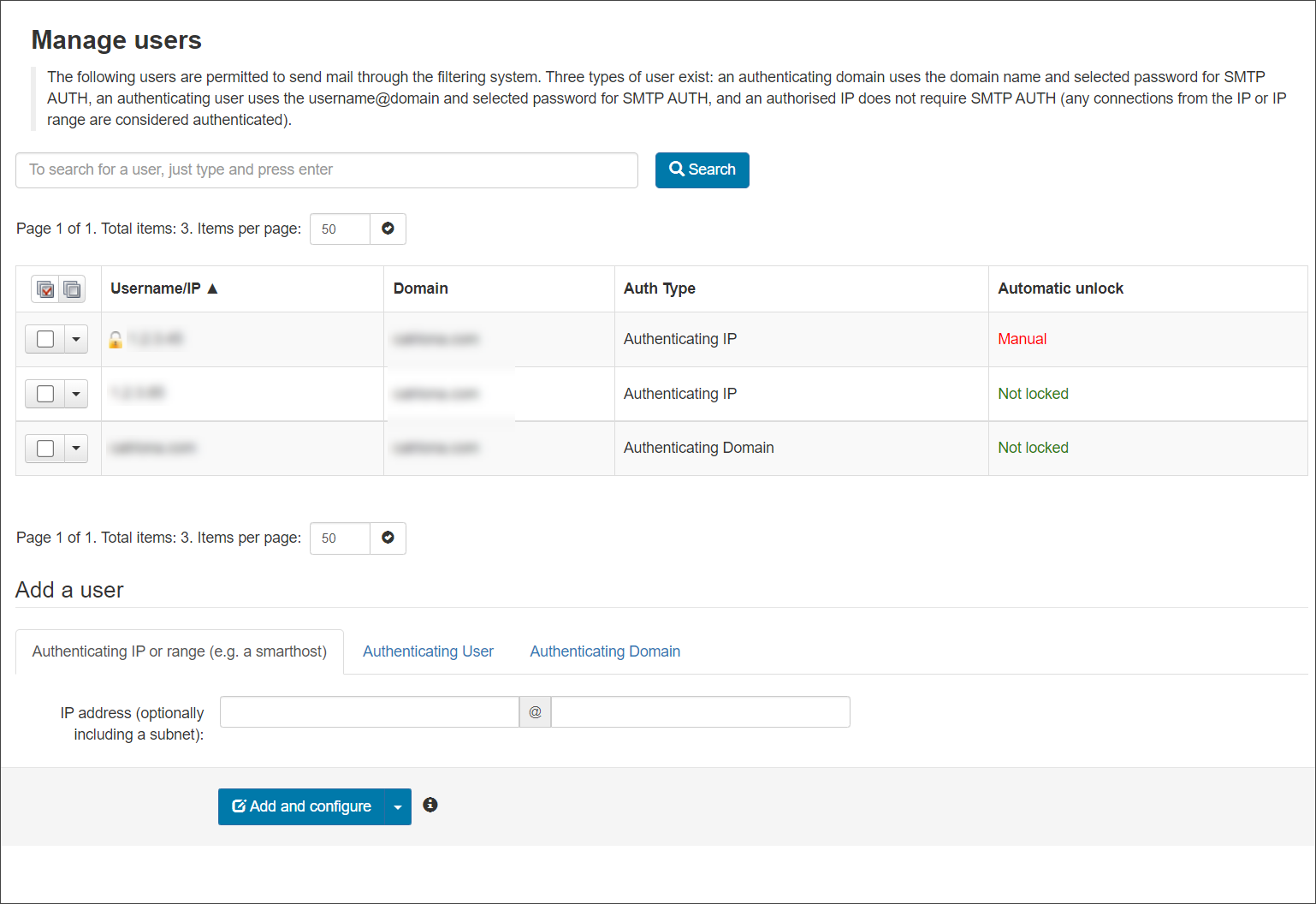
- When logged in to the Admin Level Control Panel, navigate Outgoing > Manage Users or at the Domain level Control Panel, open the Outgoing > Manage Authentication page
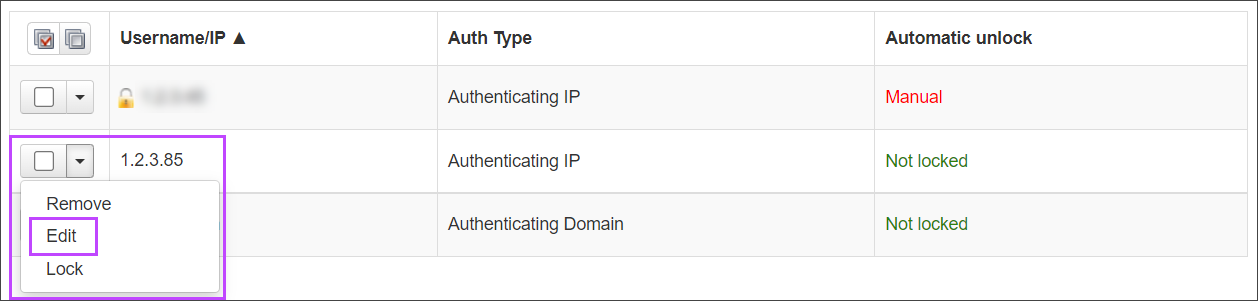
- Click on the dropdown alongside the method you want to edit
- Select Edit
- Configure the following user settings as required:
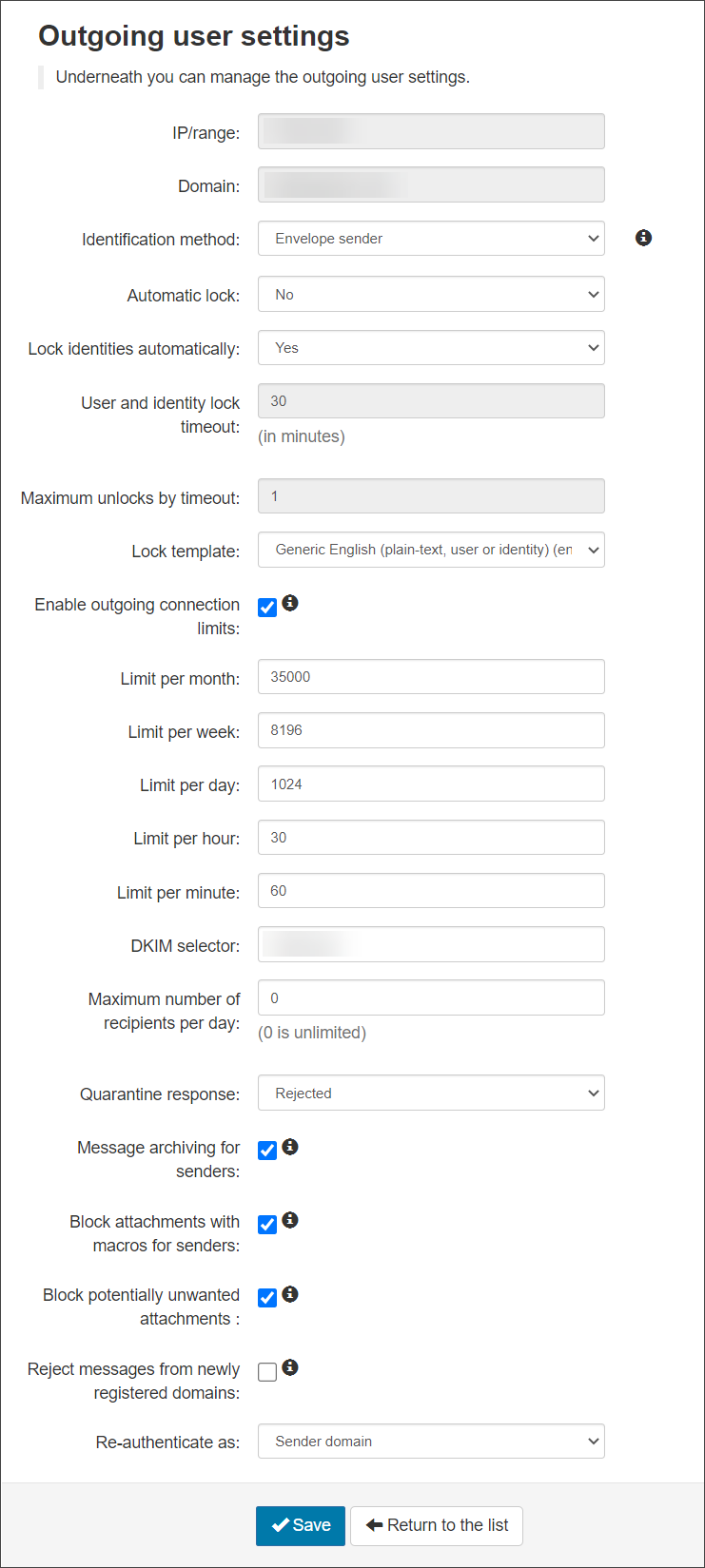
- IP/Range - This is the IP Address or IP Range provided in step 3.
This cannot be changed
- Identification Method - Choose from: “envelope sender”, “authentication user” or “Header” as the identification method (See the Manage Identities page for more details)
Envelope Sender Use this if your system enforces the “envelope sender” (or MAIL FROM value). This is typically used by Spam Experts users. Authentication User The outgoing user’s authentication details. This is the best choice when you are providing unique usernames and passwords for each outgoing user, rather than using a smarthost system. Header If you choose this option, you are able to add any number of identification headers that we should search for in the message. For example, you might have a system that adds an “X-Client-ID” header, which uniquely identifies each of your end users. For each header, you may choose to either use the entire header value as the identity, or you can provide a regular expression that extracts out a part of the value to use. You may also choose to have our software remove the header after we have found the identity, if you don’t want this to be available to the recipient of the message.
