View Conditional Access policies
Cloud Commander will be decommissioned and stop functioning on May 13, 2026. You can use the product until that date.
Review and update workflows to remove any dependencies before the product is decommissioned.
Support, bug fixes, and security patches will be available until April 13, 2026.
The Tenant Security page lists all your managed tenants, including tenant ID, number of users, and number of Conditional Access policies. You can view the list of Conditional Access policies for each tenant and drill down to see an overview of the policy settings, as well as a breakdown of the asset types included and excluded from the policy scope.
- View the Conditional Access policies for each tenant
- Drill down to view policy settings
- Drill down to view policy scopes
What is Conditional Access?
Microsoft Entra Conditional Access analyzes signals, such as user, device, and location, to automate decisions and enforce organizational access to resources. You can use Conditional Access policies to apply access controls like multi-factor authentication. These policies prompt users for multi-factor authentication when needed for security and stay out of users’ way when not needed. Conditional Access policies control and protect Microsoft 365 tenants, acting like a firewall with rules to grant or deny access. You can customize security defaults with more granularity, configure new policies that meet your requirements, and move toward a zero-trust environment.
Administrators implement Conditional Access using policies that are if-then statements of Assignments and Access controls that enforce organizational policies.
- Assignments: When configuring Conditional Access policies, you set conditions called Assignments. Assignments define the users and groups affected by the policy, the cloud apps or actions to which the policy applies, and the conditions under which the policy applies.
- Access control settings: These settings grant or block access to different cloud apps and can enable limited experiences within specific cloud apps.
For more information about Microsoft Entra Conditional Access, see Microsoft documentation: What is Conditional Access?
Benefits of viewing Conditional Access policies in Cloud Commander
Managing Conditional Access policies individually for each tenant is time-consuming and prone to errors. By viewing Conditional Access policies in Cloud Commander, you can streamline your security operations, ensure uniform policy enforcement, and quickly respond to potential threats, thereby enhancing overall security and operational efficiency.
In this first phase of our Conditional Access policies feature, you can view the list of Conditional Access policies for each tenant and drill down to see an overview of the policy settings, as well as a breakdown of the asset types included and excluded from the policy scope.
Prerequisites
- You must be assigned the Administrators role to view Tenant Security in the .
- You must be assigned the Identity Protection Reader role scoped to a tenant to view their Conditional Access policies.
- The Conditional Access feature must be licensed for the tenant. See Microsoft documentation: License requirements.
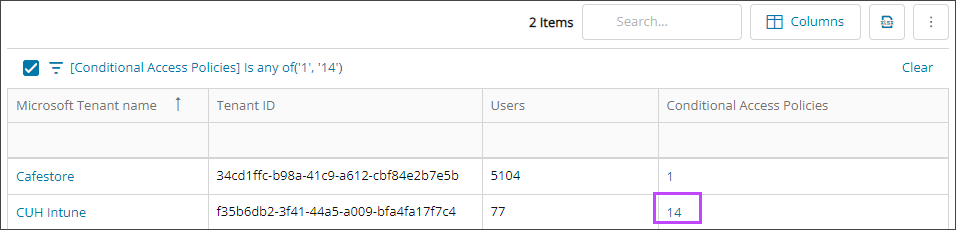
View the Conditional Access policies for each tenant
- In the , select
 Security > Tenant Security.
Security > Tenant Security. - For the tenant you need, select its number of Conditional Access Policies to view the policies for that tenant.
If you are not assigned the Administrators role for a tenant, the Conditional Access Policies column will not display a link with the number of policies for that tenant.
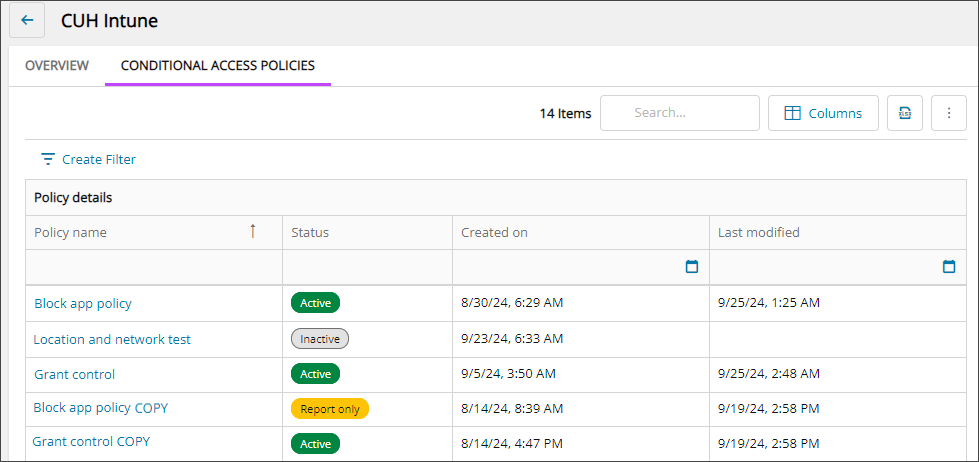
The Conditional Access Policies tab displays a list of policies with summary data for the tenant. Use the Column Chooser to select the data you want to see.
