2025.3.1 Release Notes
Build Number: 2025.3.1.9 Last updated: 21/10/2025
Security Update
This release includes critical security fix for CVE-2025-8875 and CVE-2025-8876. These vulnerabilities require authentication to exploit. However, there is a potential risk to the security of your N-central environment, if unpatched. You must upgrade your on-premises N-central to 2025.3.1. Details of the CVEs will be published three weeks after the release as per our security practices.
Release version 2025.3.1 containing the security fix is now available.
Please make sure you download the correct NSP file for your upgrade, based on your current version of N-central.
To upgrade from 2024.6 HF1 and earlier please use the OS-Upgrade NSP file.
Click here to access the N-central 2025.3.1 downloads page (login required).
Make sure MFA is enabled. MFA must be mandatory across all N-able products, especially for the admin accounts.
What's New in 2025.3.1
Please note that direct upgrade to N-central 2025.3.1.9 is now supported from versions between 2025.1.0 to 2025.3.0.
You can also upgrade directly to 2025.3.1 from 2024.6.0
We’re introducing exciting new features, enhancements, and critical fixes to improve usability, security, and performance. Here’s a preview of what’s expected in the 2025.3.1 release:
User Audit Log Export – Additional Audit Events
In earlier releases (24.6, 25.2, and 25.3), we introduced the ability to export user audit logs to a Syslog server, giving partners enhanced visibility into critical user actions across N-central. In 2025.3.1, we’ve added support for auditing the following user-initiated events:
-
SSH Access:
-
SSH Login
-
SSH Logout
-
-
Scheduled Task Management:
-
Scheduled Task Edited
-
Scheduled Task Deleted
-
Scheduled Task Enabled
-
Scheduled Task Disabled
-
-
User Script Activity:
-
Script Created
-
Script Modified
-
Script Deleted
-
To configure Syslog export and take full advantage of these features, see: Configure Syslog Export
Device Management API Updates
We’ve made it easier to manage devices and get the information you need through the N-central API:
-
New! Add Devices Automatically
You can now use POST /api/device endpoint to create devices through the API - ideal for scaling environments, automating deployments, and saving time.
-
Improved! See Application Names More Clearly
The GET /api/device/{deviceid}/asset call now includes the application name (application.displayName), so it’s easier to identify the installed applications on each device.
Continued Development on CMMC-Compliant Version of N-central for On-Premises Partners
We are continuing development of the CMMC-compliant version of N-central, specifically designed for on-premises partner-hosted instances. This work is part of our broader initiative to ensure CMMC Level 2 compliance, supporting partners managing environments aligned with U.S. Department of Defense (DoD) cybersecurity requirements.
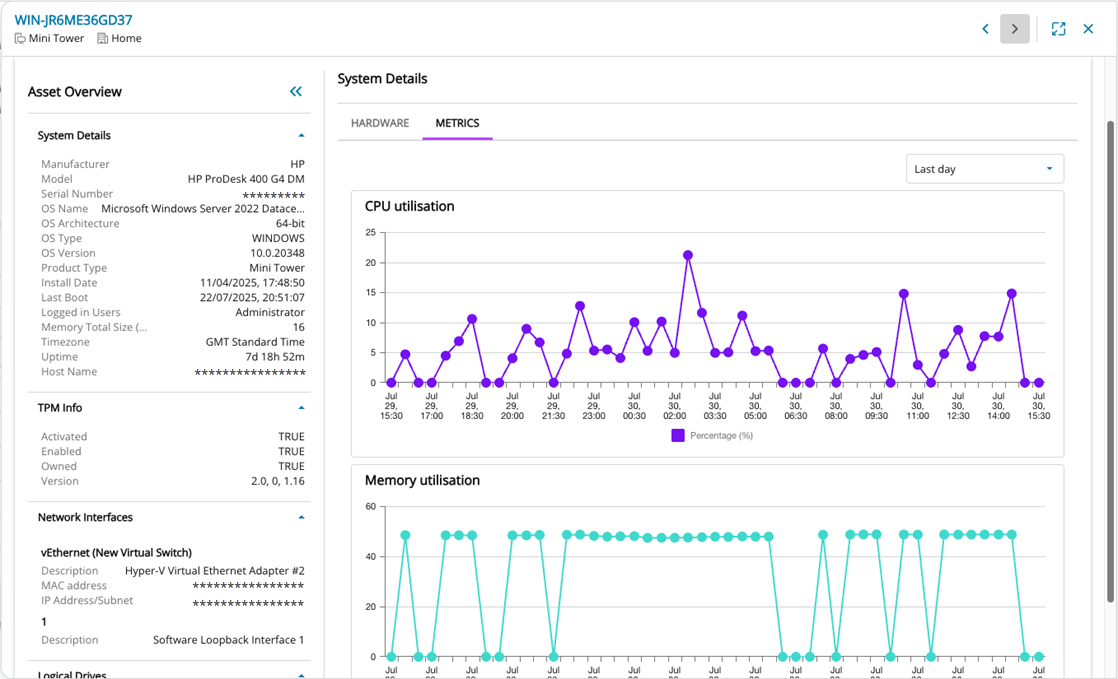
Asset Metrics (Preview) (08/14/2025)
We are pleased to announce the availability of new Asset Metrics showing CPU and Memory usage! To see the new feature, go to Assets View, open the Asset Details panel for that asset, then click on the Metrics subtab to see the new CPU and Memory usage graphs.
Asset Metrics is of high value for both L1 and L3 Technicians because it accelerates issue resolution, reduces escalations, and improves service quality by providing actionable insights into device performance. This empowers L1s to resolve more tickets independently and equips L3s with the context needed for efficient deep-dive investigations - ultimately driving operational efficiency and enhancing customer satisfaction.
Visibility to Asset Metrics helps L1 Technicians diagnose end-user performance issues with recent and historical views of CPU and Memory usage across flexible timeframes, from the last hour to the past week. Graphically displayed data highlights spikes, trends, and potential bottlenecks, enabling quicker root cause analysis and faster resolution.
