The Customer Management - Incoming Settings are split into 4 main tabs:
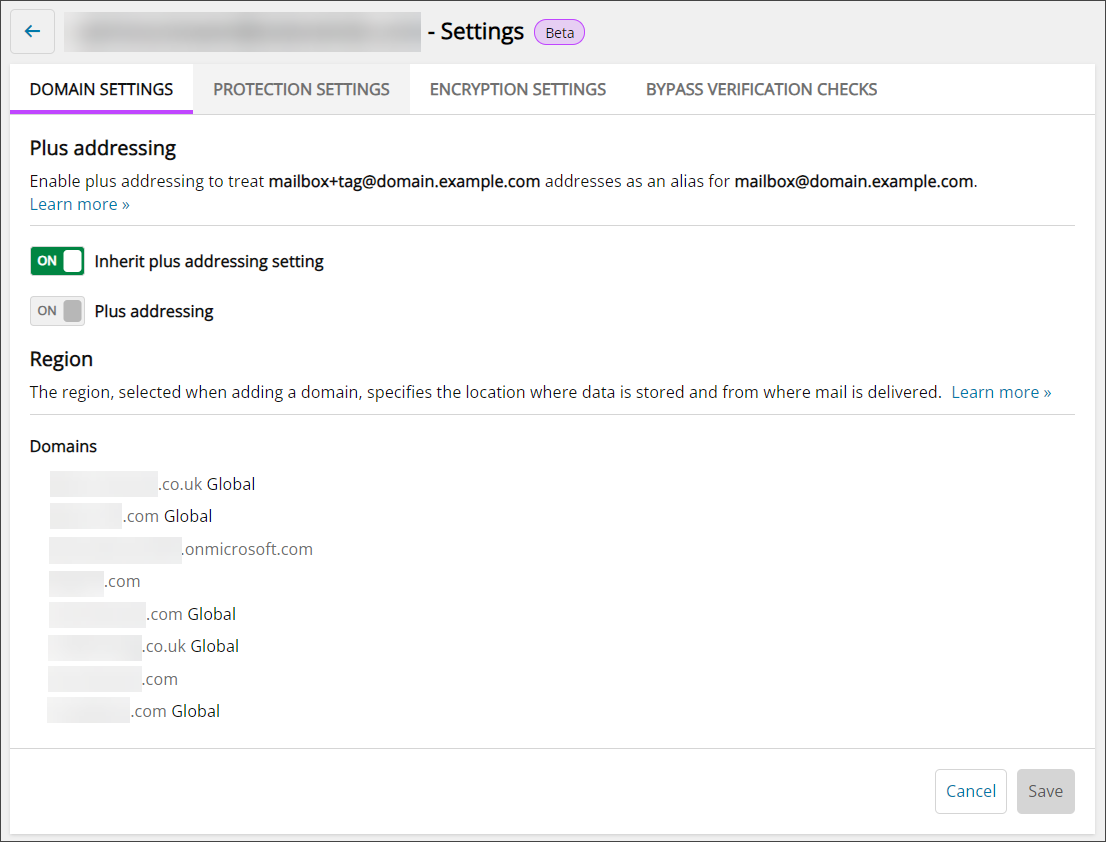
Domain Settings
Plus Addressing
In the Domain Settings tab it is possible to enable or disable Plus Addressing for all domains owned by this Admin or Sub-Admin user.
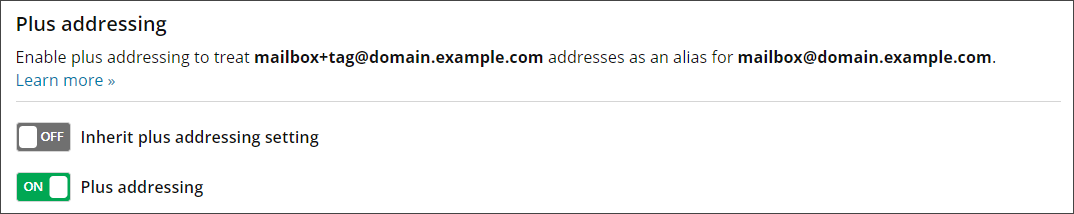
Plus Addressing allows the addition of a 'tag' on a mailbox by use of a '+' as the separating character.
Such addresses should not be added to the mailboxes list, so long as the primary mailbox is.
For example: for the primary mailbox piff.jenkins@example.com, plus addresses such as piff.jenkins+newsletters@example.com, or piff.jenkins+sales@example.com can also be used.
Delivery of mail at the destination server will be done to the full plus address, so the tag may be used for sorting mail in the inbox.
Disable Inherit plus addressing setting to customize this setting for this User's domains.
Save any changes made before switching tabs or the changes will be lost.