We strongly recommend that an identity Header is set for all outgoing traffic. This makes monitoring and taking action against spammers much easier.
- Automatic lock - When enabled, and when the system detects that the user has sent approx 5 spam messages in 10 minutes, the user will be locked automatically. The user cannot send mail until they are unlocked (the administrator can do this from the alert sent or from the Outgoing Users/Authentication Methods page)
We recommend that you do not enable the Automatic lock if you are using IP authentication within a smarthost.
- Lock Identities Automatically - This spam prevention, when enabled and the system detects that the identity has sent approx 5 spam messages in 10 minutes, the identity will be locked automatically. The identity cannot send mail until they have been unlocked. The identity can be unlocked from the Manage Identities page
- User and Identity Lock timeout - The amount of time an outgoing user or identity will be unable to send messages. This only applies to if you are using the Automatic User Lock or the Automatic Identity Lock
- Maximum unlocks by timeout - The maximum number of times the user will be automatically unlocked after the time-out value has passed. After this has been depleted, the user will have to be manually unlocked
- Lock Template - Select the email template to be used to inform the user of the lock
- Enable outgoing connection limits - Enable or disable limits on outgoing connections whether spam or not, to prevent bulk mailing
Only enable limits when preventing unusual volume of SMTP connections for the following time frames:
- Limit per month - The amount of outgoing connections that can be opened per month
- Limit per week - The amount of outgoing connections that can be opened per week
- Limit per day - The amount of outgoing connections that can be opened per day
- Limit per hour - The amount of outgoing connections that can be opened per hour
- Limit per minute - The amount of outgoing connections that can be opened per minute
- Valid Sender Address Required - (Available at Super-Admin Level only) When enabled, the filtering servers do a 'null sender' callout to verify the sender. This means that the filtering server will connect to the sending address mailserver, using a sender of "<>" (as a bounce message does), and the specified sender as the RCPT To. After checking the sender, the connection will be properly closed (i.e. no message is actually sent). This is a good way to stop spammers and we recommend having this option enabled
- DKIM Selector- Choose the selector you wish to use at domain level. Use the default or add one that has been generated using the DKIM Certificate Generation tool. Once you have created the certificate you need to add the TXT to your DNS