L3 Technicians also benefit from these insights allowing deeper investigation of monitoring alerts by providing context around system behavior leading up to and following an event—making it easier to validate issues, identify patterns, and reduce false positives.
Feature Highlights
-
Configurable timeframes allowing the user to determine what timeframe to examine the metrics over – Last day by default, last hour, last 6 hours, last 2 days and last week
-
Clear and concise visuals of how a device is performing allowing the user to spot spikes and trends
-
Memory and CPU utilization by default with more to follow – Use the ‘Feedback’ link on the Assets View to tell us which other metrics and info you would like to see!
UX Improvements to Assets View (08/14/2025)
We are also delighted to mention a couple of smaller but helpful updates to the Assets View, based on partner feedback. Now all columns can be resized and minimized down to a smaller size to aid readability and workflow.
We also improved the spacing on the Asset Details view for readability.
Analytics Updates (08/14/2025)
We’re excited to announce a series of recently released Analytics enhancements and bug fixes aimed at improving usability, performance, and reporting accuracy.
| Issue Type | Issue key | Summary | Release Notes | Release Date |
|---|---|---|---|---|
| Enhancement | DV-7226 | N-central Analytics - Hardware Inventory - UI improvements | The configuration page UI has been refreshed with a lighter background, a clearer call to action, and no longer displays the user ID or report version number. | 11-Apr-25 |
| Enhancement | DV-7161 | Hardware Inventory | Introduce 'Site' slicer in the report | A Site filter was added to the Hardware Inventory configuration page to allow users to report on managed devices for one or more sites | 11-Apr-25 |
| Enhancement | DV-6873 | Hardware inventory | Pivot Video Controller (no WH dev) | The Hardware Inventory report was changed to display devices with more than one video card on the same row, instead of over multiple rows | 11-Apr-25 |
| Bug | DV-6848 | Hardware Inventory | GB and GiB Columns (no WH dev) | The Hardware Inventory report was updated to display 'size' values in line with the N-central UI. As a result, Disk size values are calculated as a power of 1000 (GB) and labelled GB, and Memory size values are calculated as a power of 1024 (GiB) but also labelled GB. | 11-Apr-25 |
| Enhancement | DV-7162 | N-central Analytics - Software Inventory - UI improvements | The configuration page UI has been refreshed with a lighter background, a clearer call to action, and no longer displays the user ID or report version number. | 17-Apr-25 |
| Bug | DW-143 | DDA probes information does not contain appliance version [NCIP-10119] | The DIM_DEVICE_SUMMARY and DIM_DEVICE_SUMMARY_LATEST tables have been updated to include version and details for probes | 08-May-25 |
| Enhancement | DV-6764 | N-central Analytics - Hardware Inventory - Performance Improvements | General performance improvements in the Hardware Inventory report | 28-May-25 |
| Enhancement | DV-7224 | N-central Analytics - Software Inventory - Addition of Site slicer | A Site filter was added to the Software Inventory configuration page to allow users to report on software on managed devices for one or more sites | 12-Jun-25 |
| Enhancement | DV-7070 | N-central Analytics - Software Inventory - Performance Improvements | General performance improvements in the Software Inventory report | 12-Jun-25 |
| Enhancement | DV-7353 | N-central Analytics - Patch Status Dashboard Deleted | The Patch Status dashboard was removed from Analytics as it has been replaced by Patch Compliance dashboard | 20-Jun-25 |
| Bug | DV-7327 | N-central Analytics - Software Inventory - Latest installed version | The Software Inventory report was changed to only include the version of an application with the most recent installation date. This to reduce the risk of duplicate entries in cases where the deletion of the previous version wasn't sent from the N-central server to the Analytics warehouse | 23-Jun-25 |
