You can add rules that apply to a specific domain in the Domain Rules tab or, if accessing from the Admin Level, to all domains linked to the logged in Admin in the Admin Rules tab.
- In the Admin Level or Domain Level Control Panel, select Incoming - Protection Settings > Allow list filtering rules
- Navigate to the appropriate tab: Domain Rules or Admin Rules
- Click on + Add rule
- Configure the Block list rule as per the filter rule type:
 Simple Allow list Filtering Rule
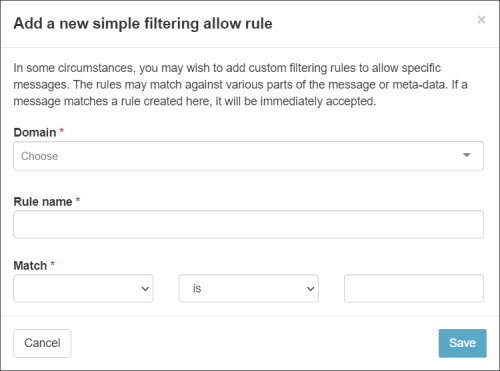
Simple Allow list Filtering RuleIf the Use advanced custom filtering rules option is disabled in the User profile page, you will see the Add a new simple filtering allow rule dialog:
Enter the required information in each of the fields:
Field Description Match Operators Field value Domain (only displayed at Admin Level) Select the domain the rule will apply to - Domain name selected from the dropdown list of domains Rule name Give the rule a memorable name - Rule name in text format Match Use the Match fields to structure your rule. The following options are available:
Can be refined by the following operators:
- Is
- Is not
- Contains
- Does not contain
- Starts with
- Ends with
The part of the message subject to allow in text format From Can be refined by the following operators:
- Is
- Is not
- Contains
- Does not contain
- Starts with
- Ends with
The part of the message header FROM address to allow in a valid email address format
e.g.:
Rocket Raccoon <rocket@demo-domain.invalid>Check the exact format from an example message header of the type you wish to block as the format may differ
To Can be refined by the following operators:
- Is
- Is not
- Contains
- Does not contain
- Starts with
- Ends with
The part of the message header TO address to allow in a valid email address format
e.g.:
Rocket Raccoon <rocket@demo-domain.invalid>Check the exact format from an example message header of the type you wish to block as the format may differ
CC Can be refined by the following operators:
- Is
- Is not
- Contains
- Does not contain
- Starts with
- Ends with
The part of the CC address to allow that was contained in the message header in a valid email address format
e.g.:
Rocket Raccoon <rocket@demo-domain.invalid>Check the exact format from an example message header of the type you wish to block as the format may differ
Country Can be refined by the following operators:
- Is
- Is not
Select the value from the defined list of Country codes Continent Can be refined by the following operators:
- Is
- Is not
Select the value from the defined list of Continent names Message Body Can be refined by the following operators:
- Is
- Is not
- Contains
- Does not contain
- Starts with
- Ends with
The part of the decoded message content to allow in text format Recipient Can be refined by the following operators:
- Is
- Is not
- Contains
- Does not contain
- Starts with
- Ends with
The SMTP envelope RCPT TO address to allow in a valid email address format
e.g.:
local-part@domain.invalidSender Can be refined by the following operators:
- Is
- Is not
- Contains
- Does not contain
- Starts with
- Ends with
The SMTP envelope MAIL FROM address to allow in a valid email address format
e.g.:
local-part@domain.invalidSender IP Can be refined by the following operators:
- Is
- Is not
- Contains
- Does not contain
- Starts with
- Ends with
The Public IP address of the sending server to allow in a valid IP format
e.g.:
1.102.103.104Sender Hostname Can be refined by the following operators:
- Is
- Is not
- Contains
- Does not contain
- Starts with
- Ends with
The associated DNS PTR record for the sender IP address to allow URL Can be refined by the following operators:
- Is
- Is not
- Contains
- Does not contain
- Starts with
- Ends with
- Language Can be refined by the following operators:
- Is
- Is not
- Contains
- Does not contain
- Starts with
- Ends with
Select the value from the defined list of language codes - Language code Attachment Type Can be refined by the following operators:
- Is
- Is not
- Contains
- Does not contain
- Starts with
- Ends with
The MIME type of attached files to allow in text format Attachment Name Can be refined by the following operators:
- Is
- Is not
- Contains
- Does not contain
- Starts with
- Ends with
The name or file extension of attached files to allow in text Attachment Type (auto-detect) Can be refined by the following operators:
- Is
- Is not
- Contains
- Does not contain
- Starts with
- Ends with
The Auto-detect attachment type scans the content of the encoded data within attachments and identifies the type of the encoded data for filtering, ignoring the reported extention type or name within the message content.