Region
The Domains Settings tab also shows the Region of the Domains owned by this Partner/Customer/Site Admin or Sub-Admin and their Sub-Admins.
The region is selected when adding a domain and cannot be changed after. This specifies the geographic location where data is stored and from where mail is delivered.
Protection Settings
Protection Settings is broken into two sub tabs; the General Settings tab, and the Attachment Settings tab.
The Attachment Settings tab will only be visible if the Security Level is set to Custom (either Inherited or selected by User)
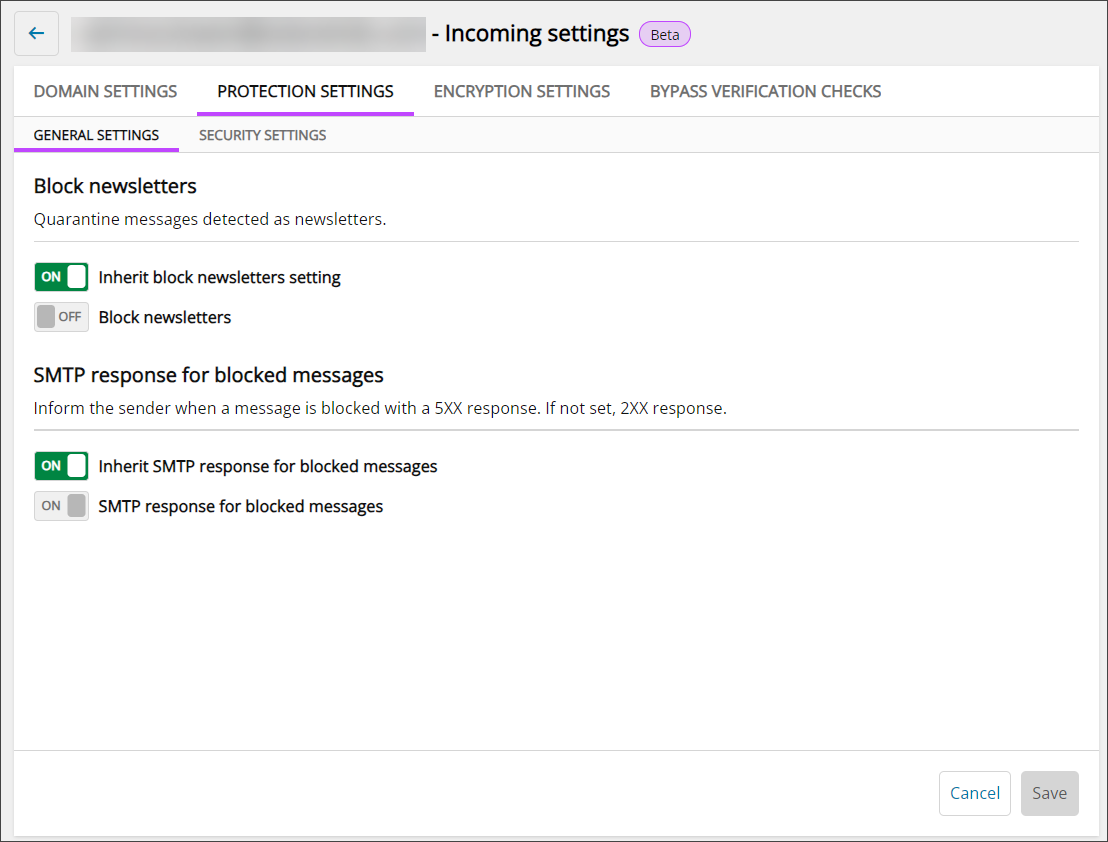
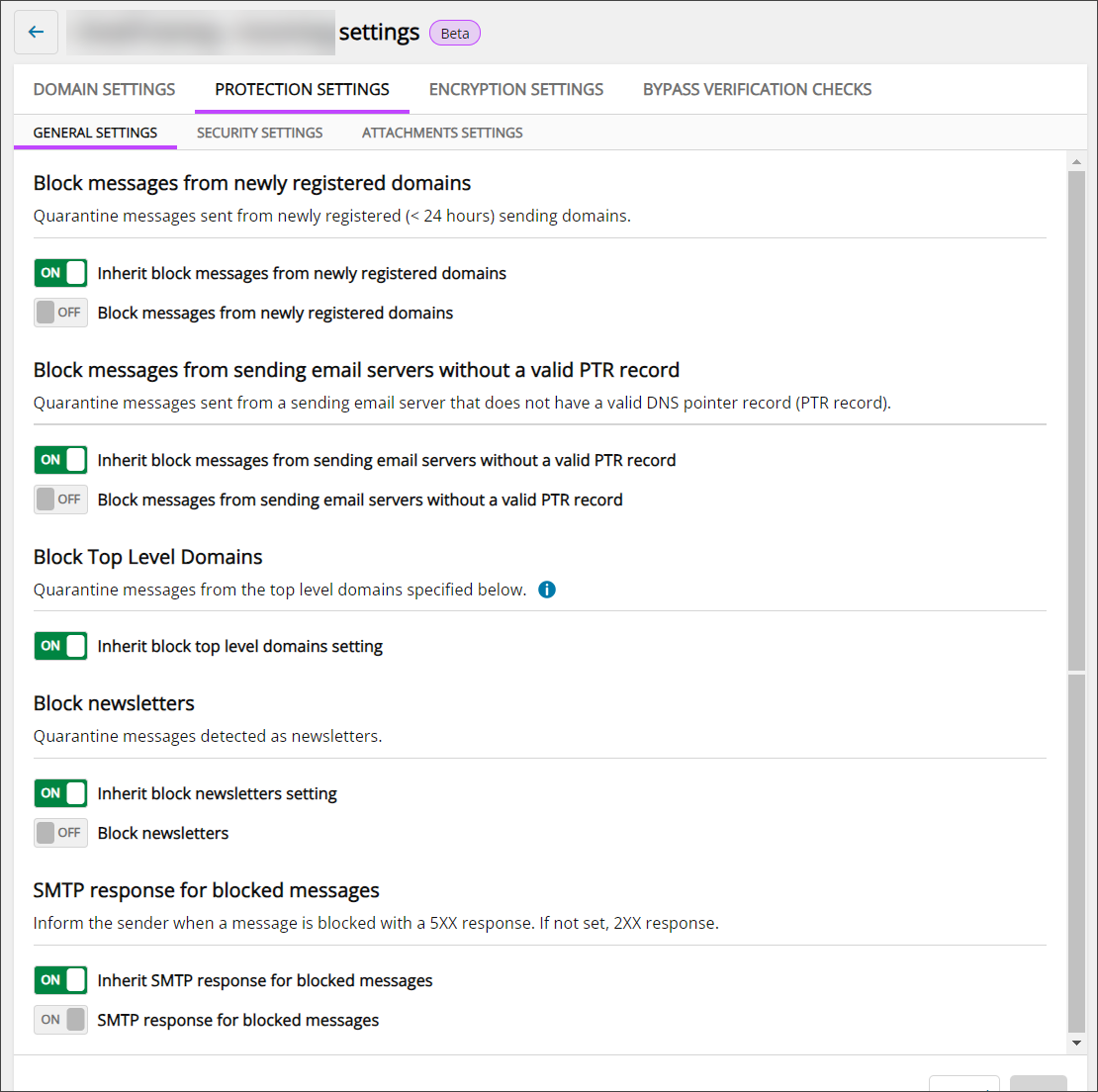
General Settings
The settings displayed on the General Settings tab will change if the Security Level is set to Custom (either Inherited or selected by User).
Pre-set Security Level:
In the General Settings tab when using the Very Low, Low, Medium, High or Very High security levels, you can configure the following settings:
- Block Newsletters - If this setting is On, any email that is detected as a newsletter will be Quarantined
- SMTP response for blocked messages - If this setting is On, senders of messages that have been blocked will be informed of this with a 5XX response. If this setting is off, the sender will not be notified, and the response will be 2XX
Disable the Inherit setting to customize these settings for this User's domains.
Save any changes made before switching tabs or the changes will be lost.
Custom Security Level:
In the General Settings tab when using the Custom security level, you can configure the following settings:
- Block messages from newly registered domains - If this setting is On, any mail from a sending domain that is less than 24 hours old will be Quarantined
- Block messages from sending email servers without a valid PTR record - If this setting is On, any mail from a sending server that does not have a valid DNS pointer record (PTR record) will be Quarantined
- Block Top Level Domains - If this setting is On, mail received from specified top level domains will be Quarantined
If not inherited, select from the dropdown, or type and press Enter to add domains to be blocked
- Block Newsletters - If this setting is On, any email that is detected as a newsletter will be Quarantined
- SMTP response for blocked messages - If this setting is On, senders of messages that have been blocked will be informed of this with a 5XX response. If this setting is off, the sender will not be notified, and the response will be 2XX
Disable the Inherit setting to customize these settings for this User's domains.
Save any changes made before switching tabs or the changes will be lost.
