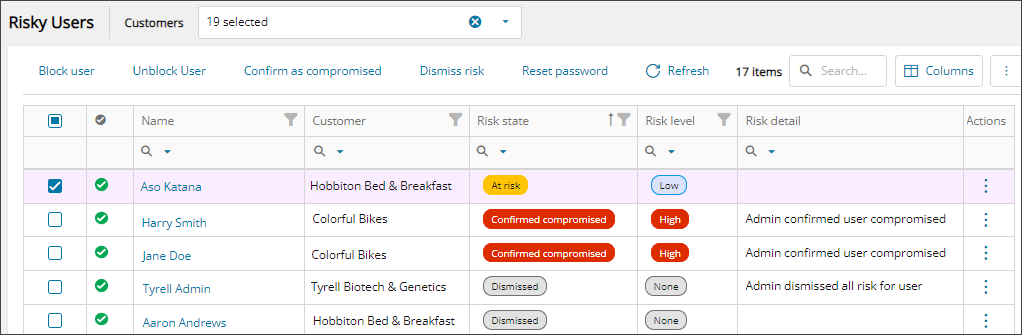
View risky users
Cloud Commander will be decommissioned and stop functioning on May 13, 2026. You can use the product until that date.
Review and update workflows to remove any dependencies before the product is decommissioned.
Support, bug fixes, and security patches will be available until April 13, 2026.
On the risky user list, search and filter to find a specific risky user, risk state, risk level and more, and use the available actions to Manage risky users.
Prerequisites
- You must be assigned the Identity Protection Writer or Reader role scoped to the tenant.
- To view and manage your customer's risky users in Cloud Commander, your customer must have a user in the tenant with Microsoft Entra ID P2 license. Microsoft requires a P2 license to access the risky users API, which Cloud Commander uses to gather the data.
View risky users
- In the , select
 Security > Risky Users.
Security > Risky Users. - Use the customer selector to choose the customers you want to view data for.
- Filter or search to find users at risk. For example, use the Risk state or Risk level column filters to quickly see users at risk.
The list of risky users displays. You can filter and search the data, choose the columns to display, and export to Microsoft Excel. See Navigation and tools for table options.
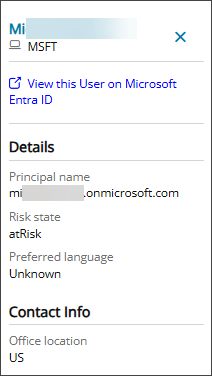
- Click in the row for a user to see more details in the right panel, such as office location and preferred language. If you use the link to view the user on Microsoft Entra ID, you'll need to sign as a user of the specific organization rather than using your Cloud Commander user credentials.
Risk column descriptions
- Risk state: State of the user's risk. The possible values are:
- Safe: After investigation, the user account is verified as safe. There is no evidence of compromise or malicious activity. The account is considered secure, and no further immediate actions are needed.
- Dismissed: The risk alert for the user account has been reviewed and determined to be a false positive or not a significant threat. The alert is dismissed, indicating no further action is required at this time. The account is not considered at risk.
- Remediated: The security threat associated with the user account has been addressed and resolved. Remediation steps are successfully implemented to mitigate the risk and restore the account to a secure state.
- At risk: The user account is currently flagged as being at risk based on detected suspicious activities or security alerts. The account has not yet been confirmed as compromised, but further investigation is recommended to determine the severity of the threat.
- Compromised: The user account is verified as compromised. This confirmation is based on investigation and evidence of malicious activities or unauthorized access. Immediate action is required to mitigate the risk and secure the account.
- Risk level: An indicator of the probability that the user's account is compromised. The possible values are low, medium, high, hidden, none.
- Risk detail: Details that contributed to the risk level. The possible values are:
- None
- Admin generated temporary password
- User performed secured password change
- User performed secured password reset
- Admin confirmed sign in safe
- AI confirmed sign in safe
- User passed MFA driven by risk based policy
- Admin dismissed all risk for user
- Admin confirmed sign in compromised
- Admin confirmed user compromised
- Admin confirmed service principal compromised
- Admin dismissed all risk for service principal
- m365 Admin dismissed detection
- User changed password on premises
- Admin dismissed risk for sign in
- Admin confirmed account safe
- Risk updated: The date and time the risky user was last updated.
Next steps
Related articles
Updated: Jan 09, 2026