View and filter by patch CVSS scores
The Common Vulnerability Scoring System (CVSS) provides a standardized and consistent way to assess and communicate the severity of vulnerabilities. By bringing information from Microsoft’s Security and Response Center in Patch Management you can clearly see which patches are solving vulnerabilities, allowing you to focus on those when needed.
In N-able N-central, you can:
- View a patch's base CVSS score
-
Filter by base CVSS scores
-
View CVE IDs
CVSS scores are only available for Microsoft patches.
View CVSS score
To view the base CVSS scores of a patch:
-
In the left-hand navigation menu, click Actions > Patch Approvals > By Patch.
-
Next to the desired patch, locate the CVSS score under the CVSS column.
This number is the highest CVSS score of the patch fixes.
-
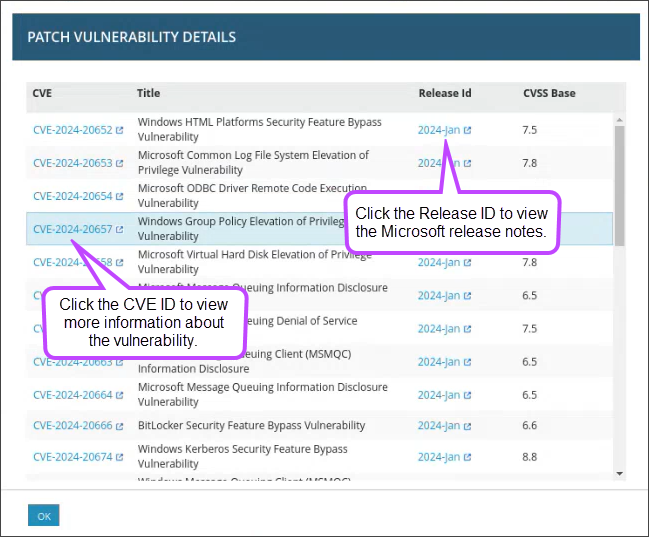
Click the CVSS score to open up the Patch Vulnerability Details dialog, which allows you to see all the CVSS scores for the patch and the CVE IDs.
You can click on the Release ID next to a CVSS score to view the corresponding Microsoft release notes or click the CVE ID to navigate to Microsoft's website for more information about the vulnerability.
Filter by CVSS score
To filter by base CVSS scores:
-
In the left-hand navigation menu, click Actions > Patch Approvals > By Patch.
-
Click Show Filter on the right.
-
Under CVSS Score Qualitative Rating, select to filter by the available ranges.
-
0.0 - None
-
0.1 - 3.9 - Low
-
4.0 - 6.9 - Medium
-
7.0 - 8.9 - High
-
9.0 - 10.0 - Critical
CVSS Score Name CVSS Score Range Color None 0.0 Low 0.1 - 3.9 Medium 4.0 - 6.9 High 7.0 - 8.9 Critical 9.0 - 10.0 -
The patch view automatically changes to show the desired patches.
View CVE IDs
To view the CVE IDs for a patch:
-
In the left-hand navigation menu, click Actions > Patch Approvals > By Patch.
-
Next to the desired patch, locate the CVSS score under the CVSS column.
-
Click the CVSS score.
-
In the Patch Vulnerability Details view, locate the CVE IDs under the CVE column.
Click the CVE ID to navigate to Microsoft's website for more information about the vulnerability.