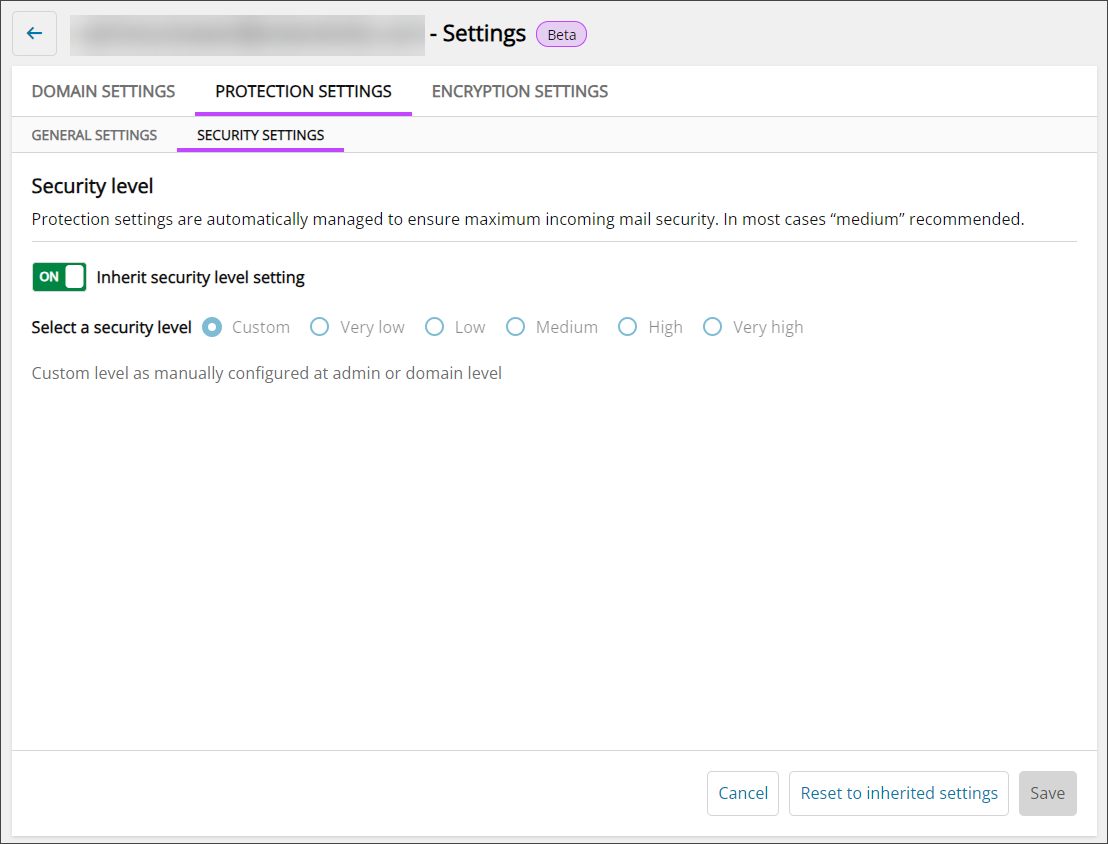
Security Settings
Security Level
The Security Level setting allows configuration of how restrictive the spam filter is for any domains owned by the Admin or Sub-Admin, or any child Sub-Admin's that inherit this setting.
Disable the Inherit setting to customize this setting for this User's domains.
The choices for security level are:
| Security Level | Amount of Protection |
|---|---|
| Custom | The level of protection as configured in the Attachment Settings > Restriction Options section or in the Manage Attachment Restrictions page |
| Very Low |
Limited protection: Skip most classifications that are likely to catch unwanted mail
|
| Low |
Some protection: Allow some classifications that may capture legitimate messages
|
| Medium |
Optimal settings for most users: Capture the most spam and the fewest false positives
|
| High |
More aggressive filtering for more capturing more potential spam: Some false positives are possible
|
| Very High |
Enables maximum protection with highest risk of legitimate messages being detected as spam
|
The selected Security Level from Very Low to Very High will overwrite the Filter Settings configured at the Domain Level. For the Custom Security Level, settings will not be overwritten.
Save any changes made before switching tabs or the changes will be lost.
