Disable Disk Encryption Manager at the Individual Device Level
At some point you may want to remove Disk Encryption Manager and either:
- Decrypt a device's hard disks
- Leave a device's hard disks in an encrypted state
In either case, encryption management is returned to the target device's BitLocker installation and is no longer managed by N-sight RMM.
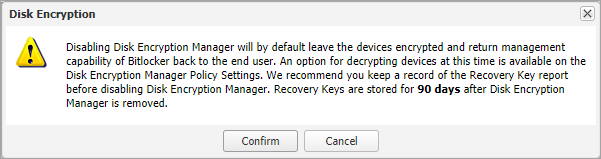
Disabling Disk Encryption Manager in the Managed AntivirusProtection Policy is the only point when the option to decrypt a device is given. As such, care must be taken to ensure only the target devices are using the policy in which Disk Encryption Manager is being disabled. Confirm that there are no other devices, clients or sites using the policy as these will also have Disk Encryption Manager disabled and, if selected, the devices will decrypt. As long as the device remains in the N-sight RMM All Devices view, the Recovery Key information remains available via the Recovery Key Report. If the device is removed from N-sight RMM, the last known valid Recovery Key is retained for 90 days only.
As disabling Disk Encryption Manager, and therefore decrypting devices, is controlled via the Managed AntivirusProtection Policy, care must be taken to not disable it on unintended devices which may be using the same policy. Your situation will fall into one of 2 scenarios, either only devices to be amended are using the policy, or those devices use a mixture of policies and will need to be amenbded onto one policy before Disk Encryption Manager can be removed safely.
The first step in either case is to run the Recovery Key Report, then confirm that the policy where you will disable Disk Encryption Manager is only in use by the devices where you want to disable Disk Encryption Manager with or without decryption.
BitLocker is a native part of the device system. If you chose to remove the Disk Encryption Manager from a device and leave the disk encrypted, you will lose the management capabilities in N-sight RMM. Ensure you collect all recovery keys before choosing this option. You should ALWAYS obtain the Recovery Keys prior to taking any action with Disk Encryption Manager. N-sight RMM only retains the last known valid Recovery Keys for removed devices for up to 90 days only. If something goes wrong with the decryption, and you deleted the device from N-sight RMM, there is no way to recall the Recovery Keys or unlock the drive after the 90 day period.
Before you start, follow the Disk Encryption Manager disable process in Removing Disk Encryption Manager with or without Decrypting Devices.
How to Disable Disk Encryption Manager at the Individual Device Level with or without Decrypting
Ensure the devices are the ONLY devices using the Managed AntivirusProtection Policy that will have Disk Encryption Manager disabled before proceeding.
- Select Settings > Managed Antivirus > Protection Policy
- Either double-click the target policy or highlight it and select Edit
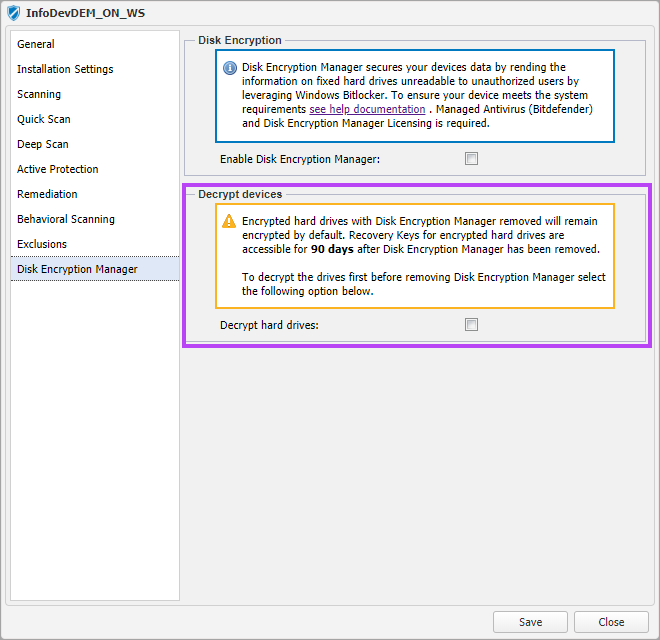
- In the policy dialog, select Disk Encryption Manager in the left-pane
- Untick the Enable Disk Encryption Manager tick box
- An advisory warning appears, read through this so you fully understand the action being taken and then click Confirm
- A new section for Decrypt Devices will appear in the policy
- Tick the Decrypt hard drives option if required. All devices configured with this policy will be set to decrypt and uninstall Disk Encryption Manager when the policy is saved
- Leave Decrypt hard drives unticked to disable Disk Encryption Manager and leave the devices encrypted. Control of BitLocker is returned to the device, with its encryption settings set as they were when Disk Encryption Manager was installed. Ensure that the Recovery Key Report has be run and saved securely for these devices. See Disk Encryption Manager Reporting for details
- Click Save to save the configuration and close the dialog
If the Decrypt hard drives option was selected, BitLocker begins the decryption process on the disk drives of the devices. The users will see a message indicating that the decryption process has started. Once the decryption has completed, Disk Encryption Manager is uninstalled and management is returned the devices BitLocker Installation.
Note that when you decrypt a device, you remove all encryption from all drives. If you need to re-enable encryption, you need to run the encryption process again.
When removing Disk Encryption Manager but leaving devices encrypted, the Boot drive of the devices will have Bitlocker enabled and active, but all other fixed drives will have Bitlocker enabled and suspended. This is due to Disk Encryption Manager tying the protector of all non-boot drives to the Boot drive. When Disk Encryption Manager is removed, Bitlocker requires manual Protectors to be configured (password/pin etc.) using the local Bitlocker instance.
When you remove Disk Encryption Manager and leave the device encrypted, the encryption management is returned to BitLocker on the device. You need to have a record of the current set of Recovery Keys and associated Key ID / Protector ID / Recovery Key ID. Ensure that the Recovery Key Report has been run and saved securely before removing encrypted drives, as these keys are retained for 90 days only after removal.
BitLocker is a native part of the device system. If you chose to remove the Disk Encryption Manager from a device and leave the disk encrypted, you will lose the management capabilities in N-sight RMM. Ensure you collect all recovery keys before choosing this option. You should ALWAYS obtain the Recovery Keys prior to taking any action with Disk Encryption Manager. N-sight RMM only retains the last known valid Recovery Keys for removed devices for up to 90 days only. If something goes wrong with the decryption, and you deleted the device from N-sight RMM, there is no way to recall the Recovery Keys or unlock the drive after the 90 day period.