| Enhancement | DV-7256 | N-central Analytics - Patch Compliance Dashboard -Days Since Approval | A new data point that can be used in custom Patch Compliance dashboards to manage pending patches. A typical use case would be to add it as a filter in the dashboard to exclude any patches that have been approved but not installed (i.e. have the status 'Pending Installation') for a defined period of time. The measure can be found when editing the dashboard in the Data panel under Patch Compliance Metrics > Measures > "Days Since Approval" | 12-Jul-25 |
| Enhancement | DV-7323 | N-central Analytics - Network Assessment - Date pickers | The configuration page of the Network Assessment report has been updated to make it clearer that the date period filter is just for the Capacity Planning section of the report. The flexible start and end date has filters have been removed leaving only the fixed period selection to ensure all sections of the report show data for data in the same timeframe. | 29-Jul-25 |
| Enhancement | DV-7227 | N-central Analytics - Network Assessment - UI improvements | The configuration page UI has been refreshed with a lighter background, a clearer call to action, and no longer displays the user ID or report version number. | 29-Jul-25 |
| Enhancement | DV-7368 | N-central Analytics - Last Boot-Up Time and Logged-In User - UI Improvements | The configuration page UI has been refreshed with a lighter background, a clearer call to action, and no longer displays the user ID or report version number. | 13-Aug-25 |
| Enhancement | DV-7613 | N-central Analytics - Patch Compliance Dashboard - Pending (Failed Install) | A new data point that can be used in custom Patch Compliance dashboards to filter out, or report on, any patches that have been approved for installation but have failed to install. The data point is available when editing a custom version of the Patch Compliance dashboard, in the Data panel under 'Patch Compliance Metrics' > Measures > 'Pending (failed install)' | 13-Aug-25 |
| Enhancement | DV-7611 | N-central Analytics - Patch Compliance Dashboard -Is Superseded (Pending) | A new data point that can be used in custom Patch Compliance dashboards to adjust how the 'Is Superseeded' checkbox works so that superseeded patches that were installed are still included in the dashboard. The data point is available when editing a custom version of the Patch Compliance dashboard, in the Data panel under 'Patch Compliance Metrics' > Measures > 'Is Superseeded (Pending)' | 13-Aug-25 |
| Enhancement | DV-7609 | N-central Analytics - Patch Compliance Dashboard -Days Since Publish Date | A new data point that can be used in custom Patch Compliance dashboards to filter out, or report on, any patches with a Publish Date older than a specified date. The metric is available when editing a custom version of the Patch Compliance dashboard, in the Data panel under 'Metrics' > 'Days Since Publish Date' | 13-Aug-25 |
| Enhancement | DV-7604 | N-central Analytics - Patch Compliance Dashboard -Days Since Failed Install (Pending) | A new data point that can be used in custom Patch Compliance dashboards to filter out, or report on, any patches that have been approved for installation (pending) but with a failure to install for a specified time period. The metric is available when editing a custom version of the Patch Compliance dashboard, in the Data panel under 'Metrics' > 'Days Since Failed Install (Pending)' | 13-Aug-25 |
| Enhancement | DV-7504 | N-central Analytics - Patch Compliance Dashboard - Num Pending (Ignore Failure) | A new data point that can be used in custom Patch Compliance dashboards to filter out, or report on, any patches approved for installation (pending) that haven't failed to install. The metric is available when editing a custom version of the Patch Compliance dashboard, in the Data panel under 'Metrics' > 'Num Pending (Ignore Failure)' | 13-Aug-25 |
Patch Management Engine (PME) 2.13.3 GA (08/15/2025)
We are pleased to announce the general availability of PME version 2.13.3, now being deployed across both N-sight and N-central platforms.
