Configure Syslog Export
On premise: accessed at System level.
Hosted: accessed at SO level.
A syslog can provide detailed information on audited events, how they are recorded, and offers an automated method to export records for consumption by a Security Information and Event Management (SIEM) system. With this capability, many user actions in N-central can now be automatically exported to your syslog server in near real-time. You can then pull these logs from your syslog server into your SIEM product.
Visit Audit Events to review a list of the audit events, and the version of N-central where they were introduced.
How it works?
Required Permissions
You need to set the appropriate permissions in N-central to configure and export a syslog audit report.
In the Administration > User Management > Roles (choose a role) > Configuration > Compliance, select Manage.
For more information about roles and permissions, see Role-based permissions.
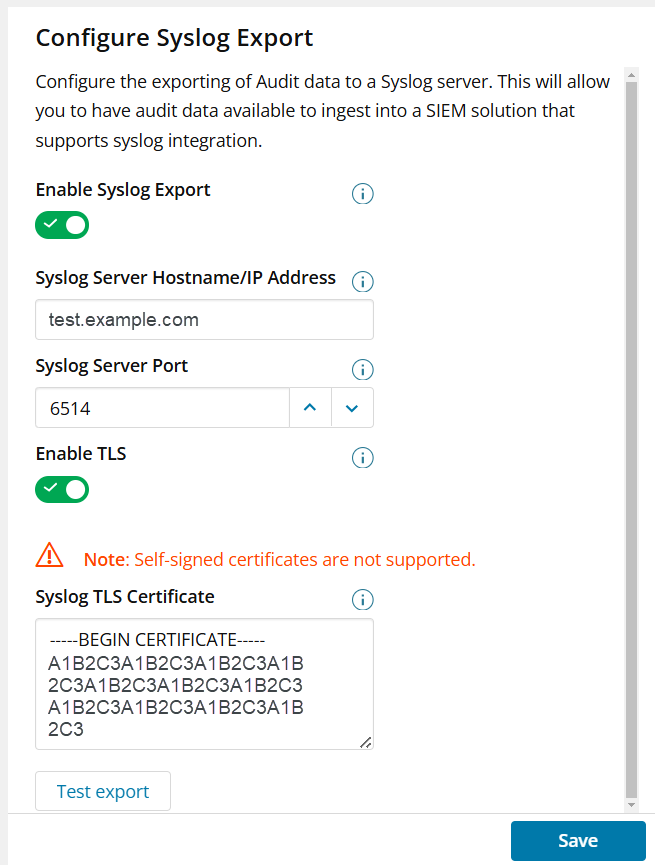
Configure Syslog Export:
-
From the left-hand navigation menu, click Administration > Audit Export.
-
Toggle the button Enable Syslog Export to enable or disable.
-
Enter Syslog Server Hostname/IP Address in the text box.
-
Enter Syslog Server Port . The Default value for non TLS is 514 (unencrypted), and TLS is 6514 (encrypted).
For on-premise - It is HIGHLY recommended to use port 6514 TCP and TLS encryption for security purposes.
For hosted - Port 6514 TCP is the ONLY available port and requires TLS encryption.UDP ports are not currently supported, and all communication within N-central occurs over TCP.
-
Toggle Enable TLS to enable or disable TLS encryption. If TLS is used (as required for hosted environments), a hostname must be used instead of an IP address.
Enabling TLS is optional if the receiving device is on the same subnet as N-central.
It is strongly recommended to use TLS if the receiving device is not on the same subnet as N-central. - When TLS is enabled, enter the CA Bundle (containing only the Intermediate and Root certificates) from the Syslog TLS Certificate in the text box labeled Syslog TLS Certificate. This certificate must be issued by a trusted Certificate Authority (CA) and match the configuration of your Syslog server. Please note that a valid TLS certificate is required; self-signed certificates are not supported.
-
Click Test Export to send a single test record out to the receiving device. Syslog is a one-way logging protocol, where messages are transmitted from the client to the syslog server without expecting any response.
Example syslog extract:
<110>1 2024-11-13T14:11:08.849-05:00 - ncentraldms - login.singlesignon - [ncuser@mycompany.com] logged in from 123.123.123.123 logged in at 2024-11-13 14:11:08.849 using External IdP MSPSSO, user customer path is [System]
This string references:
-
110: The PRI (Priority) is a calculated value embedded in syslog messages. It signifies the message’s priority level and is represented by a number, like 110. This value helps classify the importance of the log message being sent from the sender to the receiver within a syslog system.
-
1: The Syslog version in use.
-
2024-11-13T14:11:08.849-05:00: the date and time of the action in UTC/ISO 8601 format.
-
ncentraldms: the source of the action. You may also see secure syslog for actions from SSH sessions.
-
[ncuser@mycompany.com] logged in from 123.123.123.123 logged in at 2024-11-13 14:11:08.849 using External IdP MSPSSO, user customer path is [System]: the recorded audit action.
The format on the receiving server may differ from the above example as it processes records from multiple sources. The first IP listed in this example is the N-central instance’s external IP address, which can vary based on the syslog server’s software.
-
When you modify a service template at the SO level, the system actually creates a clone of the original template and applies your changes to the clone. As a result, the audit log records this as a create action—not a modify.
In contrast, modifying a template at the System level updates the original template directly. This action is correctly logged as a modify because it doesn’t involve cloning.
This difference is due to backend logic and can’t be changed. However, it’s important to be aware of this behavior, especially when auditing or troubleshooting. If you're expecting a modification event but see a creation event instead, this is likely the reason.
Example Log Entry:
Jun 13 14:34:27 10.220.200.72 <110>1 2025-06-13T14:34:26.618-04:00 - ncentraldms - servicetemplate.create - [tester@n-able.com] logged in from 10.19.30.147 created Service Template [Empty Template 1 (Service_Organization Clone)] with services [Asigra Backup] in Service Org [Service_Organization] at 2025-06-13 14:34:26.618
In this case, the service template Empty Template 1 already existed, and only the Asigra Backup service was added. However, due to the cloning mechanism at the SO level, the audit log records this as a created Service Template event. You can identify this behavior by the label (Service_Organization Clone) in the template name.