Local agent
N-able N-central agents monitor the devices that they have been installed on, and report data about the device to the N-able N-central server. To monitor devices where an agent cannot be installed, N-able N-central relies on probes. N-able N-central agents are available for devices with variants of the following operating systems:
- Windows
- macOS
- Red Hat, CentOS and Ubuntu Linux
Local agent properties
| INSTALLATION AND UPGRADE DETAILS | |
|
Install Local Agent |
Select this option to install an agent on the device. |
|
Activation Key |
N-able N-central generates an agent activation key when you install the agent software on the device. |
|
Agent Installer |
The file name (and a hyperlink) of the software application to install the appropriate agent type on the device. |
|
Installed Agent version |
The version of the agent currently installed on the device. |
|
Agent Update Available |
Indicates whether or not an updated version of the agent is available to be installed. |
|
Log |
The file name (and a hyperlink) of the agent's log file. |
|
Update New Version |
Select how the agent will be updated to the newest version. |
|
Status |
The current status of any Agent installation operations. The installation status is only available for Windows Agents. N-able N-central attempts to install the agent every six hours for a total of 12 times in 72 hours. After 12 attempts, the installation status is indicated as Failed and a Retry button becomes available. |
| CONFIGURATION DETAILS | |
|
Update Monitored Address |
Select to update the network address when the device's local IP address changes based on data gathered by the agent. For this feature to work properly, the Local IP service must first be applied to the device. |
|
Log Level |
The amount of detail that the Agent is to record in the log file as one of the following:
|
|
Appliance ID |
A read-only value that displays the appliance ID generated by N-able N-central for the agent. This is used for troubleshooting purposes. |
| COMMUNICATION SETTINGS | |
|
Protocol |
The protocol (either HTTP or HTTPS) that the agent must use to communicate with the N-able N-central server. |
|
Server Address |
The IP address or FQDN to be used to establish a connection to the N-able N-central server. If a connection cannot be established with the first address provided, additional addresses can be configured to provide fail-over functionality.
To remove an IP address or FQDN:
You can select the check box next to the Server Address column heading to select all of the addresses. Notes:
|
|
Port Number |
The port that the agent uses to establish a connection to the N-able N-central server. In typical configurations, the port value is 80 for an HTTP protocol and 443 for an HTTPS protocol except when the N-able N-central server is behind a port-forwarder. |
|
Proxy String |
Type a valid network address. Both authenticating and non-authenticating proxies are supported. For authenticating proxies, the following are examples of proxy strings:
For not-authenticating proxies, the following are examples of proxy strings:
|
|
Capture Agent Logs |
Click Capture Logs to retrieve agent logs. The logs are compressed into a .ZIP file to be downloaded. Depending on their size and number, retrieval of Agent logs may take up to five minutes. |
| ASSET SCAN | |
|
Perform Asset Scan |
Select this option to configure the settings for an asset discovery scan, if required |
|
Asset Scan Schedule |
Select the Start Time, Days of the Week, and, Days of the Month when you would like the asset discovery scan to be performed. |
|
MONITORING DATA PERSISTENCE (see Data Persistence below for additional details) |
|
|
Drop Policy |
Select the criteria to indicate when the data window has been exceeded from one of the following:
|
|
Data Window |
Select the maximum span (in hours and minutes) of data to be cached on the agent. If the span is exceeded, the data that is discarded depends on the drop policy. For example, if you specify two hours and the drop policy is configured as Newest, any new data will be discarded after more than two hours of data has been cached. The local time is used to cache data and determine the expired data span. |
|
Minimum Free Disk Space |
Select the minimum amount of disk space (in MBs, GBs, TBs, or %) required to be available on the Agent before data can be cached. |
|
Maximum Disk Space |
Select the maximum amount of disk space (in MBs, GBs, TBs, or %) on the Agent that can be used for caching data. |
Data Persistence
When setting up a Windows, Linux, or macOS agent, you can also set the agent's data persistence settings. This allows the agent to cache data for a specified length of time if the connection to the central server is down. However, data will not be cached if the available disk space on the agent is less than the specified minimum.
If the data being cached begins to exceed the specified length of time or the available disk space, the data is discarded based on the drop policy. The drop policy determines whether the oldest or newest data is discarded. If the drop policy is the oldest, then the oldest record is discarded as each new record is cached. If the drop policy is the newest, then any new data is immediately discarded.
During the time that the connection between the agent and central server is down, the statuses for the services being monitored by the agent are displayed as stale. After the connection to the central server is restored, the agent transfers all of the cached data to the central server. The central server compares the most recent information in the cached data to the original data before the connection went down to determine whether the service status has changed. If there is a change, the new service statuses are displayed on the dashboards and the appropriate notifications are triggered.
For example, if the status was green before the connection went down, but red in the last record of the cached data sent to the central server, then in comparing the two, the central server will trigger a notification. Refer to the image below.
Cached Data using Newest Drop Policy
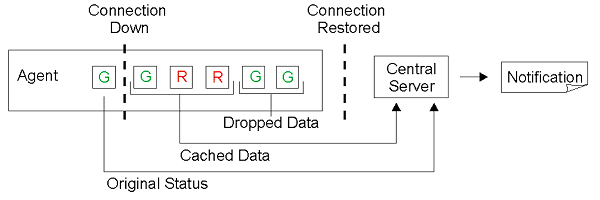
However, if the last record of the cached data sent to the central server is green, then a notification is not triggered. Refer to the image below. The data, however, can still be retrieved through historical reports.
Cached Data using Oldest Drop Policy
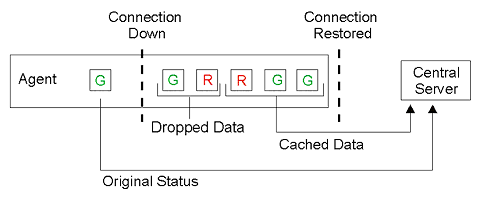
- Click Views > All Devices.
- Select the Network Devices tab.
- Click the Name of a device.
- In the Device Details screen, click Settings.
- Click Local Agent.
- Click Views > All Devices.
- Select the Network Devices tab.
- Click the Name of a device.
- In the Device Details screen, click Settings.
- Click Local Agent.
- Clear the Install Local Agent check box.
- In the Local Agent Removal Confirmation dialog box, review the N-able N-central features that will be removed by uninstalling the agent.
- Click OK then click Save.

 ) beside the new address to edit it.
) beside the new address to edit it.