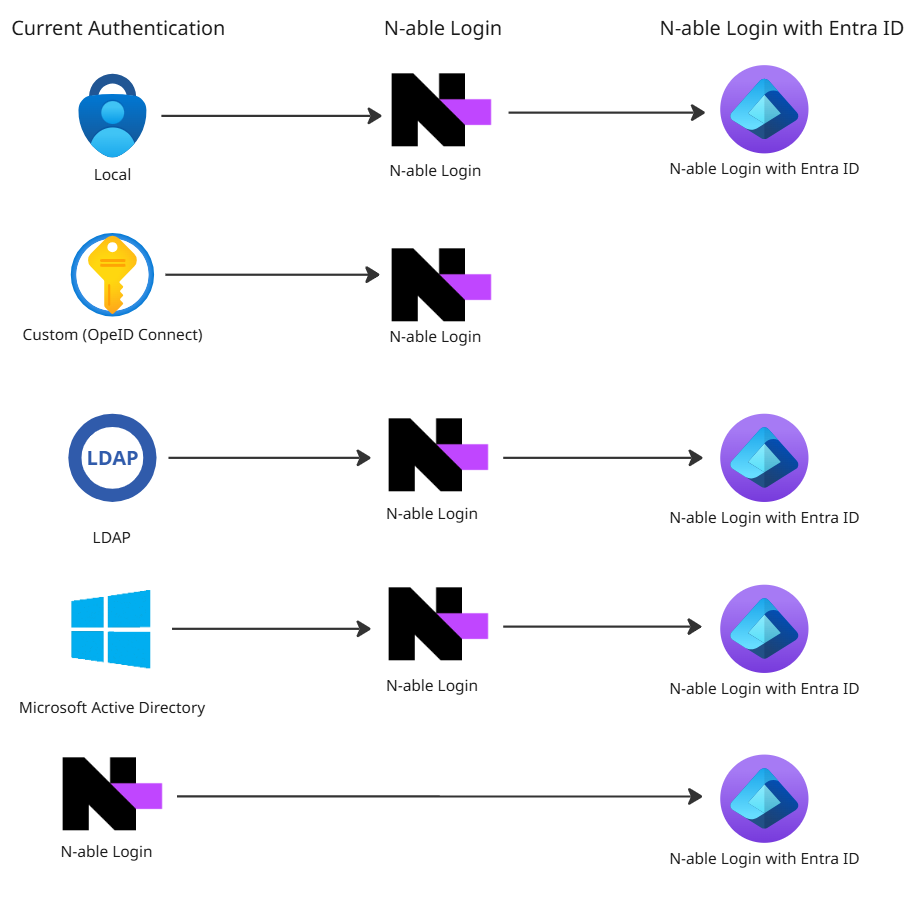
Move to N-able Login (with Entra ID)
N-central provides several authentication methods to control user access, but the most secure and scalable path forward is moving to federated authentication with N-able Login and Microsoft Entra ID (formerly Azure AD). Whether you're setting up for the first time or moving from a legacy configuration, this is your path to enabling Single Sign-On (SSO) and centralized user management through Microsoft Entra ID.
Why move to N-able Login with Entra ID
Current IT environments require centralized identity management and seamless Single Sign-On (SSO).
N-able Login with Entra ID offers a direct integration with Microsoft Entra ID, enabling users to access N-central with their existing Microsoft credentials. Moving to this authentication path reduces administrative overhead, simplifies user onboarding, and enhances security through federated access control. For organizations already using Microsoft Entra ID, this is the most efficient and secure way to manage user authentication in N-central.
Why move to N-able Login with Entra ID
Current IT environments require centralized identity management and seamless Single Sign-On (SSO). N-able Login with Entra ID offers a direct integration with Microsoft Entra ID, enabling users to access N-central with their existing Microsoft credentials. Moving to this authentication path reduces administrative overhead, simplifies user onboarding, and enhances security through federated access control. For organizations already using Microsoft Entra ID, this is the most efficient and secure way to manage user authentication in N-central.
Visit N-able Login and N-able Login with Entra ID for more detailed setup and configuration information.
Path 1: Local N-central Users
You currently use user accounts created directly in N-central, without external identity providers or directory services. This path is ideal for environments that prioritize simplicity or operate in isolated or highly controlled networks.
Path
-
Enable N-able Login in N-central
-
Navigate to Administration > User Management > Authentication Settings.
-
Select N-able Login as the preferred authentication method.
-
This enables a secure, cloud-based identity layer that supports MFA and aligns with the N-able long-term identity strategy.
-
-
Review and Migrate Local Users
-
Audit existing local user accounts and roles.