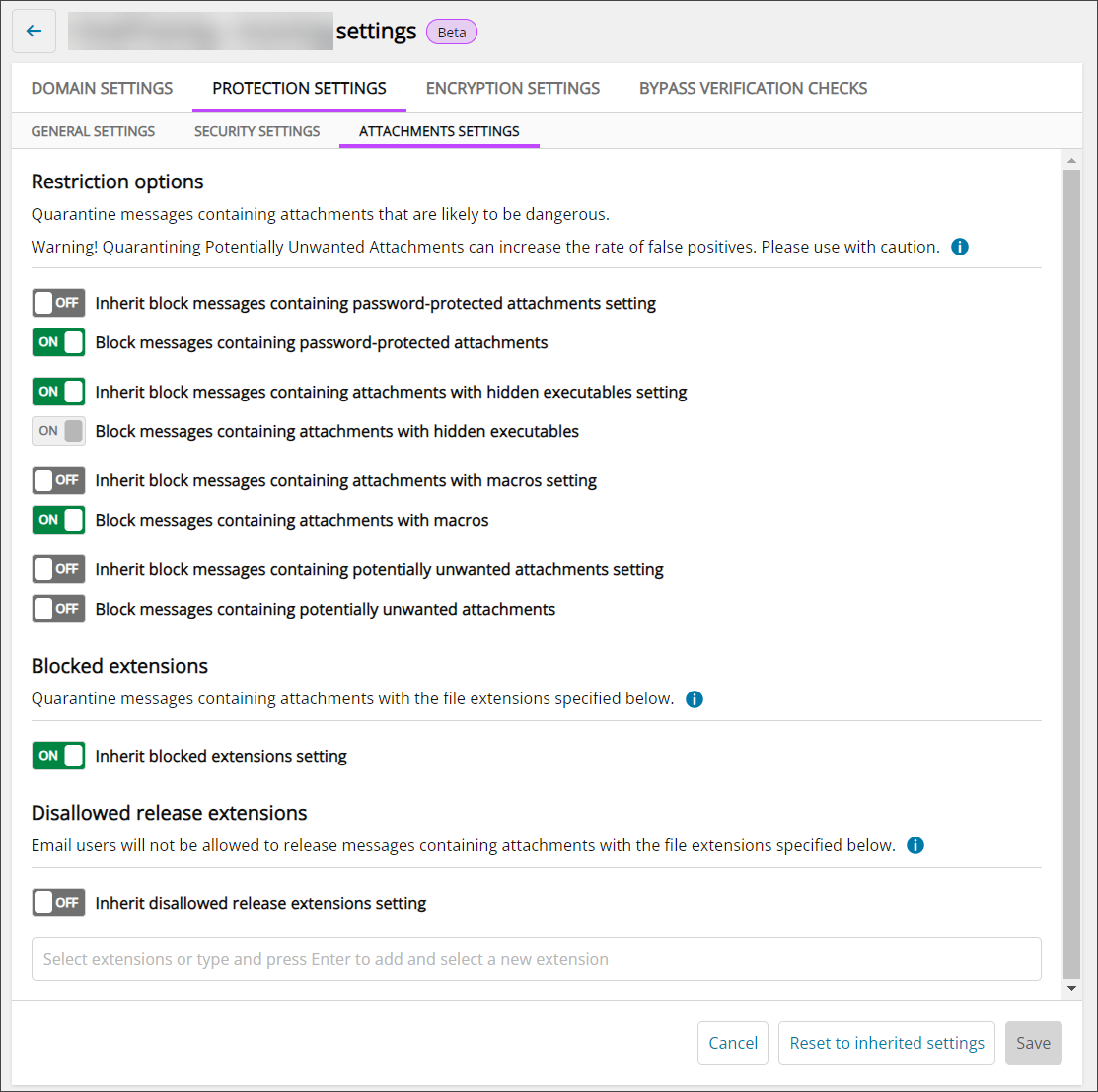
Attachment Settings
These settings will only be visible if the Security Level on the General Settings tab is set to Custom.
Restriction Options
The settings that can be configured in here are:
- Block messages with password-protected attachments - If this is On, all inbound mail containing a password-protected attachment (such as Zip files) will be sent straight to the quarantine and must be reviewed manually to be checked if it is legitimate
- Block messages containing attachments with hidden executables - If this is On, all inbound mail containing attachments with hidden executables (such as ZIP, TAR, GZIP, BZIP2 and 7Z archives (other than those compressed with deflate64)) will be sent straight to the quarantine and must be reviewed manually to be checked if it is legitimate
- Block messages containing attachments with macros - If this is On, all inbound mail with a document based attachment (.doc, .xls, .ppt etc) that contains any kind of macro will be sent straight to the quarantine and must be reviewed manually to be checked if it is legitimate
- Block messages containing potentially unwanted attachments - If this is On, all inbound mail containing attachments considered dangerous or unwanted will be sent straight to the quarantine and must be reviewed manually to be checked if it is legitimate. For example, compressed executable files (e.g. UPX packers), password tools, network tools, peer-to-peer clients, remote access applications, system tools, spying tools and documents containing scripts
Disable the Inherit setting to customize the settings for this User's domains.
Blocked Extensions
This setting Quarantines messages that have attachments with the specified file extensions.
If not inherited, select extensions from the dropdown, or type and press Enter to add extensions to be blocked
Disallowed Release Extensions
This setting will stop Email Users from being able to release messages that have attachments with the specified file extensions.
If not inherited, select extensions from the dropdown, or type and press Enter to add extensions to be blocked
Save any changes made before switching tabs or the changes will be lost.