For Example, if you generate a key for selector
mailassure1, publish the DKIM Key under the DNS Recordmailassure1._domainkey.example.invalid. Then entermailassure1in this DKIM Selector field on Spam Experts. - Maximum number of recipients per day - The maximum number of SMTP recipients the authenticating method can send emails to in a 24 hour period
- Quarantine Response – When an outgoing message is detected as spam and it goes into the outgoing quarantine, the response you send back to the sending server can be Rejected or Accepted
- If 'Rejected' (550), legitimate senders will receive a bounce message when their mail gets blocked and quarantined even though the message is stored in the quarantine
- If 'Accepted' (250), the SMTP response would be ‘Accept’ and the message would still be blocked and shown in the quarantine but the sender will not receive a bounce message and will not know that the message is in the outgoing quarantine
The administrator will be notified that there are messages in the outgoing quarantine with an Abuse Report (ARF) if the Administrator’s contact email address has been added into the Outgoing > Settings page in the Domain Level Control Panel (see Configure the Abuse Report Address). Alternatively, use the Email Scout Reports to create a schedule report with details of outgoing quarantine content.
- Message archiving for senders - Enabled/Disabled – If enabled, submission messages will be added to the archiving account of the envelope sender's domain. See Enable Archiving for Outgoing Mail.
- Block attachments with macros for senders - If enabled, any message with a document based attachment that contains any kind of macro will be rejected
- Block potentially unwanted attachments - If enabled, any messages with an attachment that is considered dangerous or otherwise unwanted will be rejected
This restriction applies to Outbound messages only, to apply this restriction for Inbound mail, see Manage Attachment Restrictions.
- Reject messages from newly registered domains - (if available) If set, then any message sent from a domain that is newly registered (less than a day) will be rejected
- Re-authenticate as - Using the dropdown select how you want the IP/Range to be authenticated
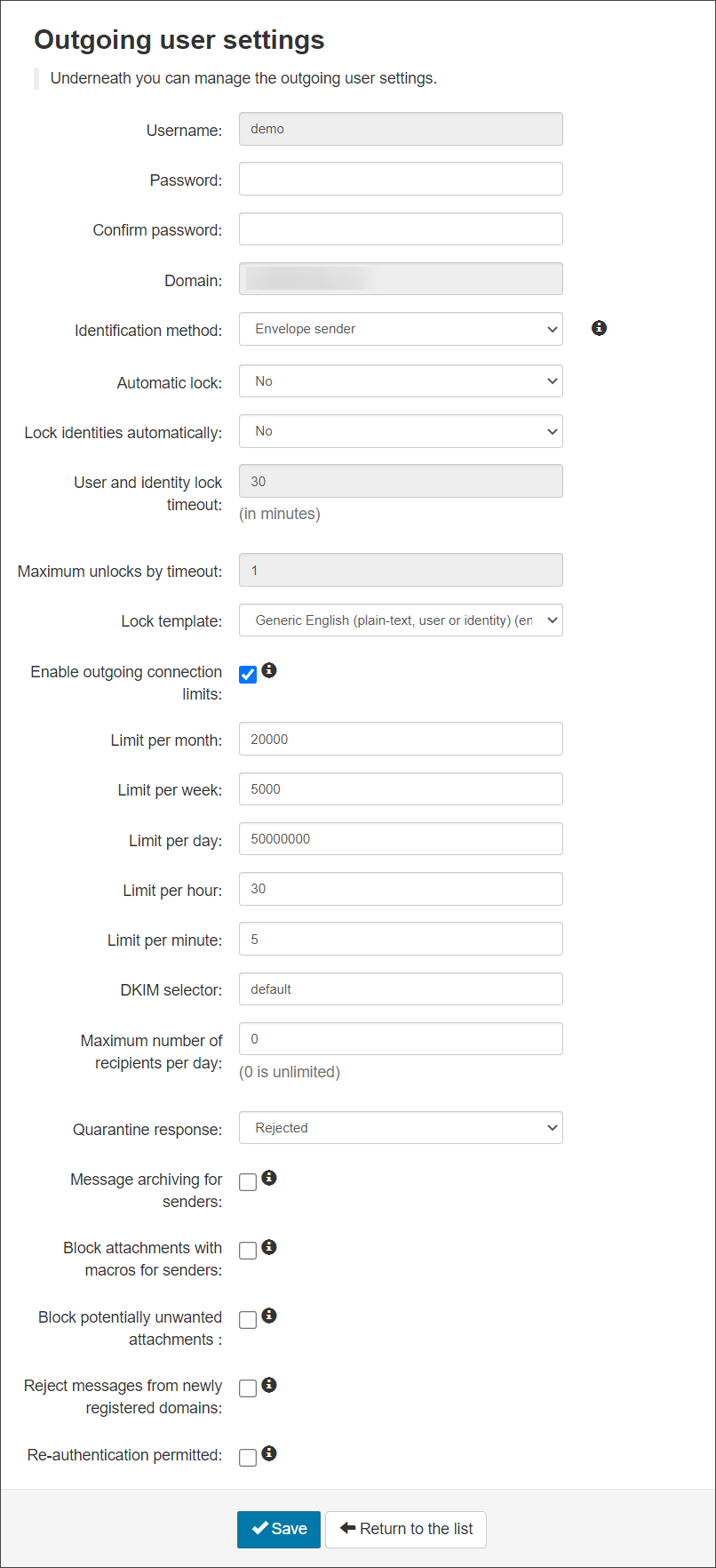
- Username - This is the IP Address or IP Range provided in step 3
This cannot be changed
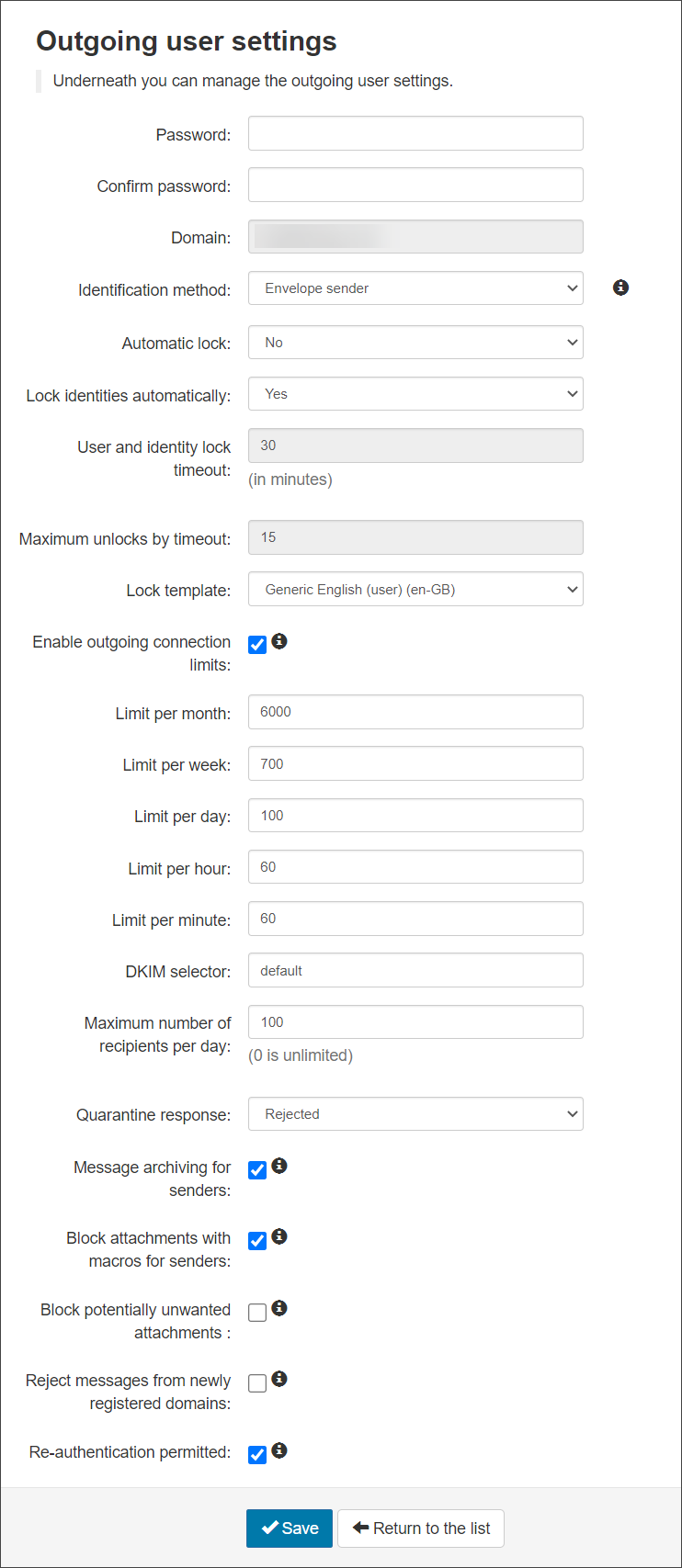
- Password - Create or change the password for the authenticating user
- Confirm Password - Confirm the password
- Identification Method - Choose from: “envelope sender”, “authentication user” or “Header” as the identification method (See the Manage Identities page for more details)
Envelope Sender Use this if your system enforces the “envelope sender” (or MAIL FROM value). This is typically used by Spam Experts users. Authentication User The outgoing user’s authentication details. This is the best choice when you are providing unique usernames and passwords for each outgoing user, rather than using a smarthost system. Header If you choose this option, you are able to add any number of identification headers that we should search for in the message. For example, you might have a system that adds an “X-Client-ID” header, which uniquely identifies each of your end users. For each header, you may choose to either use the entire header value as the identity, or you can provide a regular expression that extracts out a part of the value to use. You may also choose to have our software remove the header after we have found the identity, if you don’t want this to be available to the recipient of the message.
We strongly recommend that an identity Header is set for all outgoing traffic. This makes monitoring and taking action against spammers much easier.
- Automatic lock - When enabled, and when the system detects that the user has sent approx 5 spam messages in 10 minutes, the user will be locked automatically. The user cannot send mail until they are unlocked (the administrator can do this from the alert sent or from the Outgoing Users/Authentication Methods page)
We recommend that you do not enable the Automatic lock if you are using IP authentication within a smarthost.
