Remote Control
A key feature of N-able N-central is the ability to remotely control any managed device, regardless of the user's location on the Internet. Remote control in N-able N-central leverages the location of the N-able N-central server on the Internet and the outbound communications model provided by Agents and Probes.
Remote Control is available on N-able N-central servers with a Professional license.
N-able N-central uses the following methods to establish encrypted connections from the N-able N-central server to the remote control target device:
-
Other remote control types use connections established through one of SSH (Secure Shell) or HTTPS (Hypertext Transfer Protocol, Secure).
Security scans performed on N-central servers may, in some cases, report vulnerabilities related to SSH based on the version string. Because the SSH version string represents a truncated, high-level value, it may not accurately reflect the presence of known vulnerabilities. Before investigating further, organizations should verify whether the reported issues have already been addressed in the specific build of OpenSSH included with the server.
Accessing a remote device requires a username and password, regardless of the protocol used.
Take Control
Take Control sessions use a proprietary communication protocol with guaranteed global security, AES 256-bit encryption during session establishment and throughout the session. Key exchange is protected by SSL based on AES-CBC with TLS 1.2. All commands, including keyboard and mouse strokes, file transfers and clipboard data are digitally signed.
Take Control does not access session content. Encryption is based on end-to-end negotiation that does not intercept or decode the transferred information or the information in the gateway. Encryption keys are randomly generated for each session.
As an additional security measure, the client can configure authentication using a Master Password or Windows account and enable pre-authorization by the machine owner before launching a session.
Finally, all major features, including remote control, file transfer and chat conversations are logged in the session details and can be recorded as video.
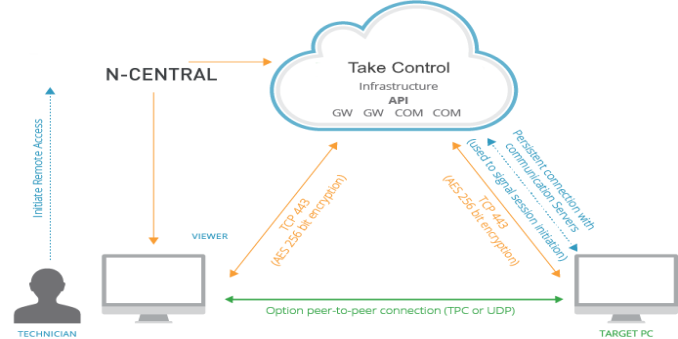
Take Control traffic is secured using multi-layer authentication. Elliptic-curve Diffie-Hellman is implemented to protect our public/private key exchanges, a component step in session instantiation. All commands, including keyboard and mouse strokes, file transfers and clipboard information are digitally signed.
Take Control does not have access to session content. All encryption is based on an end-to-end negotiation that does not intercept transferred information or decode the information in the gateway. Encryption keys are randomly generated for each session.
Take Control uses servers located in large data centers around the world, and a geolocation method ensures the geographically nearest router is always used for the connection.
As public IP Addresses are dynamically assigned (outside of N-able's control) and, as internal infrastructure changes (dynamic or effective), these public IP addresses are required to manage the infrastructure (within N-able's control). No IP Address lists or ranges can be provided, guaranteeing that they will not eventually become invalid.
Allow Outbound Network Traffic
Outbound network traffic must be allowed on both the Take Control Viewer and Agent sides for the following domains, over TCP Port 443 (https):
- swi-rc.cdn-sw.net
- *.n-able.com
- *.mspa.n-able.com
- *global.mspa.n-able.com
- *.us1.mspa.n-able.com
- *.us2.mspa.n-able.com
- *.eu1.mspa.n-able.com
Almost all of the above Firewall Rules require the use of wildcard exclusions, which are not supported by some vendors. As an alternative, the Firewall Rules can be configured as follows:
- Allow outbound communications to any IP Addresses over TCP Port 3377 (used to communicate with the Take Control Gateways).
- Allow outbound communication over TCP Port 443 (https) for the following URLs:
- swi-rc.cdn-sw.net
- comserver.global.mspa.n-able.com
- comserver.us1.mspa.n-able.com
- comserver.us2.mspa.n-able.com
- comserver.eu1.mspa.n-able.com
- comserver-hb-eu1-fra.n-able.com
- comserver-hb-eu1-iad1.n-able.com
- comserver-hb-us0-iad1.n-able.com
- comserver-hb-us0-lax.n-able.com
- comserver-hb-us1-iad2.n-able.com
- comserver-hb-us1-lax.n-able.com
- comserver-hb-us2-lax.n-able.com
- comserver-hb-us2-iad2.n-able.com
Outbound network traffic must be allowed on both the Take Control Viewer and Agent sides for the following domains, over TCP Ports 80 (http) and 443 (https):
- *.mspa.n-able.com
- *.swi-rc.cdn-sw.net
The Take Control Firewall requires the use of wildcard exceptions, which are not configurable on some legacy Network equipment. As an alternative, use fail over TCP Port 3377, which can be configured as follows:
- Allow outbound communications to any IP Addresses over TCP Port 3377.