Encryption Settings
You can configure TLS and DANE from the Encryption Settings tab.
This will apply the appropriate TLSA (Transport Layer Security Authentication) records and DNSSEC (Domain Name System Security Extensions) protocol to secure SMTP traffic.
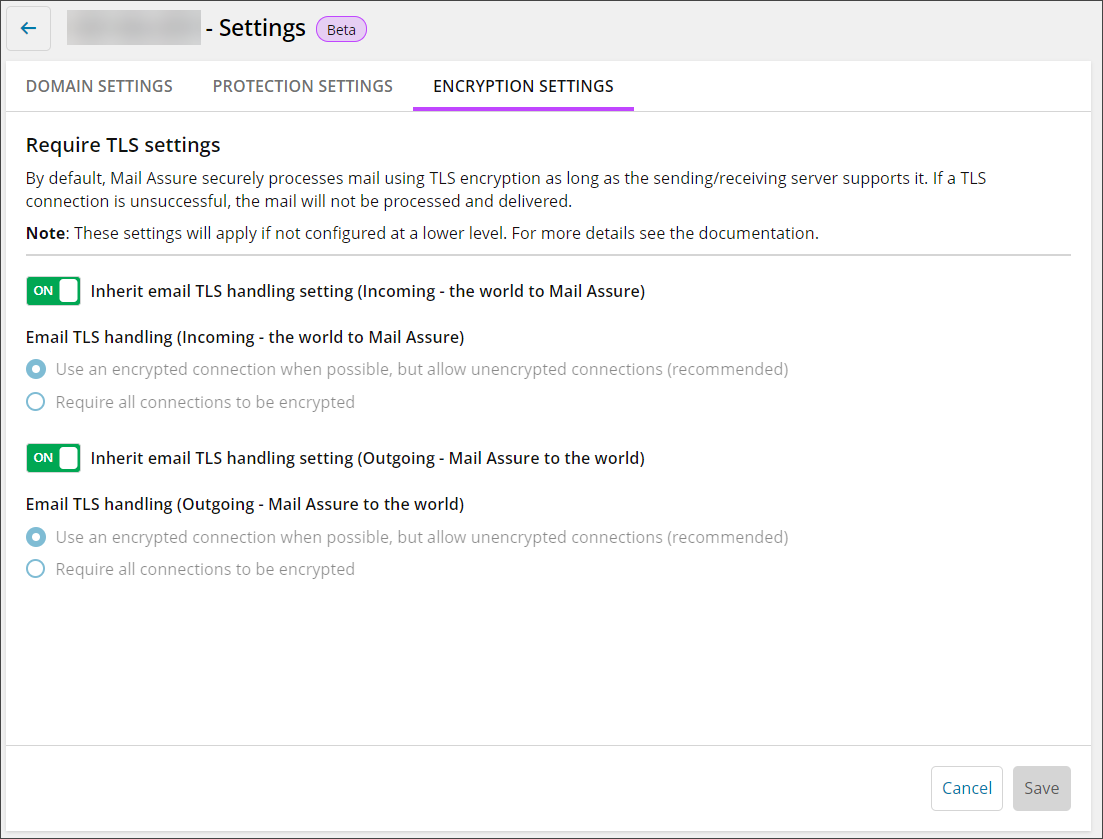
TLS Settings
In the Encryption Settings tab, TLS encryption settings can be configured for both Incoming and Outgoing mail.
By default, all email processed by Mail Assure is done securely using TLS encryption as long as the sending/receiving server provides support for it.
Using these settings, you can specify to use TLS is when possible, but also to allow unencrypted connections or set it so that TLS is compulsory for all connections; if a TLS connection is unsuccessful the email will not be processed or delivered.
Disable the Inherit settings to customize email TLS handling for this User's domains.
Save any changes made before switching tabs or the changes will be lost.
DANE Settings
You can configure DANE (DNS-based Authentication of Named Entities) for incoming mail currently.
Incoming email for managed host names (either direct or through an inheritance rule) will be processed by Mail Assure to use DANE, as long as the receiving server supports DNSSEC (DNS Security Extensions). DANE adds an additional layer of security to inbound email for filtered domains through DNSSEC-backed certificates. However, for DANE to work correctly, destination servers must:
-
Support and be set up correctly for DNSSEC. DNSSEC must be fully operational and validated before you use DANE.
-
Use host names, not IP addresses for receiving servers.
-
Have STARTTLS capability for connections from the filtered IP delivery addresses.
-
Have a valid TLS certificate installed.
Before enforcing DANE validation for specific host names, make sure that your destination server supports this protocol. If the DANE validation fails on the destination server, the mail delivery is blocked.
