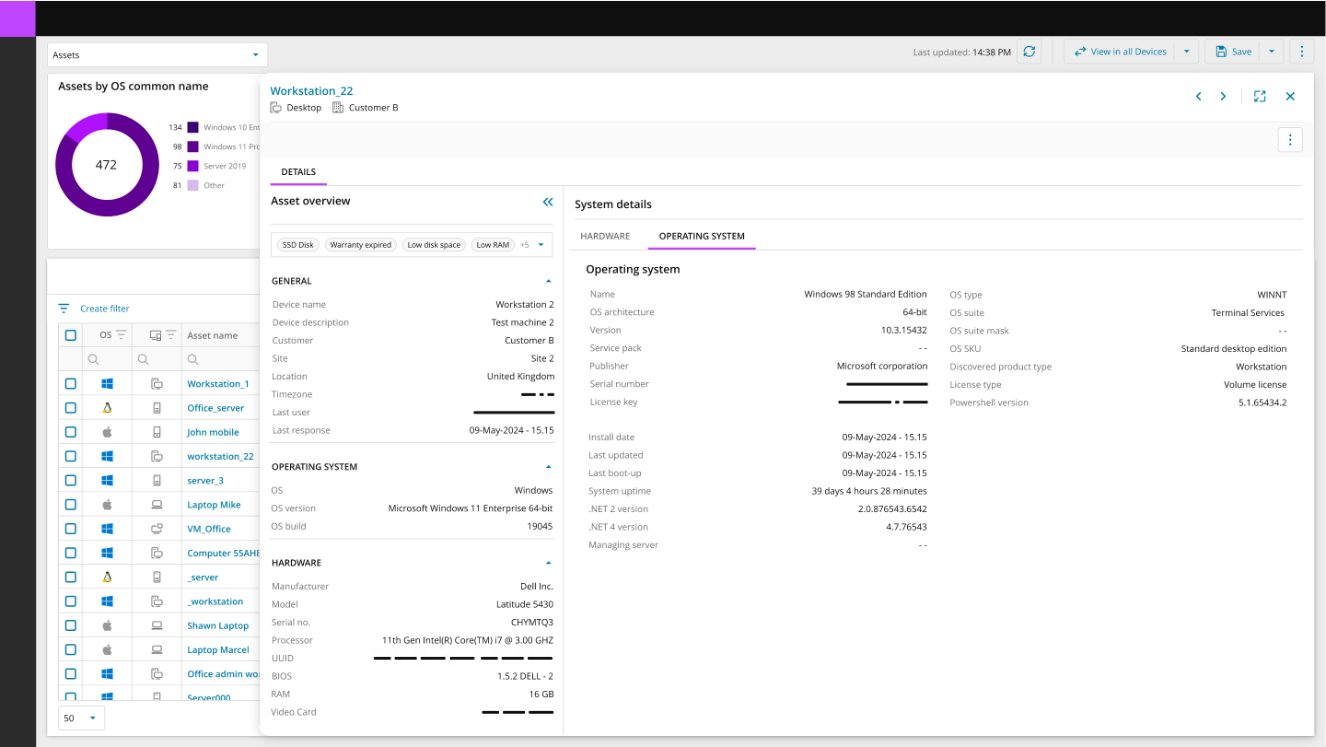
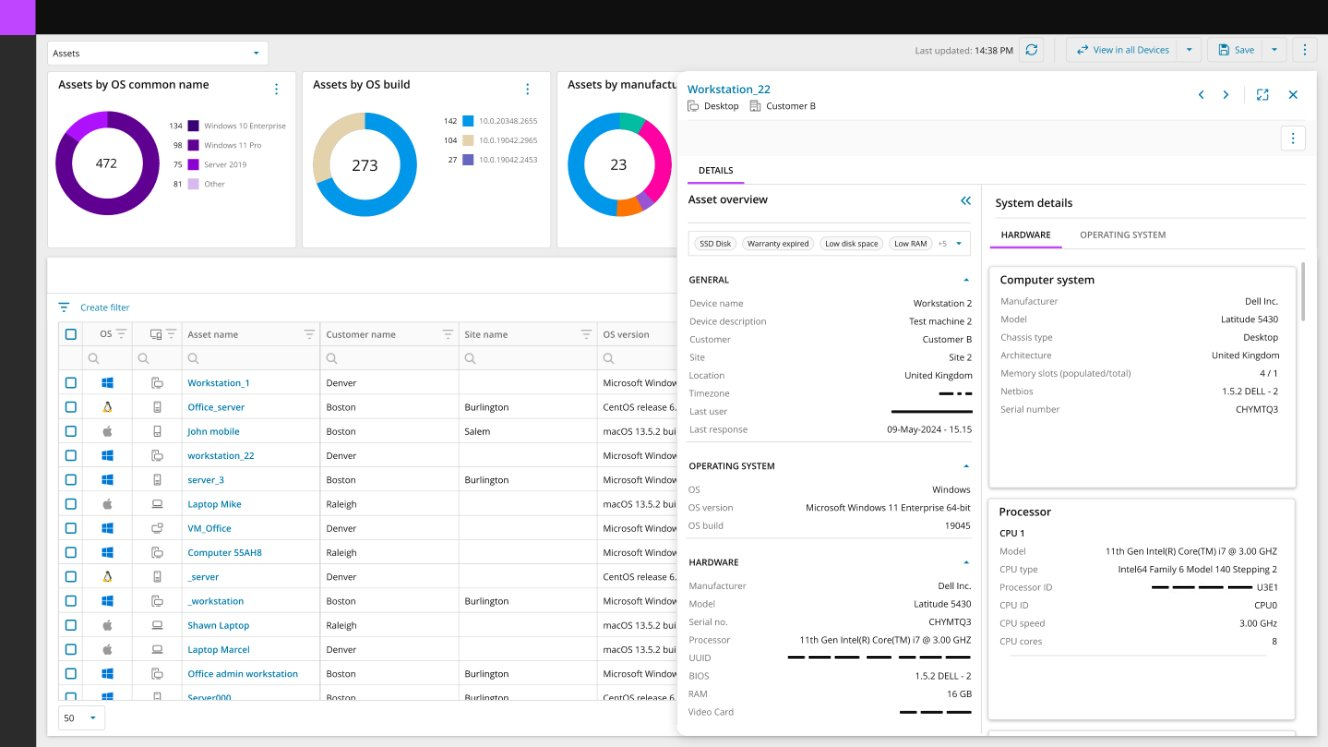
Display of the Asset Details Overlay Panel
Quickly View extended information about an asset
See also
Post GA releases
Here's a breakdown of our new features and updates released since the GA version of N-central.
Vulnerability Enhancements (June 13th, 2025)
We’re excited to introduce the latest refinements to Vulnerability Management, which enhance usability, expand coverage, and improve visibility to help you manage and respond to threats more effectively. You can now export up to 10,000 rows