-
Recreate or migrate these users into the N-able Login system.
-
Assign appropriate roles and permissions to maintain continuity of access.
-
-
(Optional) Configure Entra ID Federation
-
If you plan to centralize identity management or enable SSO, register N-able as an app in Microsoft Entra ID.
-
Configure redirect URIs and claims mapping to support role-based access control.
-
This step is optional but recommended for organizations already using Entra ID.
-
-
Test Authentication and Role Mapping
-
Validate login flows for migrated users.
-
Confirm that role mappings from Entra ID (if configured) align with N-central’s role-based access model.
-
Use test accounts to simulate various access scenarios before full rollout.
-
-
Decommission Legacy Local Accounts (Optional)
-
Once all users are successfully transitioned, consider disabling or removing legacy local accounts to reduce attack surface and simplify management.
-
Path 2: LDAP/Active Directory (On-Prem)
You use on-premises Active Directory (AD) via LDAP authentication in N-central. This path transitions your environment to N-able Login with optional federation to Microsoft Entra ID for centralised identity management.
Transition Path
-
Review Current AD/LDAP User Roles
-
Audit existing LDAP-linked user accounts and their assigned roles in N-central.
-
Document group memberships and role mappings to ensure continuity during migration.
-
-
Enable N-able Login in N-central
-
Go to Administration > User Management > Authentication Settings.
-
Select N-able Login as the preferred method.
-
This step introduces MFA and cloud-based identity controls.
-
-
Register N-central as an OIDC App in Entra ID
-
In Microsoft Entra Admin Center, create a new enterprise application.
-
Configure OpenID Connect (OIDC) settings including redirect URIs and scopes.
-
Ensure the app is assigned to appropriate user groups.
-
-
Map Entra ID Group Claims to Roles in N-central
-
Use group claims from Entra ID to define role-based access in N-central.
-
Validate that each group maps correctly to the intended permissions.
-
-
Test Authentication and Role Mapping
-
Use test accounts to verify login flows and role assignments.
-
Confirm fallback mechanisms for users not yet migrated.
-
-
Decommission LDAP Authentication (Optional)
-
Once all users are transitioned, disable LDAP authentication to reduce complexity and improve security posture.
-
Path 3: Already Using N-able Login
You’re already using N-able Login for authentication but haven’t yet federated with Microsoft Entra ID. This path enables full SSO and centralised identity control.
Transition Path
-
Register N-central as an OIDC App in Entra ID
-
In Microsoft Entra Admin Center, create a new app registration.
-
Configure redirect URIs, scopes, and claims to support role mapping.
-
-
Configure Claims and Redirect URIs
-
Ensure group claims are included in the token.
-
Set up redirect URIs to point to your N-central instance.
-
-
Enter OIDC Settings in N-central
-
Navigate to Authentication Settings in N-central.
-
Input the client ID, secret, issuer URL, and other OIDC parameters.
-
-
Test Login and Role Mapping via Entra ID
-
Validate that users can log in using Entra ID credentials.
-
Confirm that group-based roles are correctly applied.
-
-
Monitor and Optimize
-
Review login logs and user activity.
-
Adjust group mappings and claims as needed for scalability.
-
Benefits of Transitioning to N-able Login and N-able Login with Entra ID
Whether you're enabling N-able Login on its own or integrating it with Microsoft Entra ID for federated authentication, the transition offers a unified set of strategic benefits:
Security Enhancements
-
Introduces modern authentication protocols including Multi-Factor Authentication (MFA), reducing reliance on legacy credentials.
-
(Entra ID) Enables conditional access policies, risk-based sign-in protection, and integration with Microsoft’s broader security ecosystem.
Centralized Identity Management
-
Consolidates user roles and access control within N-central, streamlining administration.
-
(Entra ID) Extends identity lifecycle management through Entra ID.
Improved User Experience
-
Provides a consistent login experience across N-able products.
-
(Entra ID) Enables Single Sign-On (SSO) across N-central and other Microsoft 365 or enterprise applications, reducing password fatigue and improving productivity.
Audit and Compliance Readiness
-
Enhances visibility into authentication events and user activity for internal audits.
-
(Entra ID) Leverages Microsoft’s logging and reporting tools for deeper compliance insights and integration with SIEM platforms.
Scalability and Role Management
-
Supports role-based access control directly within N-central.
-
(Entra ID) Allows dynamic role assignment via group claims, simplifying access control in large or complex environments.
Future-Ready Architecture
-
Aligns with the N-able long-term identity and access strategy, providing access to current and future functionality, for example Ecoverse views.
-
(Entra ID) Positions your environment for full participation in the N-able Ecoverse vision and future integrations with Microsoft identity services.