Single Sign-On in Management Console Beta Dashboard
The Single Sign-On service allows users to access our supported products through a single login.
Single Sign-On
After registering the user's credentials with the Single Sign-On service, these are then used to access all our supported products.
Single Sign-On has the following benefits:
- Provides the user with full control over their login
- Makes logging into multiple products easier
- Improves security - login credentials are only entered once in the service, which leads to reduced exposure of login details
- Makes it easier to apply the company’s login policy as there is only one login to manage
- Simplifies switching between products through the Navigator bar
- Increases productivity as users spend less time attempting to login
- Helps reduce administrative burden of dealing with lost credential requests
- Encourages the use of more complex passwords as there is only one login to remember
Single Sign-on utilizes the leading industry standard for cross-platform authentication. All login requests pass through HTTPS using this protocol.
SAML authentication is not currently supported with our Single Sign-On.
Console Update
After migration the Backup Console includes further user options when clicking on the username in the upper right corner. From here the user can change their details, reset their password and enable Two-Factor Authentication.
Email Address Credentials
Before the release of Single Sign-On, supported logins used usernames or email addresses.
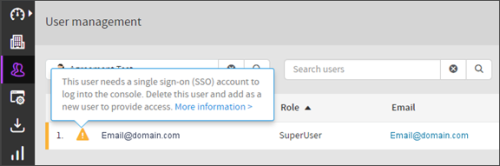
Once migrated, users need active email address credentials to access the Backup Console.
Where users do not use an email-based login, a prompt will prompt them to correct their credentials and change their username to an email address
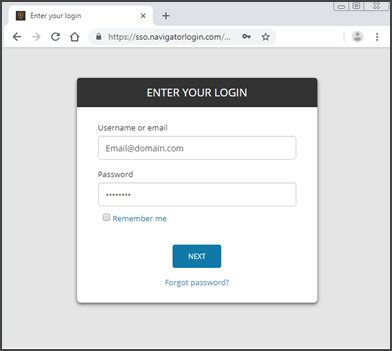
Single Sign-On URL Access https://sso.navigatorlogin.com
After migration, users are re-directed to the Single Sign-On service login page at https://sso.navigatorlogin.com. This will authenticate their credentials when logging into the Backup Console.
If experiencing problems reaching this page, it may be necessary to add navigatorlogin.com to the white-list on any Firewall or content filtering to ensure you can maintain Backup Console access.
You cannot use https://sso.navigatorlogin.com to directly access the Backup Console
Duplicate Email Addresses
Username email addresses must be unique and only associated with one backup partner
If linked to more than one customer account, the user will receive a notification in the console to remove the non-unique email address from the other accounts.
When identifying duplicate accounts, the migration will take the active email account with the highest security level to the Single Sign-On service. The duplicate logins are converted to Integration Users and cannot log into the Backup Console. Integration Users can only access the legacy Cloud Management Console (CMC), API services or Storage Nodes.

Existing Single Sign-On users
The user may receive a message that their email address already exists in the Single Sign-On server. This can occur where the email address is also in use as a login for one of our other SSO utilizing MSP solutions (including N-able Remote Monitoring & Management and N-able MSP Manager).
To access the Backup Console post-migration the user simply enters their existing Single Sign-On username and password at the Single Sign-On login page.
If the user experiences problems with their Single Sign-On password, they can use the “Forgot Password” link on the login page to receive a reset email.
Two-Factor Authentication
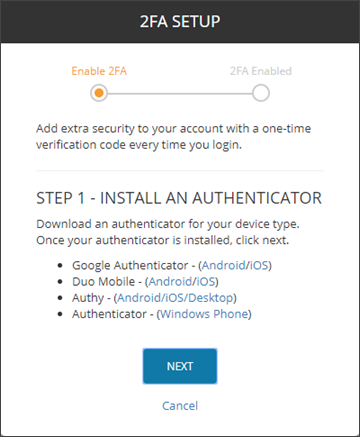
The Single Sign-On Service utilizes a Two-Factor Authentication (2FA) mechanism. This is a mandatory security measure and cannot be disabled.
Single Sign-on does not support the DoubleChecked app for 2FA. To continue using 2FA after migration, you must setup 2FA on the Single Sign-On server for the email-based login.
2FA for new SSO logins will prevent these credentials from working with the legacy Cloud Management Console (CMC), API services or Storage Nodes.
During the 2FA setup phase, you will be provided with a Recovery Key - keep this in a secure location. Should you need to reset 2FA due to no longer having access to your used Authenticator tool, you will require this Recovery Key.
Resetting 2FA
If you no longer have access to the Authenticator to gain the 2FA code, due to a replaced phone for example, you will need to reset your 2FA. To do so, you require the Recovery Key gained at the point 2FA was configured.
To reset your 2FA:
Log into Backup as per normal, when presented with the prompt for your 2FA code, click the Reset your two-factor authentication? link
Enter your Recovery Key and click Disable 2FA
You are now prompted to select either Continue to product or Two-Factor Setup - in either case you will be prompted to configure 2FA before being able to access the Backup dashboard
Software Only Partners
Those hosting their own storage nodes must run the Storage Node Installer before and after migration. They must use email-based credentials and update these with a valid password.
We recommend creating a unique SuperUser for exclusive use in Storage Node authentication.
Storage Nodes do not support login email credentials linked to 2FA
Failure to confirm or update the storage node credentials can result in missed backups
If experiencing any issues identifying or correcting accounts or have any other issues after migration, please open a support case.