from key views like All Vulnerabilities, All Detections, and Assets at Risk for easier analysis and reporting at scale. Other improvements include direct navigation to device details, enriched vulnerability data, Mac application scanning, and focused views of impacted assets, enabling faster risk assessment.
What’s New
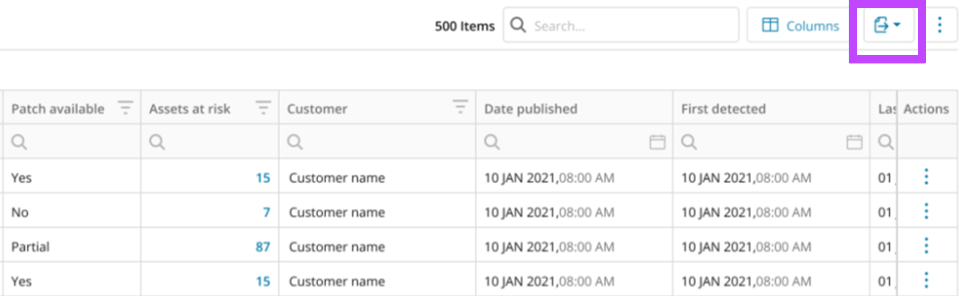
Export Rows from Vulnerability Management Views
Easily export up to 10,000 rows from “All Vulnerabilities”, “All Detections”, and the new “Assets At Risk” views—making data handling and reporting more flexible than ever.
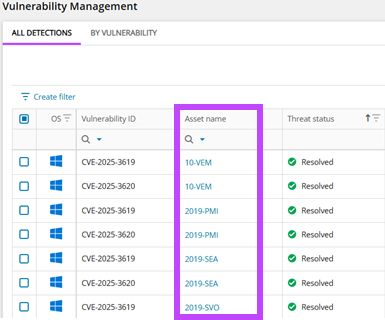
Device Details View
Jump directly from Vulnerability Management tabs to full asset details in both N-sight and N-central. This seamless navigation streamlines your workflow and makes reviewing asset details faster and easier.
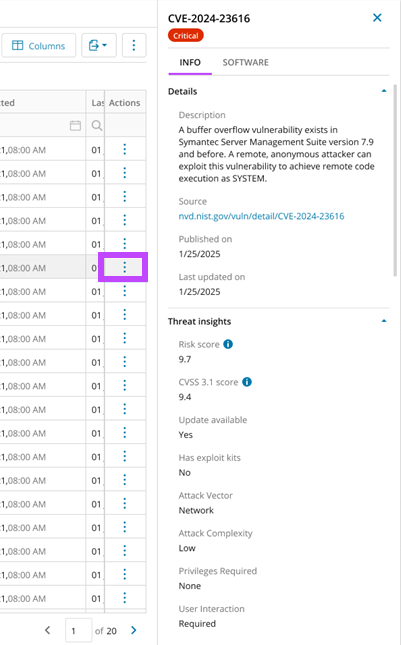
Detailed Vulnerability Insights
Each vulnerability now includes rich contextual data—CVE descriptions, CVSS scores, risk levels, and direct links to authoritative sources—so you can prioritize threats with greater confidence.
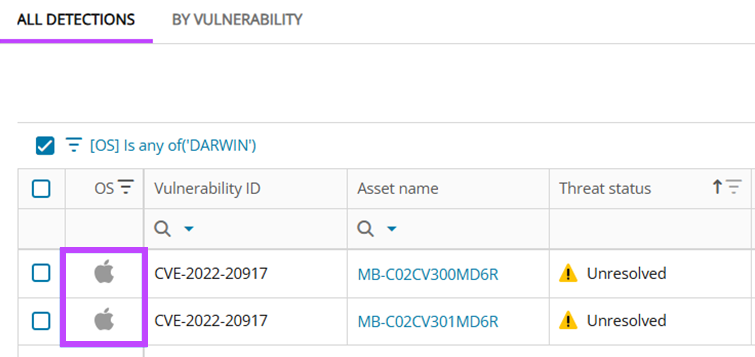
>Vulnerability Scanning Support for Mac Applications
Expanded coverage! Vulnerability scans now include installed applications on macOS devices, thanks to expanded support via the native UFA inventory component.
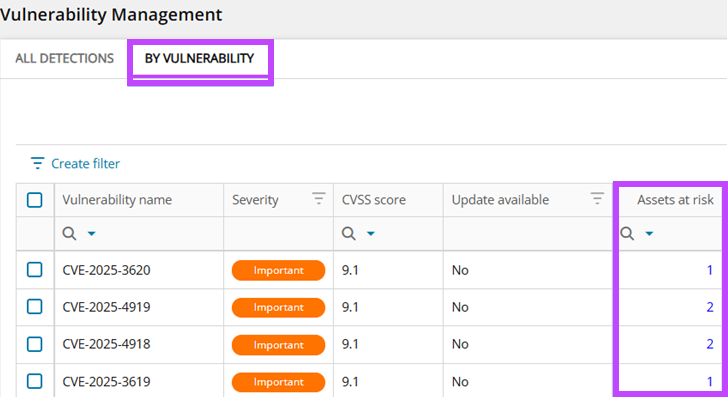
View Assets at Risk for a Vulnerability
Quickly identify all devices affected by a specific CVE. This targeted view helps you accelerate and focus remediation efforts.
Fixes
Reduced Microsoft False Positives
Fixed an issue that caused some Microsoft products to be incorrectly flagged due to release channel settings on endpoints. This improves detection accuracy and reduces noise in your vulnerability reports.
N-central Mac agent v1.12.1 (June 11th, 2025)
A new hotfix version of the Mac agent to address a certificate revocation check issue. This issue had caused problems with the N-central agent's ability to communicate with N-central servers. The hotfix ensures continued reliable connectivity between Mac agents and N-central.