- Lock Identities Automatically - This spam prevention, when enabled and the system detects that the identity has sent approx 5 spam messages in 10 minutes, the identity will be locked automatically. The identity cannot send mail until they have been unlocked. The identity can be unlocked from the Manage Identities page
- User and Identity Lock timeout - The amount of time an outgoing user or identity will be unable to send messages. This only applies to if you are using the Automatic User Lock or the Automatic Identity Lock
- Maximum unlocks by timeout - The maximum number of times the user will be automatically unlocked after the time-out value has passed. After this has been depleted, the user will have to be manually unlocked
- Lock Template - Select the email template to be used to inform the user of the lock
- Enable outgoing connection limits - Enable or disable limits on outgoing connections whether spam or not, to prevent bulk mailing
Only enable limits when preventing unusual volume of SMTP connections for the following time frames:
- Limit per month - The amount of outgoing connections that can be opened per month
- Limit per week - The amount of outgoing connections that can be opened per week
- Limit per day - The amount of outgoing connections that can be opened per day
- Limit per hour - The amount of outgoing connections that can be opened per hour
- Limit per minute - The amount of outgoing connections that can be opened per minute
- Valid Sender Address Required - (Available at Super-Admin Level only) When enabled, the filtering servers do a 'null sender' callout to verify the sender. This means that the filtering server will connect to the sending address mailserver, using a sender of "<>" (as a bounce message does), and the specified sender as the RCPT To. After checking the sender, the connection will be properly closed (i.e. no message is actually sent). This is a good way to stop spammers and we recommend having this option enabled
- DKIM Selector- Choose the selector you wish to use at domain level. Use the default or add one that has been generated using the DKIM Certificate Generation tool. Once you have created the certificate you need to add the TXT to your DNS
For Example, if you generate a key for selector
mailassure1, publish the DKIM Key under the DNS Recordmailassure1._domainkey.example.invalid. Then entermailassure1in this DKIM Selector field on Spam Experts. - Maximum number of recipients per day - The maximum number of SMTP recipients the authenticating method can send emails to in a 24 hour period
- Quarantine Response – When an outgoing message is detected as spam and it goes into the outgoing quarantine, the response you send back to the sending server can be Rejected or Accepted
- If 'Rejected' (550), legitimate senders will receive a bounce message when their mail gets blocked and quarantined even though the message is stored in the quarantine
- If 'Accepted' (250), the SMTP response would be ‘Accept’ and the message would still be blocked and shown in the quarantine but the sender will not receive a bounce message and will not know that the message is in the outgoing quarantine
The administrator will be notified that there are messages in the outgoing quarantine with an Abuse Report (ARF) if the Administrator’s contact email address has been added into the Outgoing > Settings page in the Domain Level Control Panel (see Configure the Abuse Report Address). Alternatively, use the Email Scout Reports to create a schedule report with details of outgoing quarantine content.
- Message archiving for senders - Enabled/Disabled – If enabled, submission messages will be added to the archiving account of the envelope sender's domain. See Enable Archiving for Outgoing Mail.
- Block attachments with macros for senders - If enabled, any message with a document based attachment that contains any kind of macro will be rejected
- Block potentially unwanted attachments - If enabled, any messages with an attachment that is considered dangerous or otherwise unwanted will be rejected
This restriction applies to Outbound messages only, to apply this restriction for Inbound mail, see Manage Attachment Restrictions.
- Reject messages from newly registered domains - (if available) If set, then any message sent from a domain that is newly registered (less than a day) will be rejected
- Re-authenticate permitted - If enabled, authorized servers will be able to relay email on behalf of this user
- Password - Create or change the password for the authenticating domain.
- Confirm Password - Confirm the password.
- Identification Method - Choose from: “envelope sender”, “authentication user” or “Header” as the identification method (See the Manage Identities page for more details)
Envelope Sender Use this if your system enforces the “envelope sender” (or MAIL FROM value). This is typically used by Spam Experts users. Authentication User The outgoing user’s authentication details. This is the best choice when you are providing unique usernames and passwords for each outgoing user, rather than using a smarthost system. Header If you choose this option, you are able to add any number of identification headers that we should search for in the message. For example, you might have a system that adds an “X-Client-ID” header, which uniquely identifies each of your end users. For each header, you may choose to either use the entire header value as the identity, or you can provide a regular expression that extracts out a part of the value to use. You may also choose to have our software remove the header after we have found the identity, if you don’t want this to be available to the recipient of the message.
We strongly recommend that an identity Header is set for all outgoing traffic. This makes monitoring and taking action against spammers much easier.
- Automatic lock - When enabled, and when the system detects that the user has sent approx 5 spam messages in 10 minutes, the user will be locked automatically. The user cannot send mail until they are unlocked (the administrator can do this from the alert sent or from the Outgoing Users/Authentication Methods page)
We recommend that you do not enable the Automatic lock if you are using IP authentication within a smarthost.