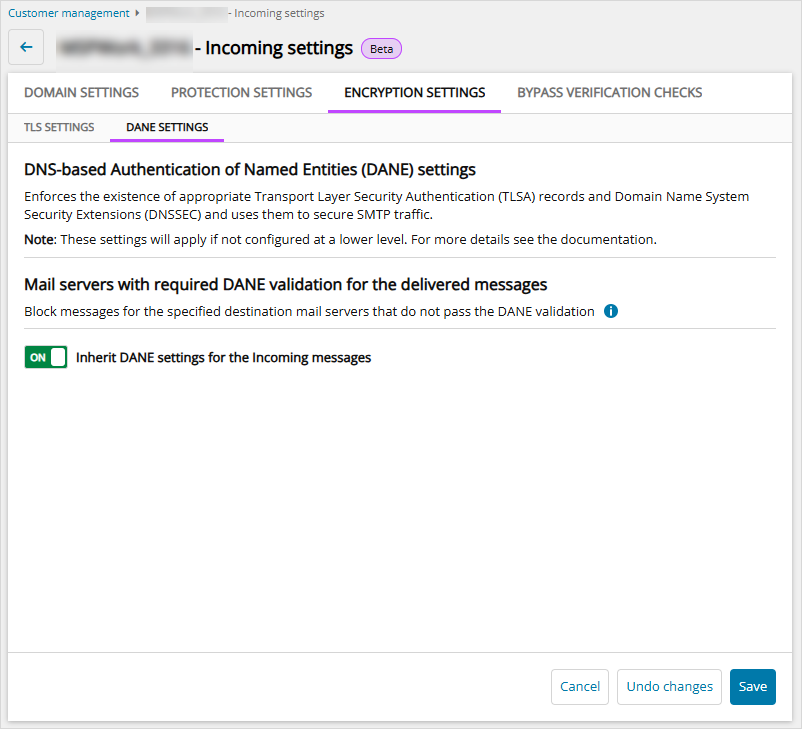
Disable the Inherit setting to customize the host names from which Mail Assure should inherit the DANE settings.
Save any changes made before switching tabs or the changes will be lost.
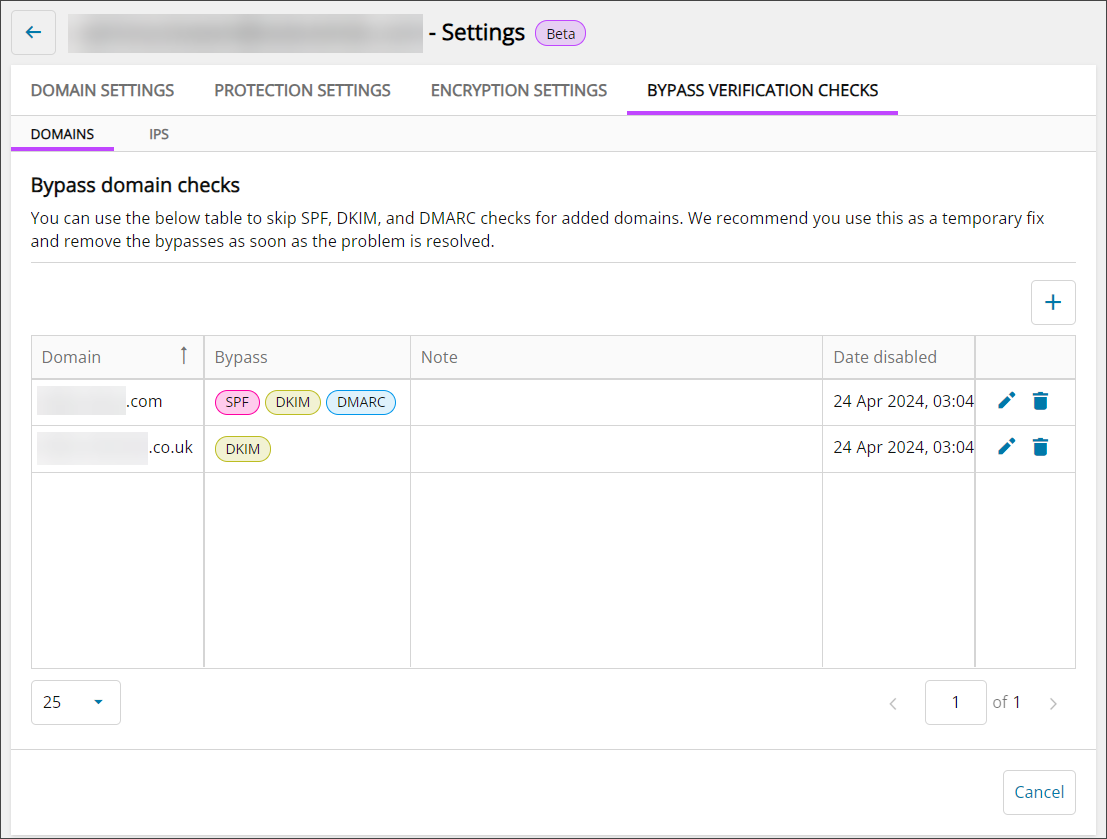
Bypass Verification Checks
The Bypass Verification Checks tab is broken into two sub tabs; the Domains tab, and the IPs tab.