This release introduces targeted improvements to the handling of missing, incomplete, or corrupt metadata provided by Microsoft, with a focus on enhancing patch applicability and supersedence logic.
Key Enhancements:
-
Improved Supersedence Handling
Enhanced logic to better manage scenarios where patch supersedence data is incomplete or unavailable.
-
Refined Applicability for Cumulative Updates
Updates from our engine to calculate supersedence during patch detections, to prevent cases where older cumulative updates are flagged as required by the device itself despite newer versions already being installed.
These improvements aim to eliminate erroneous patch offerings to devices where they are not applicable, while also improving visibility into the patch supersedence hierarchy.
Post GA releases
Here's a breakdown of our new features and updates released since the GA version of N-central.
N-central Mac agent 1.12.2 (27/08/2025)
This update contains a small hotfix to address a problem where Mac devices were periodically unable to communicate with N-central servers.
Analytics Updates (30/09/2025)
| Issue Type | Issue key | Summary | Release Notes | Release Date |
|---|---|---|---|---|
| Enhancement | DV-7369 | N-central Analytics - Managed Devices Summary Report | The configuration page UI has been refreshed with a lighter background, a clearer call to action, and no longer displays the user ID or report version number. | 04-Sep-25 |
| Enhancement | DV-7371 | N-central Analytics - Remote Control Usage Report | The configuration page UI has been refreshed with a lighter background, a clearer call to action, and no longer displays the user ID or report version number. | 04-Sep-25 |
| Enhancement | DV-7366 | N-central Analytics - Antivirus Report | The configuration page UI has been refreshed with a lighter background and a clearer call to action. The user ID and report version number have been removed, and a new filter for Site has been added. | 04-Sep-25 |
| Enhancement | DV-7370 | N-central Analytics - Managed Devices by Operating System | The configuration page UI has been refreshed with a lighter background and a clearer call to action. The user ID and report version number have been removed, and a new filter for Site has been added. | 08-Sep-25 |
| Bug Fix | DV-7238 | N-central Analytics - Network Assessment Report | The column ‘Hours over Capacity’ was removed from the first table in the Capacity Planning section, as it was incorrectly displaying a count of hours over capacity rather than the actual values. | 11-Sep-25 |
| Enhancement | DV-7386 | N-central Analytics - Disk Usage Trending Report | The configuration page UI has been refreshed with a lighter background and a clearer call to action. The user ID and report version number have been removed, and a new filter for Site has been added. | 18-Sep-25 |
| Bug Fix | DV-7793 | N-central Analytics - Software Inventory Report | Resolved an issue that occasionally caused rows to be missing Device Names. | 30-Sep-25 |
| Bug Fix | DW-482 | N-central Software Inventory Report | A bug that fixes an issue that was causing deleted applications to appear in the N-central Software Inventory report. | 10-Oct-2025 |
| Bug Fix | DV-7545 | N-central Hardware Inventory Report | Fixed a bug that caused removed external storage to still be counted and included in the Total Disk (GB) column of the Hardware Inventory report | 21-Oct-2025 |
Patch Management Engine (PME) Update Announcement(15/09/2025)
This update is exclusively available to N-central assets set to use the Release Candidate (RC) version of Patch Management.