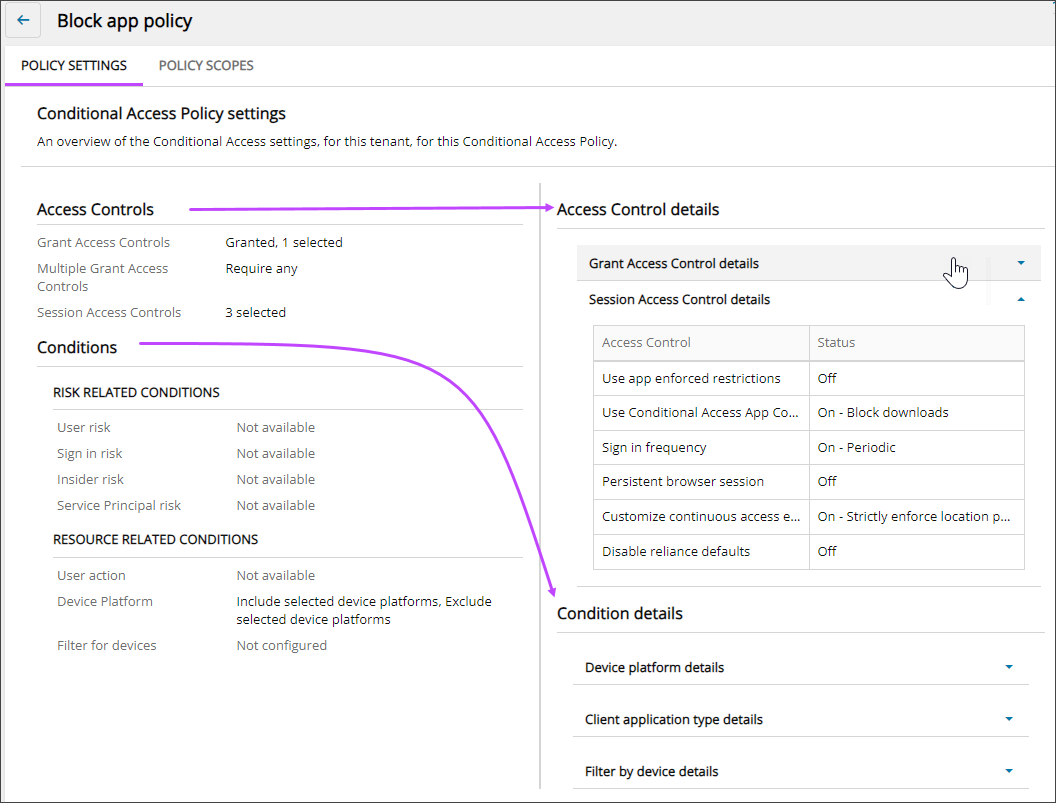
Drill down to view policy settings
- On the Conditional Access Policies tab, select the name of a policy to view its details.
The Policy Settings tab displays.
- The core policy settings display on the left with more detailed data on the right. Click a row heading on the right to view or hide data on the right.
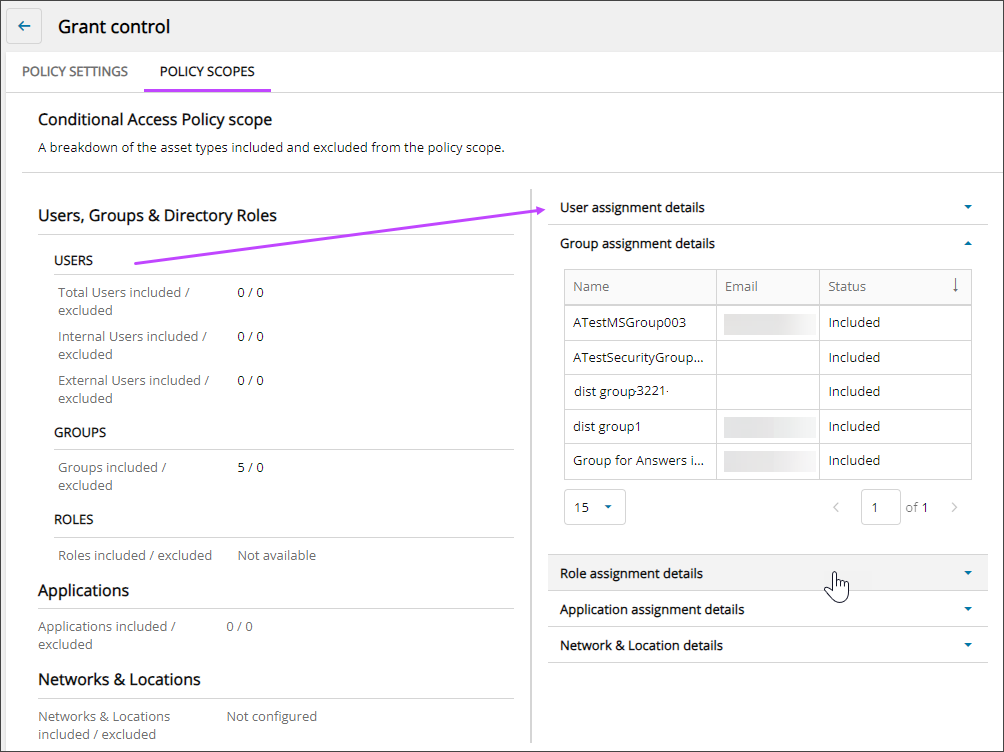
Drill down to view policy scopes
- On the Conditional Access Policies tab, select the name of a policy to view its details.
- Select Policy Scopes.
The Policy Scopes tab displays.
- The core policy settings display on the left with more detailed data on the right. Click a row heading on the right to view or hide data on the right.
Related articles
- Tenant security
- Microsoft documentation: What is Conditional Access?
- Microsoft documentation: Building a Conditional Access policy
Updated: Jan 09, 2026