Bug Fixes
| Category | Updated Summary | Issue Key |
|---|---|---|
|
Core |
Improved Probe Task Scheduling to Reduce Stale Service States Issue: Several services monitored by probes were displaying as stale, particularly in high-load environments. This was indicated by missing or blank "Last Scan Time" values. The root cause was the probe's limited task scheduling capacity, which struggled to manage a large number of simultaneous tasks efficiently. Fix: An enhanced task scheduler was introduced to optimize how the probe handles and prioritizes tasks. |
NCCF-626897 |
|
Core |
Data File Manager (DFM) Failure Due to Incorrect Azure Disk Path Issue: The Data File Manager (DFM) stopped working after an upgrade due to an incorrect Azure disk path.Fix: Updated the path logic to align with the latest Azure storage structure. |
NCCF-574527 |
| Core |
Performance Boost During Mass Device Deletion Issue: Deleting many devices caused lock contention on remote control properties. Fix: Optimized backend handling to prevent database slowdowns when deleting large volumes of devices. |
NCCF-546488 |
| Core |
Stabilized Feature Flagging Issue: Missing customer creation timestamp caused flag system to fail. Fix: Added validation and default fallback for missing creation times. |
NCCF-546103 |
|
Core |
Upgrade Failures on Unsupported CPUs Issue: Upgrades failed silently on devices with unsupported CPUs. Fix: Implemented CPU validation checks to block ineligible upgrades early. |
NCCF-542240
|
| Core |
Faster Device Filtering Issue: All Devices view loaded every device on the server instead of only those under the selected Service Organization. Fix: Corrected scope to limit query to SO-visible devices only. |
NCCF-538809 |
|
Core |
ConnectWise: Customer mappings issues Issue: Customer data was displayed incorrectly in ConnectWise integration. Fix: Refined the data sync to ensure accurate mapping across systems. |
NCCF-538614 |
| Core |
Correct PSA Ticket Closure Logic Issue: PSA tickets without a completion date were being marked as deleted. Fix: Fixed PSA sync to prevent incorrectly closing or removing tickets that were still open or lacked completion dates. |
NCCF-535280 |
|
Core |
Incorrect Time Zone Detection for CST devices Issue: Devices in Central Standard Time reported incorrect local times. Fix: Adjusted the time zone recognition logic to align with regional standards. |
NCCF-515334 |
|
Core |
Direct Tools Version String Exception Issue: An unhandled exception occurred when version strings were malformed in the Direct Tools Application. Fix: Added input validation to prevent crashes caused by invalid version strings. |
NCCF-509157 |
|
Core |
Discovery JSON handling error Issue: System errors occurred when making changes to discovery. Json configuration files. Fix: Improved change detection and exception handling to prevent configuration issues. |
NCCF-502392 |
|
Core |
Outdated SMS Registration Feature Removed Issue: The SMS registration feature was linked to an outdated and non-functional service. Fix: Deprecated the broken feature and removed legacy service references. |
NCCF-492760 |
|
Core |
Mac Agent Version Display Error in Analytics Issue: Mac agent versions were incorrectly displayed in the Analytics dashboard. Fix: Corrected version parsing logic to ensure accurate reporting. |
NCCF-469541 |
|
Core |
All Devices Sorting Incorrectly Issue: Serial numbers were not sorted correctly in the All-Devices view. Fix: Adjusted sorting logic to ensure accurate alphanumeric order. |
NCCF-462801 |
|
Core |
Backup Display Inconsistency Issue: Backup results were displayed differently in the UI versus exported reports. Fix: Standardized the backup display between the UI and exports (CSV/PDF). |
NCCF-461335
|
| Core |
Security Patch for Apache Struts Issue: File uploads in the platform’s configuration tools were not processing as expected in some environments. Fix: Upgraded to Apache Struts 6.4.0 and updated upload mechanism. |
NCCF-440860 |
|
Core |
Probe Cache Timeout During Upgrade Issue: During upgrades, probes occasionally hung due to delayed cache access. Fix: Implemented a reasonable timeout for probe cache operations. |
NCCF-424742
|
|
Core |
EDR Device Filter Missing Results Issue: Devices not configured for EDR were excluded from filtered views. Fix: Updated filtering logic to include all devices, even if not yet configured. |
NCCF-421269 |
|
Core |
Improved Input Validation for LAN Device Actions Issue: LAN device actions lacked proper input validation, increasing error risk. Fix: Added strict validation checks for all LAN device input fields. |