This release focuses on bug fixes and performance improvements, including:
Enhanced Patch History Handling
We’ve improved how PME queries historically installed patches. Previously, changes in system environments, such as OS build updates, could cause the WUA API to stop returning patch data, resulting in patches being incorrectly stuck in an “In-progress” or “Pending” state in reporting analytics. This update resolves that issue, ensuring more accurate patch status reporting.
Improved ESU Patch Detection
We’ve refined the logic for detecting and offering Extended Security Updates (ESUs), leading to more accurate patch availability and coverage.
Removal of Preview Patches Without Supersedence
Preview patches that lack proper supersedence metadata have been removed from scan detections. These patches can interfere with our patch offering logic and are generally not recommended by Microsoft for production environments. PME will now exclude them, however we will consider their re-introduction once metadata has been improved.
PME Engine Update – Version 2.13.5.5568 (RC: 14/10/2025 | GA: 20/10/2025)
This release addresses a bug affecting how supersedence information was handled for Cumulative Updates (CU) detected via Windows Update Agent.
As a result of this fix, PME can now more effectively filter updates and prevent older CUs from being offered when a newer one is already installed.
Known Issues
|
Category |
Updated Summary |
Issue Key |
|---|---|---|
|
Core |
During pre-upgrade checks, servers running version 2025.3 may report insufficient memory when upgrading to 2025.3.1.
Issue: Due to the kernel upgrade in 2025.3, the total system memory reported to the AlmaLinux 9 OS is lower than before the kernel upgrade. In some cases this can cause the minimum memory check during the pre-upgrade checks to fail. Recommendation: Please remove any un-needed virtual devices from your VM configuration (i.e. soundcards), or temporarily add an additional 1GB of memory. For cloud servers, you may need to temporarily upgrade to a larger instance size for the upgrade, and revert back to your current instance size post-upgrade. |
NCCF-836008 |
Bug Fixes
A range of high-impact bugs have been resolved in this release. Be sure to review the full list included below for more details.
|
Category |
Updated Summary |
Issue Key |
|---|---|---|
|
Integration and Remote Support |
||
|
Core |
PSA Export Fails with Long Passwords
Issue: Long PSA integration passwords caused export operations to fail. Fix: Truncated and sanitized long strings to ensure stable export behavior. |
NCCF-762305 |
|
Core |
Customer Info Missing from Warehouse
Issue: Some devices were flagged for reinstallation prematurely due to the recovery of logic errors. Fix: Improved recovery checks to avoid unnecessary reinstalls. |
NCCF-533915 |
|
Core |
Take Control Setup Fails During Remote Support
Issue: Remote support failed when Take Control was not pre-configured. Fix: Improved default configuration handling to allow dynamic Take Control setup. |
NCCF-602350 |
|
Performance, Audit & Data |
||
|
Core |
HP Stock Drive Mappings Caused Malformed Data
Issue: Outdated HP physical drive mappings resulted in malformed asset data. Fix: Updated drive mapping logic and data parser validation. |
NCCF-679885 |
|
Core |
Duplicate “DeletedID” Prefix in Asset Names
Issue: Asset names incorrectly included repeated “DeletedID” text after device removal. Fix: Removed redundant prefix logic and cleaned up asset records. |
NCCF-506131 |
|
Core |
Scheduled Tasks Stuck on Network Share
Issue: Scheduled tasks based on network shares were stuck in 'In Progress' status. Fix: Resolved file lock issues and improved task completion logic. |
NCCF-230181 |
|
Core |
System Error: Task Updates Failing Due to ID Limit
Issue: A system ID used to track changes grew too large, causing task failures and repeated error messages. Fix: Increased the ID limit to prevent future failures. A server restart may be needed to apply the fix. |
NCCF-703826 |
| Core |
Title: Improved SSL_read Error Handling and OpenSSL Compatibility
Issue: After upgrading to version 2025.2, some HTTPS checks - used to validate certificate expiry, content verification, and service availability - fail when monitored by the Central Server. These checks return no status code in the response. Fix: Enhanced SSL_read error handling and added support for OpenSSL error codes compatible with AlmaLinux 9, CentOS 8 and later, and Ubuntu 20.04 and later. |
NCCF-734812 |