The data for the rules should be the text of the "Media types" (https://www.iana.org/assignments/media-types/media-types.xhtml) "template" field, for example: application/pdf for PDF files or image/png for standard PNG image files.
Sensitive Data Can be refined by the following operators:
- is
Choose one of five available data types to match:
- credit-card
- bank-account
- personal-identifier
- health-identifier
- any
We will match against the most common formats of these types of data – for example, a VISA credit card might be “4012888888881881”, or “4012-8888-8888-1881”, or “4012 8888 8888 1881”. However, it will always be possible for someone determined to bypass these checks to do so, e.g. with “my credit card is 4012 then eight eights in a row then 1881”. This functionality is intended to protect against accidental exposure rather than malicious intent.
 Advanced Allow list Filtering Rule
Advanced Allow list Filtering RuleIf the Use advanced custom filtering rules option is enabled in the User profile page, you will see the Add a new advanced filtering allow rule dialog:
Field/Option Description Domain (only displayed at Admin Level) Choose the domain you want to apply the rule to from those available in the Domain dropdown. (When you are accessing this page at the Domain Level, the system applies the rule to the logged in domain). Rule name Enter the name you want to give this rule Priority Enter a number to represent the priority given to the rule Rules are evaluated by Priority from the lowest number to the highest number, until one matches or all rules have been checked. All Allow list rules are checked before Block list rules regardless of priority.
Content Type By default this field will display Header Name as initially the Match field is set to Header, however, this field will change or disappear as the Match field is changed:
Match Field Name Value Header Header Name Restrict the check to a specific header. This will also match the decoded version of the header rather than the raw content.
You may enter a regular expression here, if required.
Message Body Content Type Restrict the check to specific parts of the message for example text/plain, or text/.*.
You may enter a regular expression here, if required.
Language Automatic or Specified By default, language matches will be done against automatic language detection and when the sender specifies the language. To only match against automatic detection, use "automatic", or to only match when the sender specifies, use "specified" Location Location Type You may specify which type of location to match against. Valid values are:
- "city"
- "continent"
- "country"
- "represented_country"
- "registered_country"
- "latitude"
- "longitude"
You may enter a regular expression here, if required.
Advanced filtering location rules created using regular expressions may not be compatible with the simple filtering rule views and as such display as Unknown.
Hashing Algorithm Supported Hash You must specify which Hash to match against. Valid values are:
- MD5
- SHA-224
- SHA-256
- SHA-384
- SHA-512
Regular expression Enter the regular expression for the rule
Use the Cheatsheet panel on the right of the page for examples of how to build your regex.
Unfortunately, the Technical Support team is unable to support any customisation of the predefined Rulesets or those you build yourself.
Due to the potential complexity in building a regex pattern, we advise that only users with regex experience should attempt to create new rules or customise existing ones.Match Use the Match fields to structure your rule. The following options are available:
- Header
- Raw Message
- Message Body
- HELO/EHLO
- Recipient
- Sender
- Sender (Verified)
- Sender IP
- Sender Hostname
- URL
- Language - Language code
- Location
- Attachment Type
- Attachment Name
- Attachment Type (auto-detect)
- Attachment Hash
- Message Type
- Sensitive Data
We will match against the most common formats of these types of data – for example, a VISA credit card might be “4012888888881881”, or “4012-8888-8888-1881”, or “4012 8888 8888 1881”. However, it will always be possible for someone determined to bypass these checks to do so, e.g. with “my credit card is 4012 then eight eights in a row then 1881”. This functionality is intended to protect against accidental exposure rather than malicious intent.
Flags The following flags are available: - i (ignore case)
- m (^ and $ match start and end of line),
- s (. matches newline)
- x (allow spaces and comments)
- Click Save
The dialog that is displayed here depends on whether you have enabled or disabled the Use advanced custom filtering rules option in the User profile page. For more information, see Manage Your Admin User Profile or Manage Your Domain User Profile.
The new rule will appear in the list shortly after saving.
Attachment Hash Rule Specifics
The Hashing Algorithm field that is displayed once Attachment Hash is selected in the Match field is compulsory. Fill this with the algorithm type used to generate the hash for the file to be matched. E.g.:
- MD5
- SHA-224
- SHA-256
- SHA-384
- SHA-512