NCCF-363817 |
|
Core |
License Server Pull Failure Due to SSL Issue: An SSL provider issue prevented the license server from syncing properly. Fix: Replaced the problematic provider to restore license communication. |
NCCF-309077 |
|
Core |
Incorrect Export Dates When SO Eventing Enabled Issue: Exported files showed incorrect dates when Service Organization Eventing was active. Fix: Corrected date handling to reflect the actual event timestamps. |
NCCF-271691 |
|
Core |
Duplicate Message in Agent Removal Dialog Issue: A confirmation message appeared twice when removing a local agent. Fix: Removed the redundant message to streamline the UI interaction. |
NCCF-130244 |
| Managed Services for Apple Devices |
DMA Agent Retry Logic Fixed Issue: DMA Agent install commands weren't retried on failure. Fix: Ensured DMA installation commands retry properly until they are confirmed as completed. |
MSAD-3254 |
| Ecoverse |
LDAP Username Field Now Valid Issue: LDAP users were not allowed to be edited due to unnecessary username validation. Fix: Fixed validation rules to allow editing LDAP user accounts without triggering incorrect username errors. |
FSN-11683 |
Known Issues
Upgrading from 24.6 and below
When upgrading from a version below 2024.6.0.19 you will need to upload the NSP (N-able Software Platform) upgrade file through the NAC (Network Administration Console) web console, typically accessed at https://<server_address>/admin on port 10000.
Please note, the NAC web console does not support multi-factor authentication (2FA) or single sign-on (SSO) accounts. To access the NAC web console, use the Product Admin account, which has 2FA disabled by default.
The following items are for the current version of the N-able N-central software. They include material issues that significantly impact performance whose cause has been replicated by N-able and where a fix has not yet been released. The list is not exclusive and does not contain items that are under investigation. Any known limitations set forth herein may not impact every customer environment. The N-able N-central software is being provided as it operates today. Any potential modifications, including a specific bug fix or any potential delivery of the same, are not considered part of the current N-able N-central software and are not guaranteed.
Backups
| Description | Issue |
|---|---|
|
Scheduled system backups may not run after fresh installations of N-central 2025.1 and N-central 2025.2. On demand backups continue to work as expected. Also if N-central was upgraded from a previous version it will continue to work as expected. If you experience an issue with Scheduled system backups after a fresh installation of N-central 2025.1 or N-central 2025.2 please reach out to support for further assistance. |
NCCF-597226 |
Integrations
| Description |
|---|
|
Underscore in PSA Integration URL Blocked by UI Validation Users attempting to integrate with PSA platforms using underscores in their endpoint URLs may be unable to complete configuration through the N-central UI for example, api_example.psa.com. This restriction is enforced by the UI only; backend systems and DNS do not block such URLs. The limitation is based on SEO and analytics best practices, where underscores are discouraged due to compatibility concerns with parsing and indexing tools. |
Remote Control
| Description | Issue |
|---|---|
| Web SSH, SSH, Custom remote-control options for windows will not dynamically request an updated path when the saved path is not correct and instead provide a terminal error message requesting the user update the remote control settings path | NCCF-506138 |
| Web SSH, SSH, Custom remote-control options will not work when launched from a MAC or Linux client | NCCF-414079 |
| While calculating the size of the required disk space we look at the size of the last backup on the system, the last system backup on the system must have the "Include Historical Data" option selected in order for the upgrade calculation to be accurate when assessing enough disk space is available. Alternatively downloading then deleting all backups from the system to ensure the backup partition has enough space is an option. Review N-able N-central Backup for details. | - |
| You may run into an error "Not enough space on the root (/) volume for the N- central OS upgrade. We need 'X' GB but there is only 'Y' GB free. Not enough space on the root (/) volume for the N-central OS upgrade. We need 'X' GB but there is only 'Y' GB free". See Not enough space in the root (/) volume for the N-central OS upgrade for details. | - |