Data Breach Prevention Lifecycle
The security of corporate sensitive data is under relentless attack. Fighting the war on digital data loss has reached the status of a global epidemic.
The vast majority of data breaches are caused by unprotected data at rest, residing on vulnerable endpoints and resulting in an easy entry point for attackers.
Risk Intelligence recognizes today's cyber security challenges and enables organizations to protect themselves by continuously assessing their environments using proven technology that follows the Data Breach Prevention Lifecycle stages:
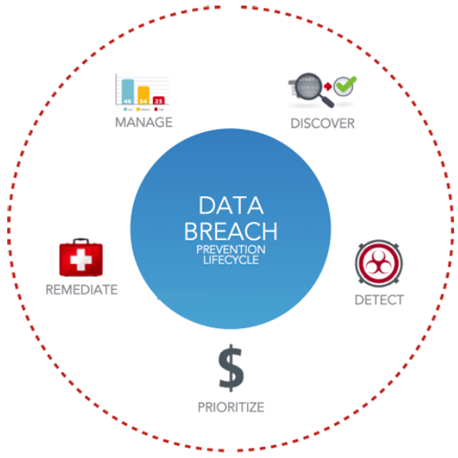
- Discover - Unprotected sensitive data at rest and the insiders that have access to the data
- Detect - Security threats providing vulnerable entry points for attackers to access your data
- Prioritize - At-risk assets by leveraging the combined intelligence of security threat and data intelligence
- Remediate - Security threats by applying patches, mitigating solutions and encrypting or removing unprotected data
- Manage - The entire lifecycle process through a single scalable cloud-deployed console
In this Quick Start Guide, we will walk through implementing the Risk Intelligence Data Breach Prevention Lifecycle using the Risk Intelligence Data Breach platform.
The guide describes how to effectively:
- Use the system to discover data and vulnerabilities - using the Expanded Data Breach Risk Scan. See Performing an Expanded Data Breach Risk Scan.
- Generate data breach risk reports to help prioritize activities for remediation and help prevent a data breach in your organization before it occurs. See Reporting.