- Allow outbound communication over TCP Ports 80(http) and 443 (https) for the following URLs:
- comserver.us0.swi-rc.com
- comserver.us3.swi-rc.com
- comserver.eu2.swi-rc.com
Ports and URLs
To avoid potential communication or connection problems to these global servers, we recommend you allow the following Ports and URLs in your firewall or web-monitoring software:
Ports
- 80 (TCP)
- 443 (TCP)
- 3377 (TCP) - used as a fall over if 443 is unsuccessful
URLs
- *.mspa.n-able.com
- *.swi-rc.cdn-sw.net
Services and Processes (Windows only)
Take Control includes the following executables that run continuously or for the duration of a single session:
Continuously running executables
| Executable | Type | Description |
|---|---|---|
| BASupSrvc.exe | Service | Allows remote sessions and maintains communication to the All Devices view and infrastructure |
| BASupSrvcUpdater.exe | Service | Updates the BASupSrv service when required and ensures it is always running |
| BASupSrvcCnfg.exe | Process (Normal) |
Allows in-session chats between the technician and the user, and also displays the session authorization pop-ups. This process is loaded for each user logged on to the machine and multiple instances can exist at the same time.
If the session is killed, in-session chats are not available and session authorization pop-ups do not display to the local user (the default action defined will occur after a timeout period). |
Single session executables
| Executable | Type | Description |
|---|---|---|
| BASupTSHelper.exe | Process (Elevated) | Permits image capturing during the remote session |
| BASupSrvcEvnt.dll | DLL | Registers Take Control related Events that display in the device's Event Viewer. To ensure Take Control is reported as the Event source, the .dll remains on the device after Take Control is uninstalled. |
Remote Desktop
Remote Desktop uses a Custom Protocol Handler (CPH) to facilitate the connection to an RDP session. When launching a RDP session, N-able N-central will verify if the CPH application is installed on the host device. If the system does not detect CPH, it prompts the user to download and install the application.
The handler will attempt to use a tunnel over SSH for the connection before failing over to HTTPS (443) to establish the connection. The CPH launcher opens a listening port randomly selected by N-central to start the RDP client.
No CPH for Mac and Linux
Mac and Linux devices still use the Java implementation for Remote Desktop. SSH and webpage require Java to run.
To manage devices from a Mac or Linux technician system, use browser-based remote control if the endpoint supports it.
Launch remote sessions from a Windows-based technician machine or VM to leverage CPH.
Other Remote Control Connections
For remote control types other than Take Control, the first protocol attempted will be an SSH tunnel (TCP on port 22 to N-central). Should the SSH connection attempt fail, the requesting user and the target system will again attempt to connect to each other through the N-able N-central server using HTTPS on port 443.
| Port Number | Port Location | |||
|---|---|---|---|---|
| N-able N-central Server | Target Device | |||
| Inbound | Outbound | Inbound | Outbound | |
|
Port 22 |
Ö | Ö | Ö | |
|
Port 443 |
Ö | Ö | Ö | |
After the requesting user and the target system are connected, the remote control tools can then communicate over this encrypted connection as if they were located on the same network subnet. Since the remote control sessions originate outbound from the user’s system, as well as from the device to be remotely controlled, there is no requirement for a public IP address, or inbound port forward for this remote control tool to work.
In the diagrams below, the "SSH Tunnel*" notation indicates the first protocol attempted will be an SSH tunnel (TCP on port 22).
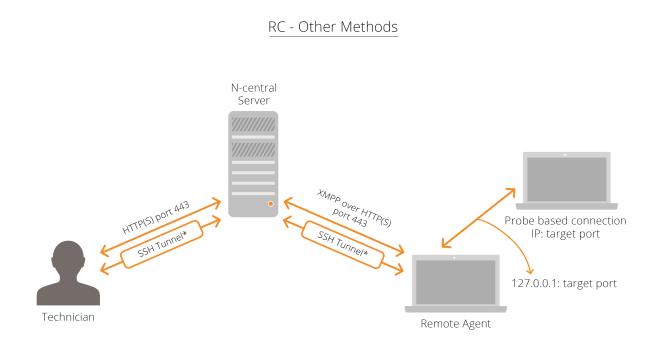
Remote control in N-able N-central uses several layers of security. The outbound request model ensures that there are no inbound reports required.
Data passed through SSH connections is encrypted using 128-bit AES-based encryption keys.
Data is passed through HTTPS connections in combination with SSL and TLS. SSL and TLS are cryptographic protocols that provide secure communications on the Internet. HTTPS is designed for secure encrypted communication between different devices as well as secure identification and authentication of the remote device.