- Lock Identities Automatically - This spam prevention, when enabled and the system detects that the identity has sent approx 5 spam messages in 10 minutes, the identity will be locked automatically. The identity cannot send mail until they have been unlocked. The identity can be unlocked from the Manage Identities page
- User and Identity Lock timeout - The amount of time an outgoing user or identity will be unable to send messages. This only applies to if you are using the Automatic User Lock or the Automatic Identity Lock
- Maximum unlocks by timeout - The maximum number of times the user will be automatically unlocked after the time-out value has passed. After this has been depleted, the user will have to be manually unlocked
- Lock Template - Select the email template to be used to inform the user of the lock
- Enable outgoing connection limits - Enable or disable limits on outgoing connections whether spam or not, to prevent bulk mailing
Only enable limits when preventing unusual volume of SMTP connections for the following time frames:
- Limit per month - The amount of outgoing connections that can be opened per month
- Limit per week - The amount of outgoing connections that can be opened per week
- Limit per day - The amount of outgoing connections that can be opened per day
- Limit per hour - The amount of outgoing connections that can be opened per hour
- Limit per minute - The amount of outgoing connections that can be opened per minute
- Valid Sender Address Required - (Available at Super-Admin Level only) When enabled, the filtering servers do a 'null sender' callout to verify the sender. This means that the filtering server will connect to the sending address mailserver, using a sender of "<>" (as a bounce message does), and the specified sender as the RCPT To. After checking the sender, the connection will be properly closed (i.e. no message is actually sent). This is a good way to stop spammers and we recommend having this option enabled
- DKIM Selector- Choose the selector you wish to use at domain level. Use the default or add one that has been generated using the DKIM Certificate Generation tool. Once you have created the certificate you need to add the TXT to your DNS
For Example, if you generate a key for selector
mailassure1, publish the DKIM Key under the DNS Recordmailassure1._domainkey.example.invalid. Then entermailassure1in this DKIM Selector field on Spam Experts. - Maximum number of recipients per day - The maximum number of SMTP recipients the authenticating method can send emails to in a 24 hour period
- Quarantine Response – When an outgoing message is detected as spam and it goes into the outgoing quarantine, the response you send back to the sending server can be Rejected or Accepted
- If 'Rejected' (550), legitimate senders will receive a bounce message when their mail gets blocked and quarantined even though the message is stored in the quarantine
- If 'Accepted' (250), the SMTP response would be ‘Accept’ and the message would still be blocked and shown in the quarantine but the sender will not receive a bounce message and will not know that the message is in the outgoing quarantine
The administrator will be notified that there are messages in the outgoing quarantine with an Abuse Report (ARF) if the Administrator’s contact email address has been added into the Outgoing > Settings page in the Domain Level Control Panel (see Configure the Abuse Report Address). Alternatively, use the Email Scout Reports to create a schedule report with details of outgoing quarantine content.
- Message archiving for senders - Enabled/Disabled – If enabled, submission messages will be added to the archiving account of the envelope sender's domain. See Enable Archiving for Outgoing Mail.
- Block attachments with macros for senders - If enabled, any message with a document based attachment that contains any kind of macro will be rejected
- Block potentially unwanted attachments - If enabled, any messages with an attachment that is considered dangerous or otherwise unwanted will be rejected
This restriction applies to Outbound messages only, to apply this restriction for Inbound mail, see Manage Attachment Restrictions.
- Reject messages from newly registered domains - (if available) If set, then any message sent from a domain that is newly registered (less than a day) will be rejected
- Re-authenticate permitted - If enabled, authorized servers will be able to relay email on behalf of this user
- Click Save when finished
The Outgoing User Settings page is displayed:
The Outgoing User Settings page is displayed:
The Outgoing User Settings page is displayed: