Take Control Architecture
Introduction
N-able Take Control is a comprehensive and powerful, yet easy-to use, remote support platform, allowing access to Windows (version 2000 or later) and macOS (version 10.7 or newer) devices from most Desktop and Mobile Operating Systems.
With Take Control inSight Lite - a Remote Monitoring and Management module integrated into Take Control - Network Administrators and Managed Service Providers (MSPs) have their IT devices, whether individual or integrated into differently sized networks or topologies, reducing management costs and optimizing the implementation of policies and procedures in all types of infrastructures or organization.
The Insight Lite add-on is compatible with all versions of Microsoft Windows™, from 32 to 64 bits, since the 2000 version. From independent consultants, to technology services companies, Take Control is the most efficient solution in providing the maximum Return on Investment.
Architecture
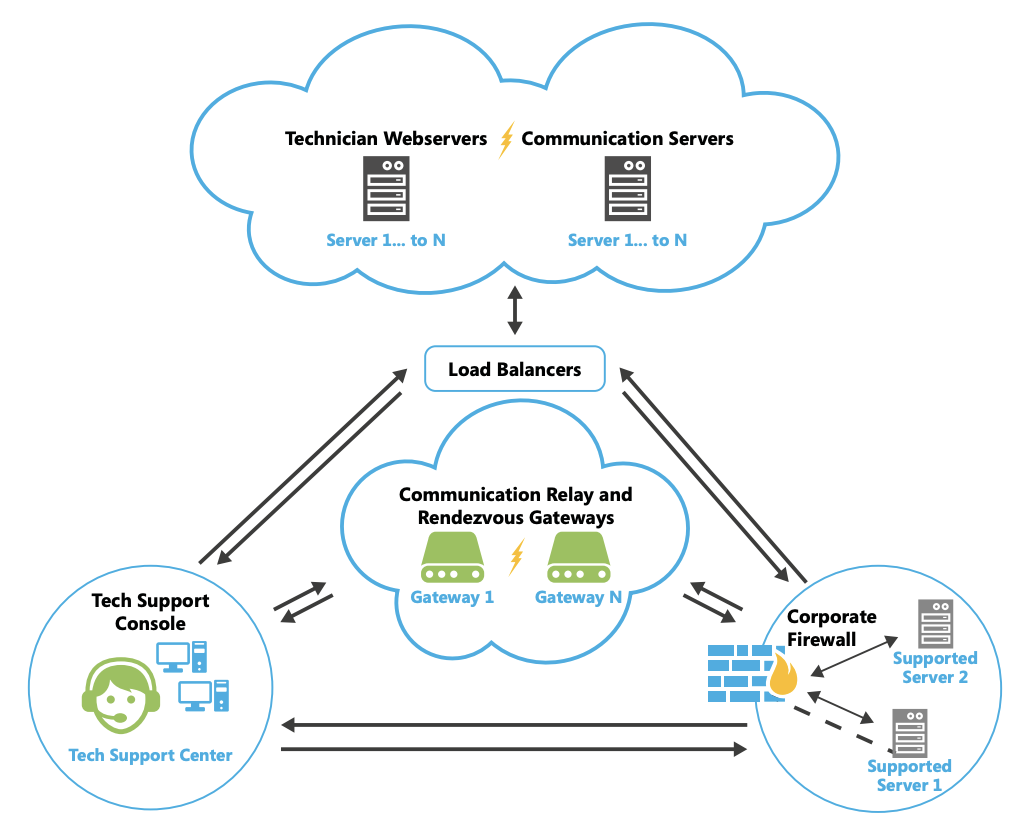
The network support side of Take Control can be divided into 4 major components:
- The Central Servers host the communication with the Tech Consoles, the Applets and the Agents, and create all incoming and outgoing sessions
- The Gateways keep Agents connected and distribute centralized commands, as well as mediate sessions that cannot be executed in peer-to-peer mode
- The Tech Consoles establish connection with the clients’ devices
- The Agents/Applets, executed locally on the clients’ devices, allow both remote access and management
The Central Servers establish communication with all components in different stages of the service, while the remaining servers work independently.
Redundancy
Take Control’s infrastructure is built on a failure tolerant, geographically distributed and redundant architecture. It is monitored 24/7 through both automated resources (Take Control's own watchdog, Pindgom and Wormly services) and human resources (dedicated support contacts):
-
The Central Servers are in three different and redundant locations hosted on Amazon Web Services. These servers coordinate the establishment of sessions and the connection to technicians, as well as the databases that support the system.
-
The assignment of communication gateways, which assure the establishment of remote sessions when there is no direct connection between the two points - to support sessions or to Take Control’s Agents, is made according to country and geographic proximity, and is automatically replaced by an alternative connected gateway, if unavailable. Each one of the gateways available have several thousands of simultaneous connections, being monitored in real-time for health and capacity, both by automatic systems and Take Control’s 24/7 Network Operations Control center. New gateways can be automatically created in a matter of minutes, if needed.
Security
The entire session (all of its content, including but not limited to remote control, VoIP, File Transfer…) is sheltered by a proprietary communication protocol encrypted by AES-256 CTR + HMAC-SHA256 and a Diffie–Hellman ephemeral key exchange, whether when establishing the session, security if guaranteed by TLS 1.2.
As an additional security measure, all commands containing images, keyboard and mouse strokes, file transfers and clipboard information are digitally signed. Take Control has no access to the sessions’ content, since all encryption is based on an end-to-end negotiation, which leaves no room for intercepting the transferred information nor decoding it in the gateway.
The encryption keys are randomly generated in each session between the Viewer and the Applet or the Take Control Agent. As an additional security measure, the client can configure a Master-Password (saved only in the Agent) or choose Windows Account authentication, as well as requiring a previous authorization for the machine user to launch of the session. All the actions performed during the sessions are logged, and video recording can be made mandatory. Also, any session performed to a Windows device will be registered in the machine’s Event Viewer.
Data Policy
Take Control will not sell or rent personally identifiable information to anyone unless given expressed consent to disclosures personal identification and other personal information to third parties.
Take Control may send personally identifiable information to third parties when:
- We have Your consent to share the information
- We have Your consent to share the information
- We find that Your actions on the web service violate these Terms of Service
- We respond to subpoenas, court orders or legal processes which require us to disclose registration data or any information about You to law enforcement or other government officials as BA, in its sole discretion, believes necessary or appropriate.