Domains
Add domains to the table to skip SPF, DKIM or DMARC checks so that if, for example, an SPF check fails for any of the specified domains, the system will continue to process the message.
To add domains to the list:
- Click the + icon
- Enter the Domain name
-
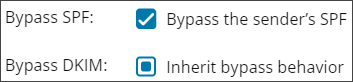
To inherit bypass behavior, click the checkbox once to fill it with a solid square
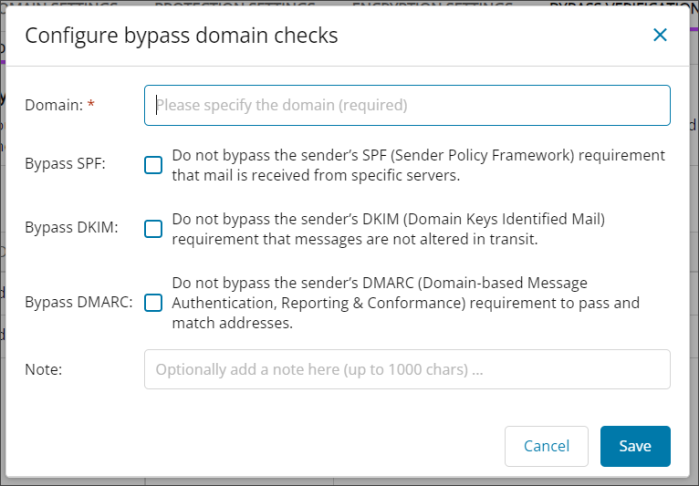
- To bypass the check entirely, click the checkbox twice until you see a tick
- Optionally, you can add a note
- Click Save
The domain and checks selected to bypass will be added to the list.
IPs
Add IP addresses to the table to skip sender SPF checks and DMARC checks so that if, for example, an SPF check and a DMARC check fail for any of the specified sender IPs, the system will continue to process the message.
To add IP addresses to the list:
- Click the + icon
- Enter the IP address
-
Ensure the checkboxes are selected to bypass the sender's SPF and DMARC
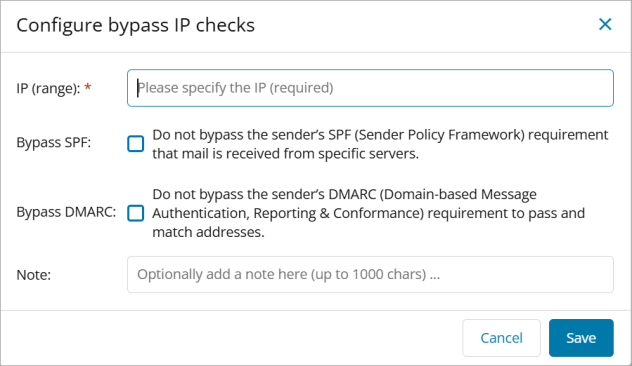
The following inherit message displays once the checkboxes are selected to bypass the sender's SPF and DMARC:
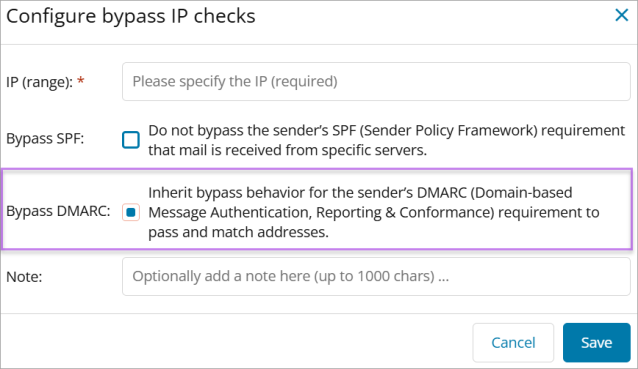
-
Click the checkbox twice until you see a tick to bypass the check entirely
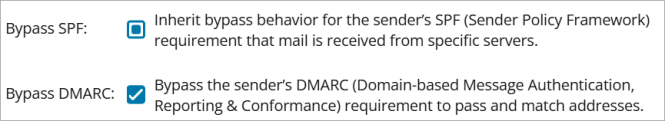
- Optionally, you can add a note
- Click Save
The IP will be added to the list.